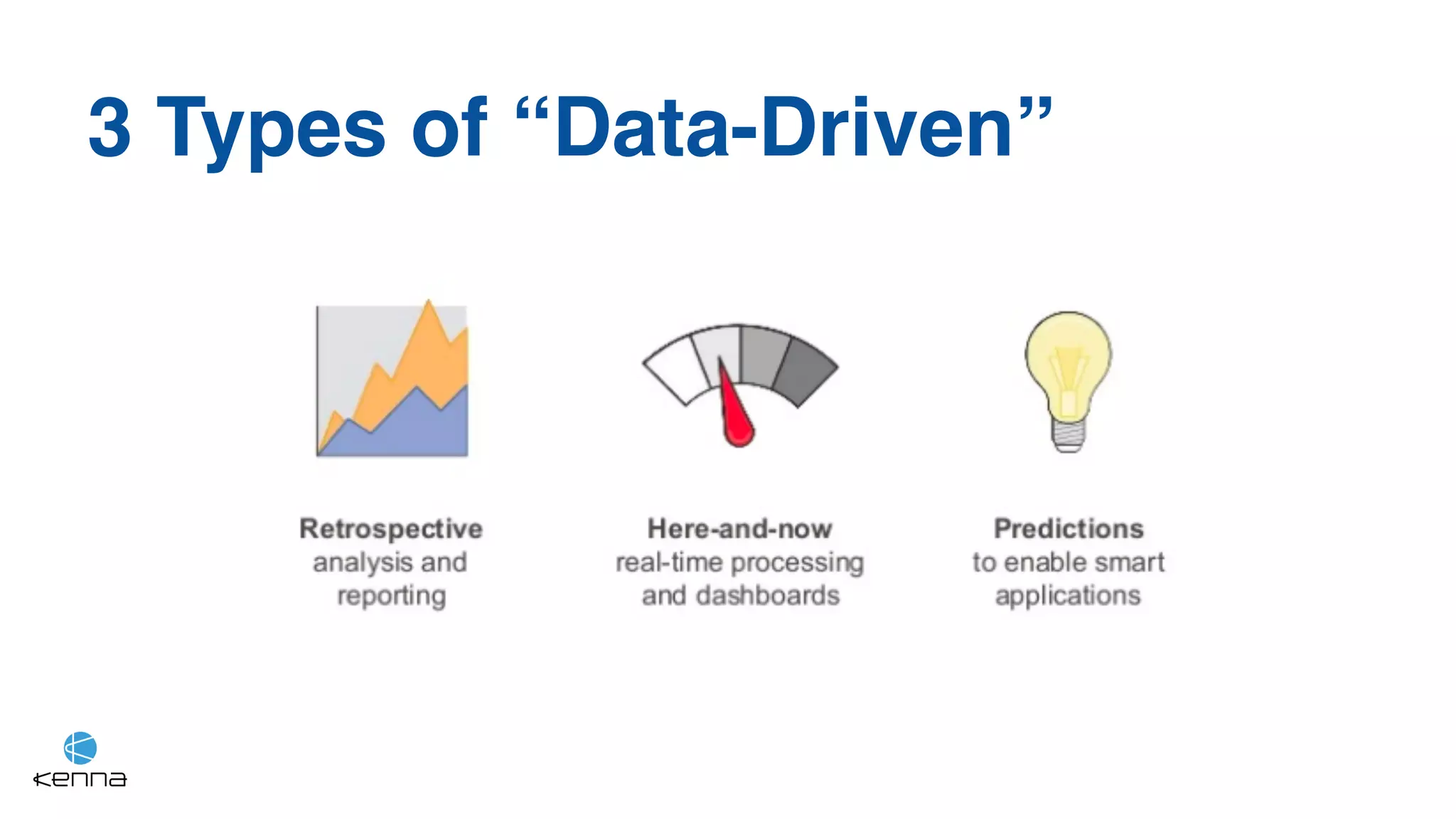
