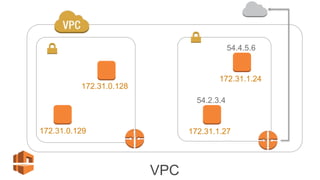
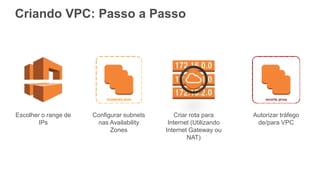
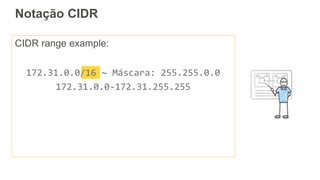
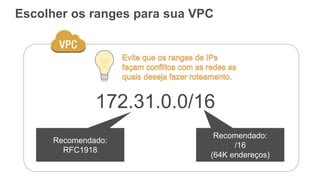
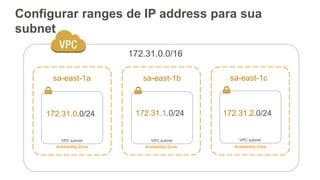
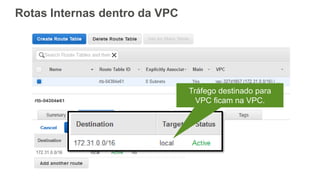
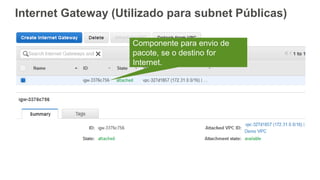
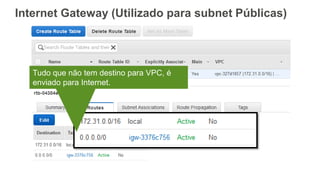
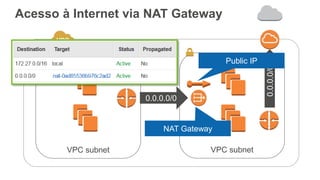
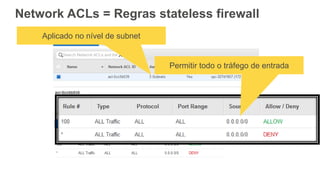
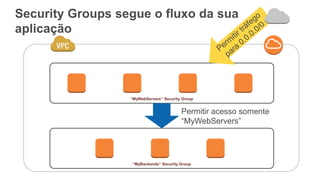
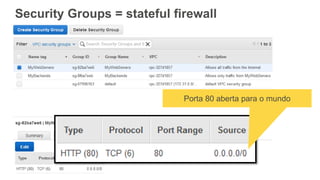
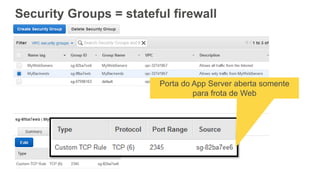
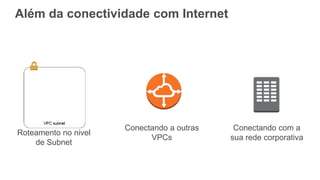
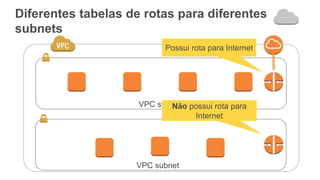
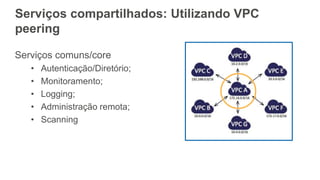
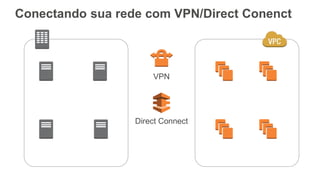
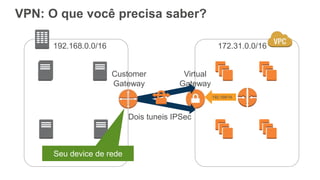
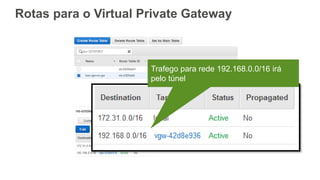
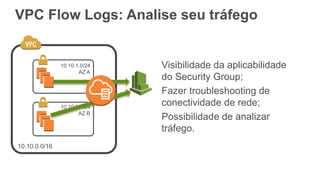
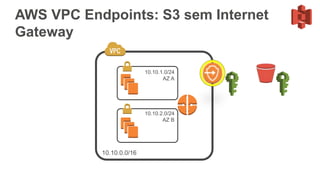
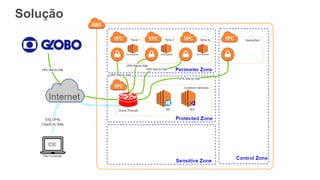
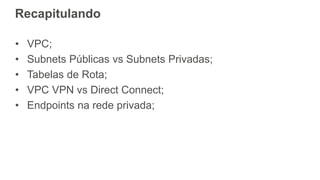
O documento aborda a criação e conectividade de um Data Center Virtual utilizando o Amazon VPC, incluindo conceitos como isolamento de rede, configuração de subnets, tabelas de rotas e conectividade com redes on-premises. Também discute o uso de VPN e Direct Connect para conectar a rede corporativa à VPC, assim como a segurança através de Network ACLs e Security Groups. Por fim, enfatiza a importância de monitorar e gerenciar o tráfego de rede com ferramentas como VPC Flow Logs.