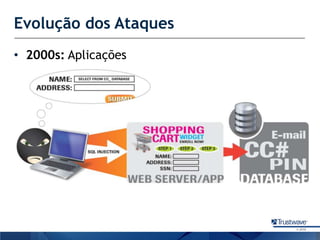
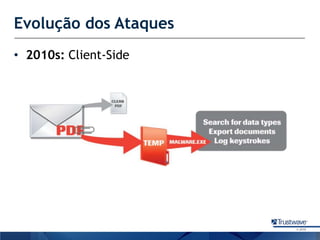
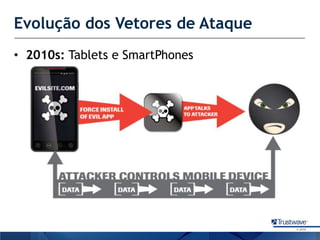
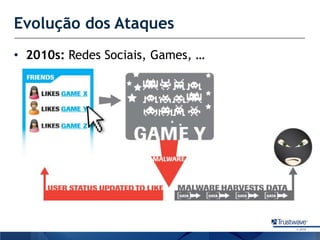
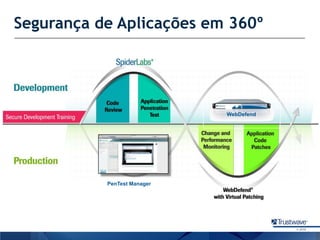
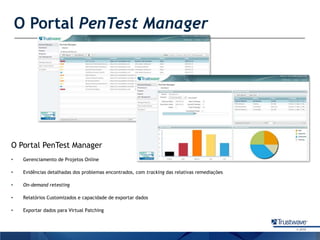
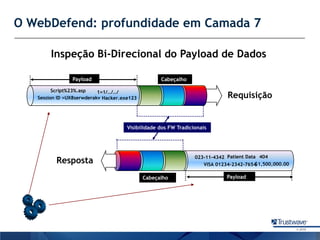
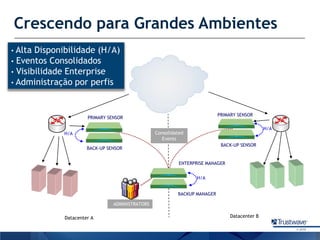
O documento discute como a Trustwave, uma empresa global de segurança cibernética, oferece várias soluções de segurança, incluindo testes de penetração, gerenciamento de vulnerabilidades, firewalls de aplicações web e proteção contra fraudes bancárias. Apresenta também as tendências de ataques cibernéticos ao longo dos anos e como a empresa ajuda clientes a evitar notas falsas em caixas eletrônicos.