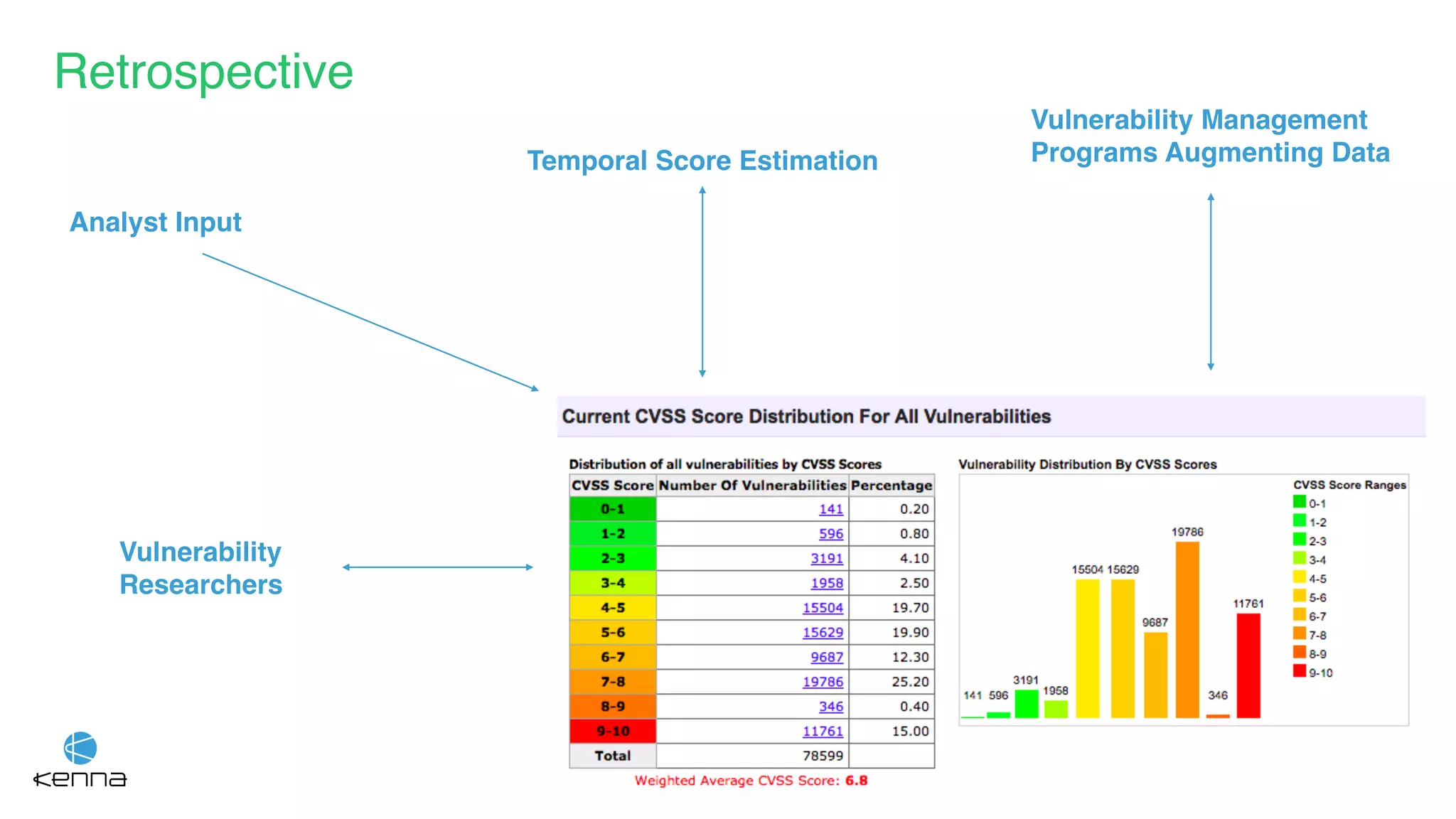
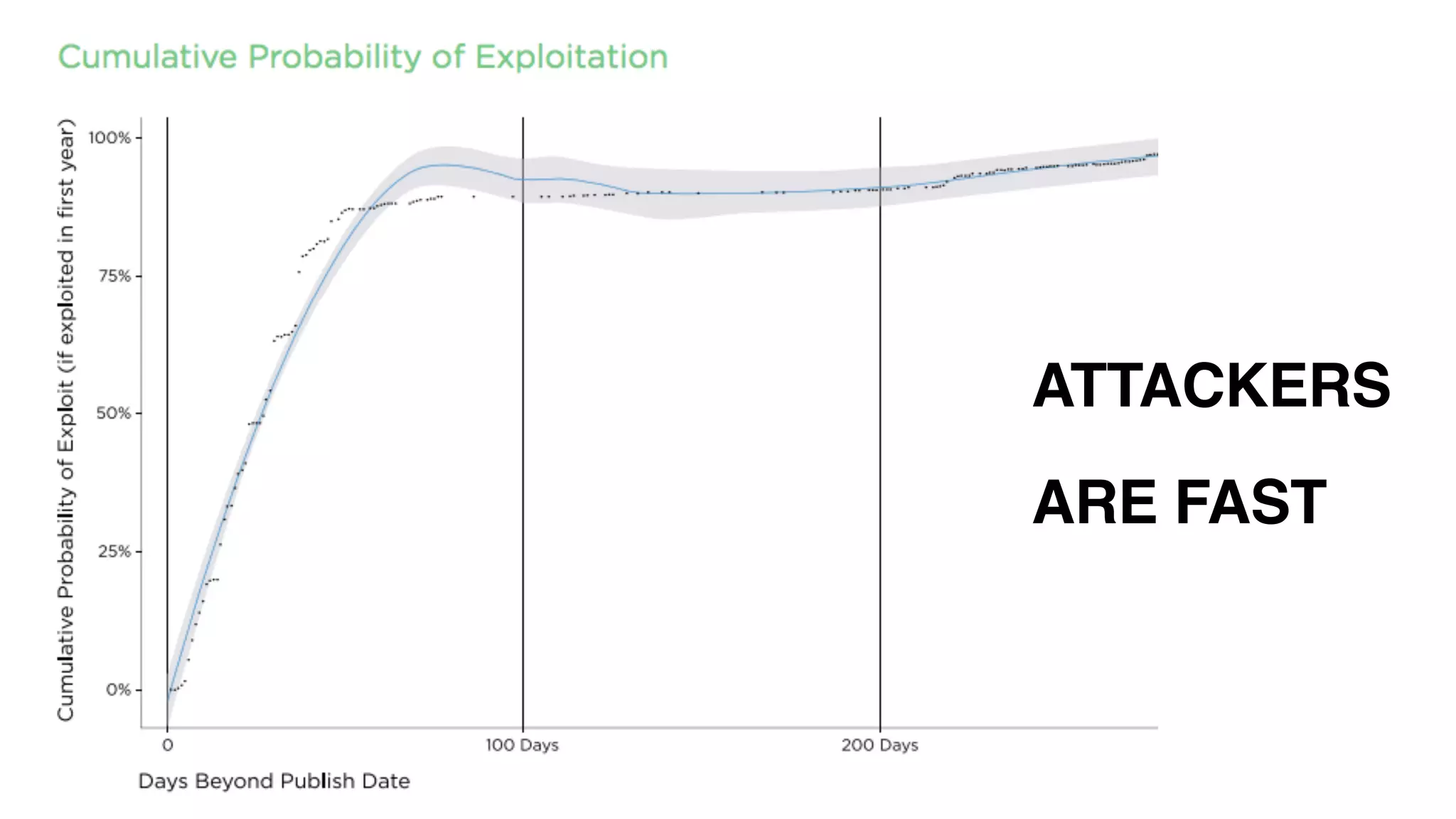
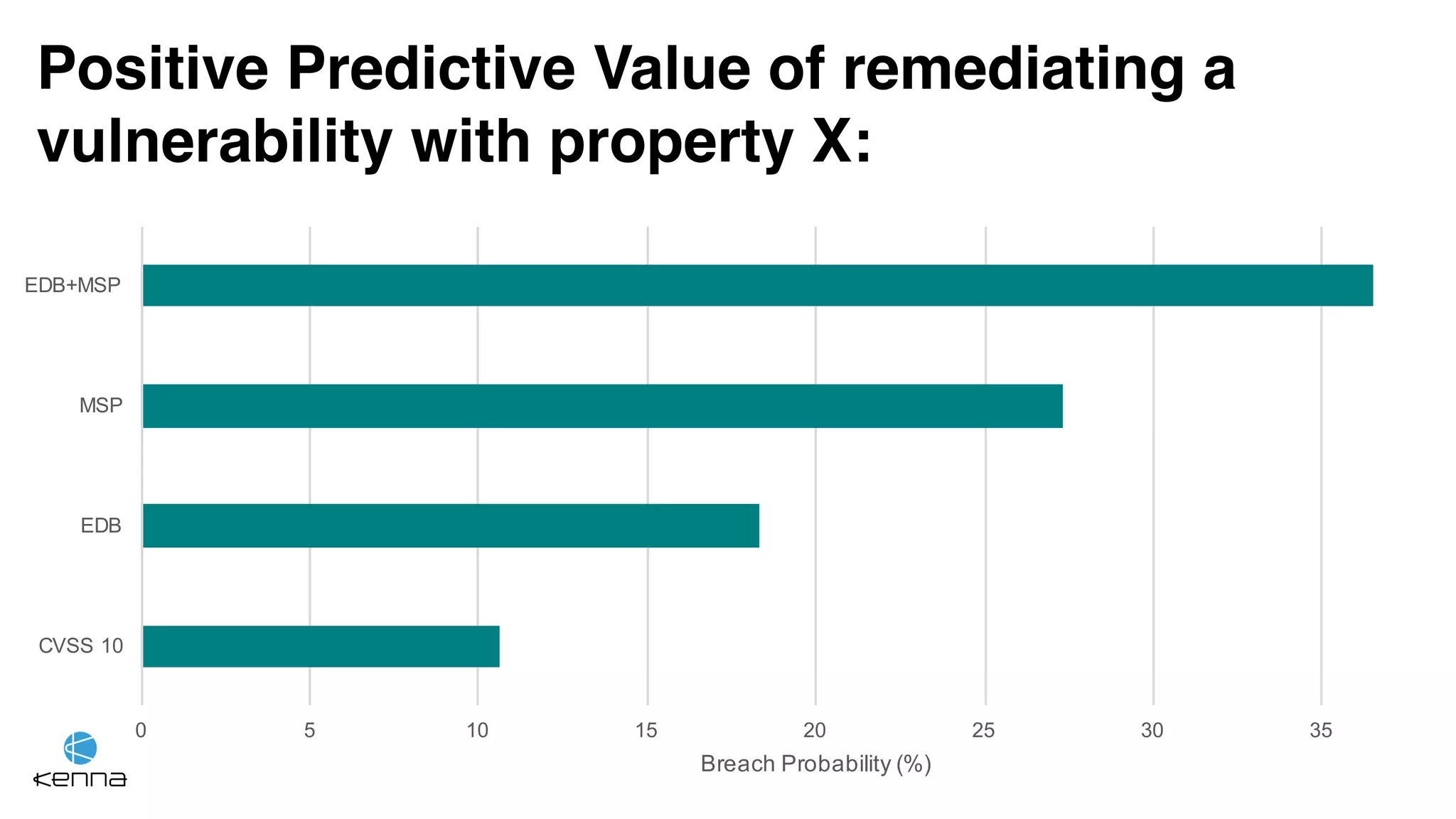
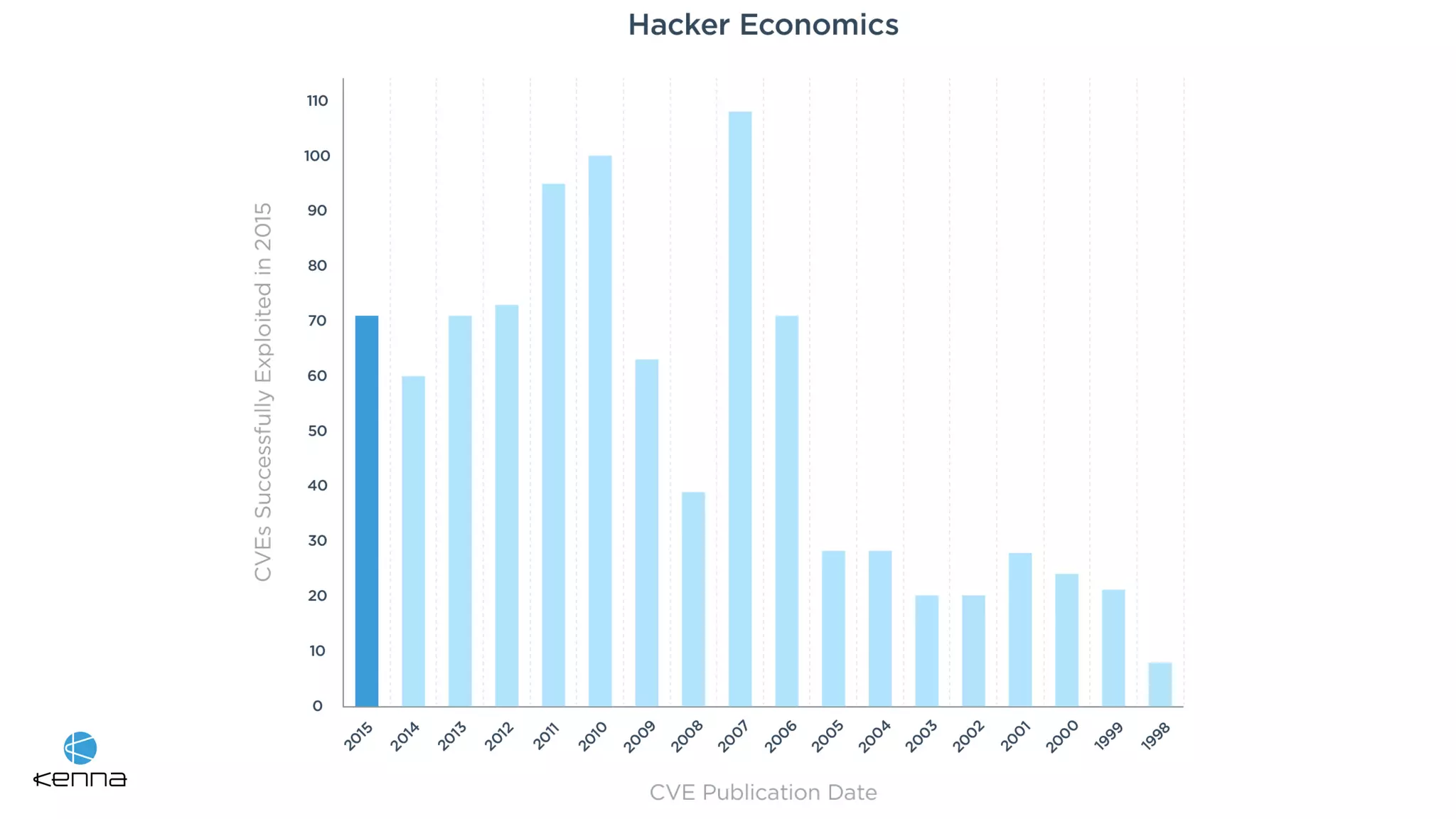
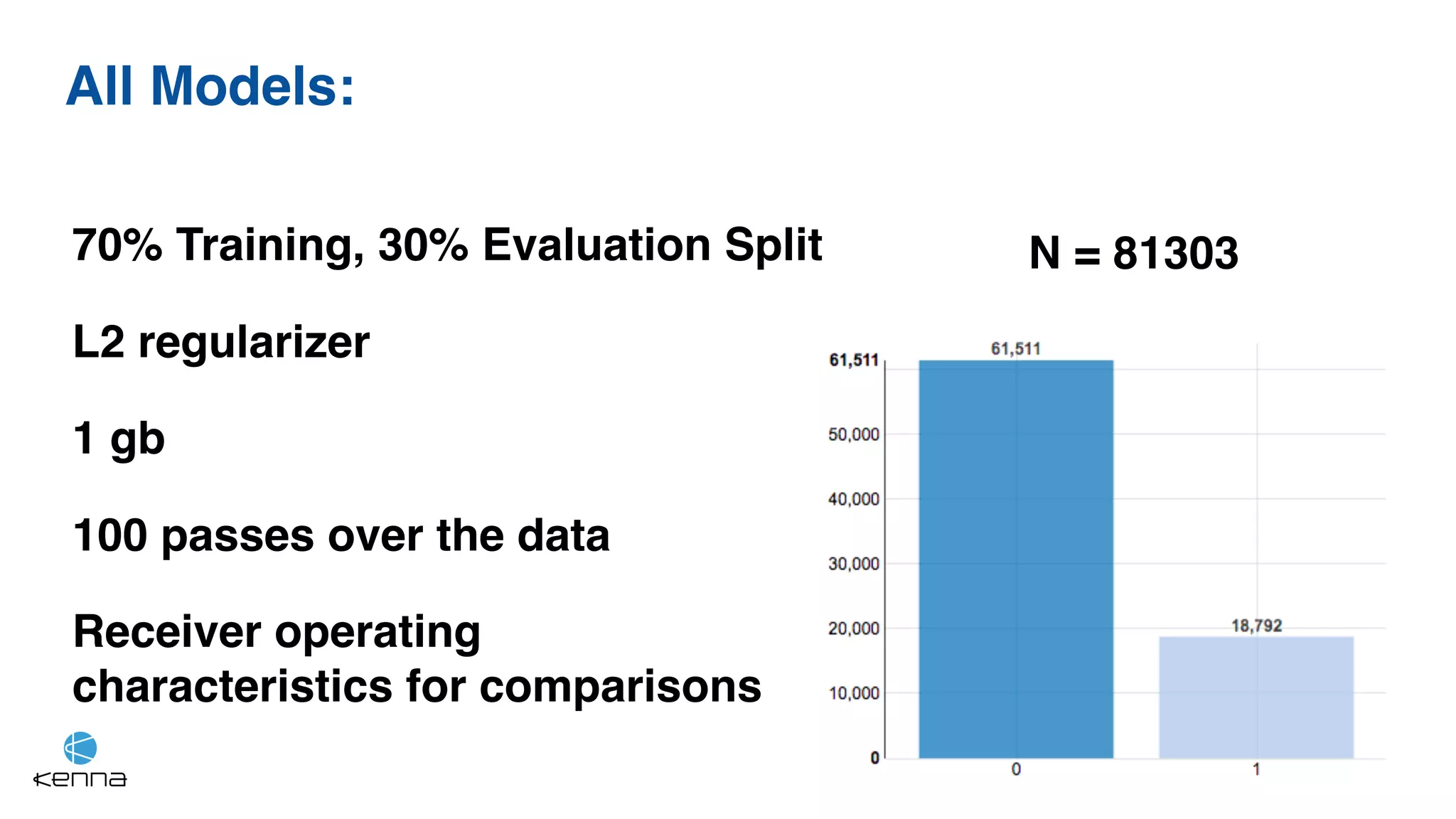
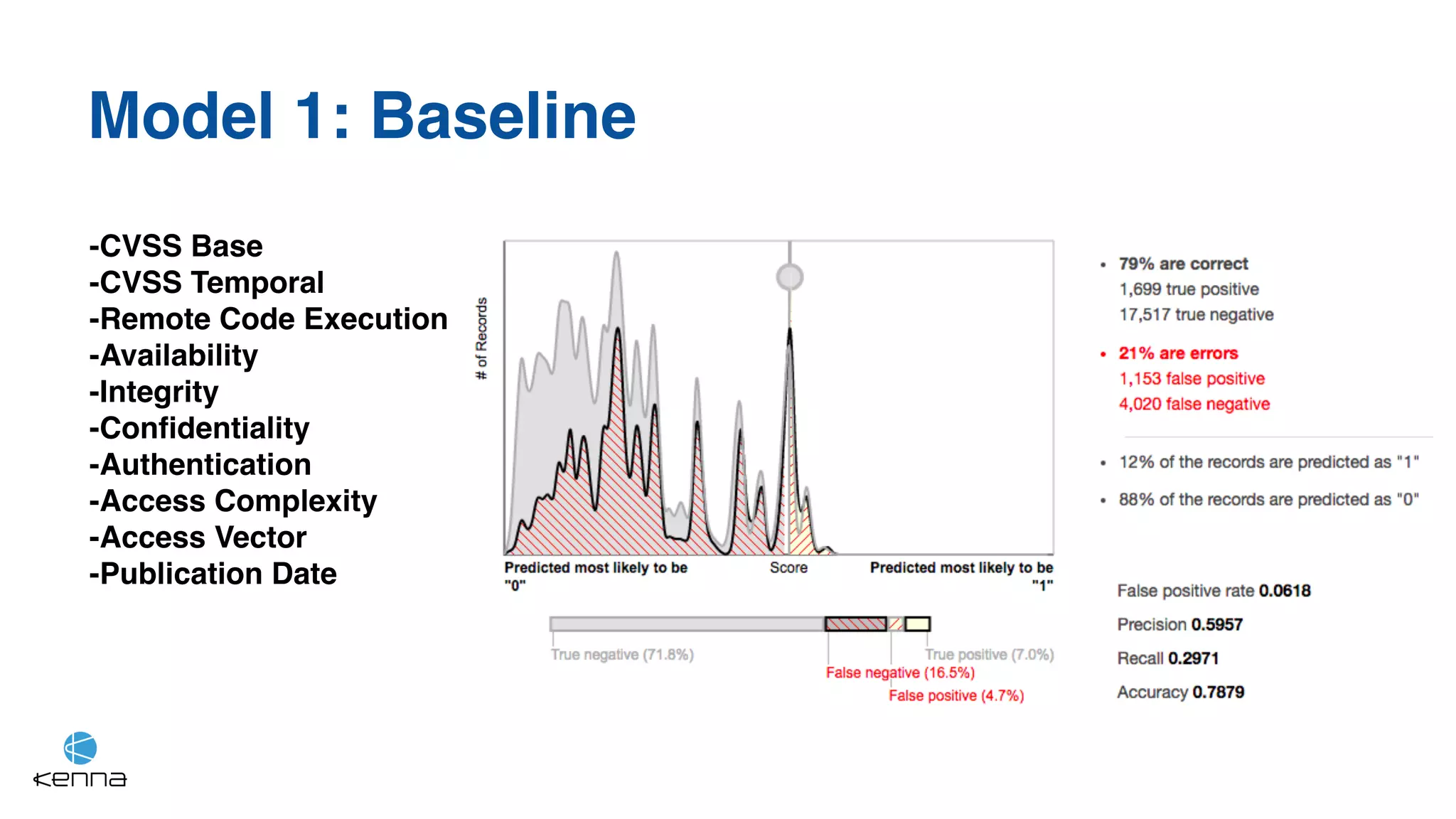
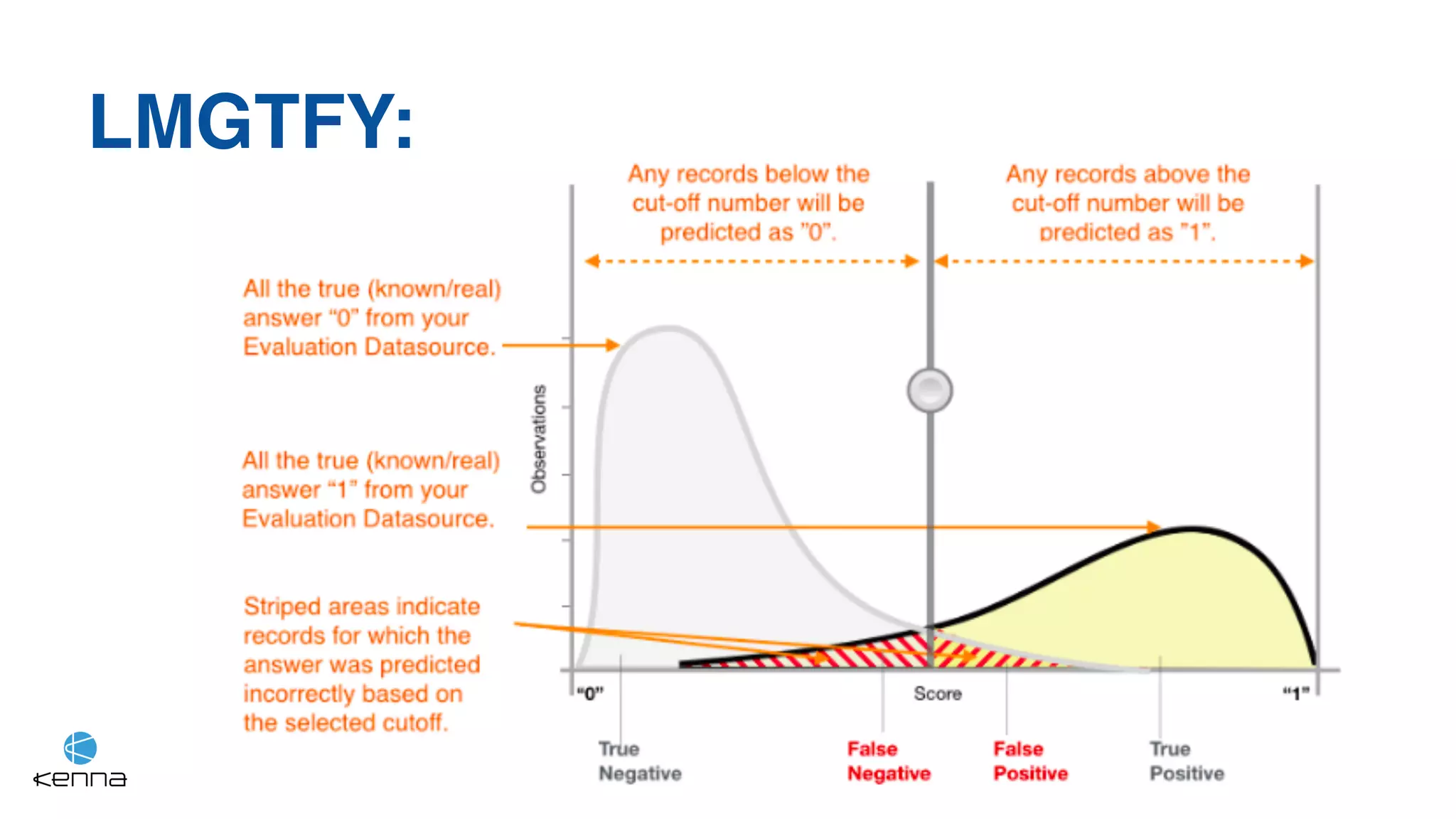
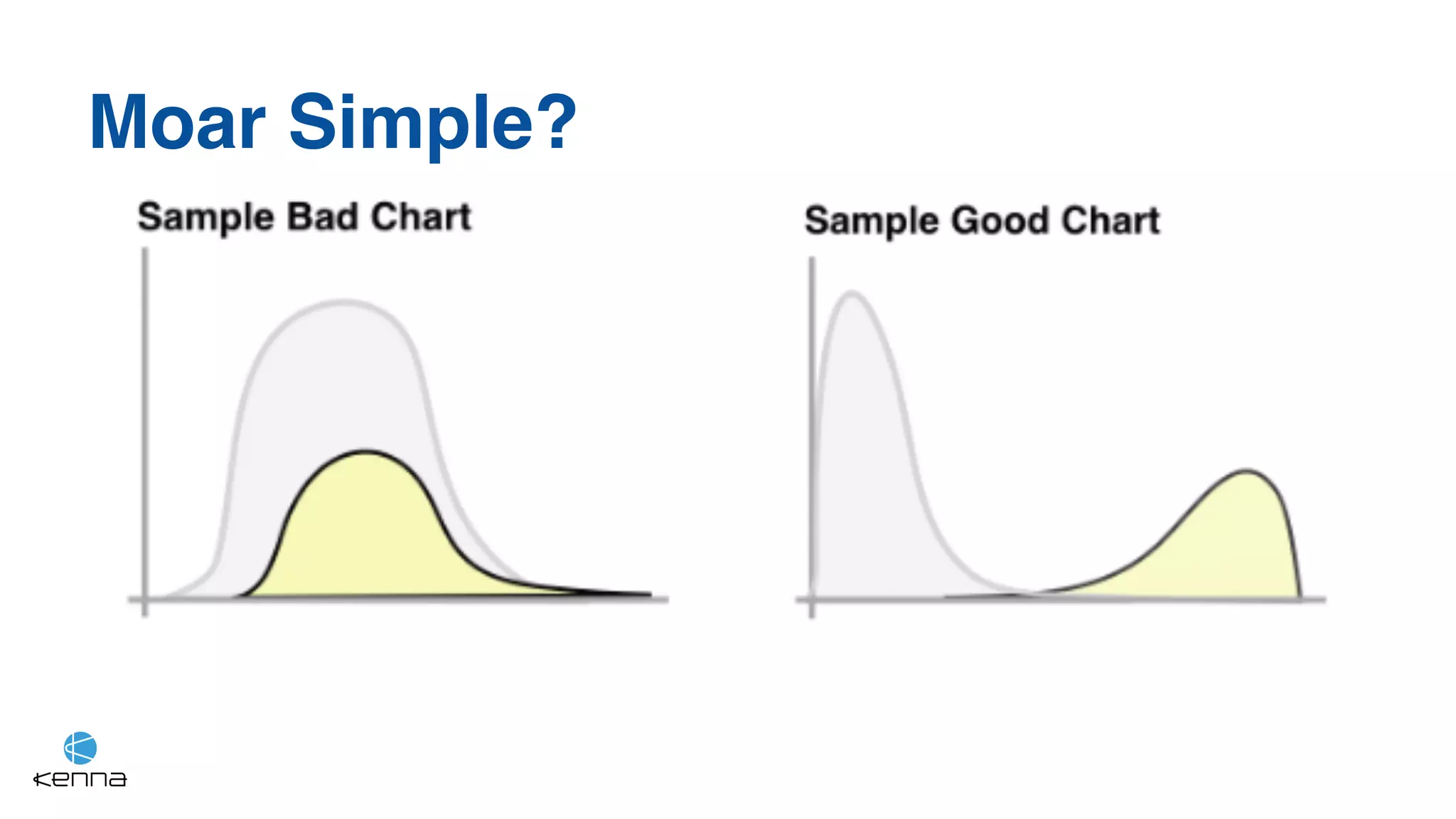
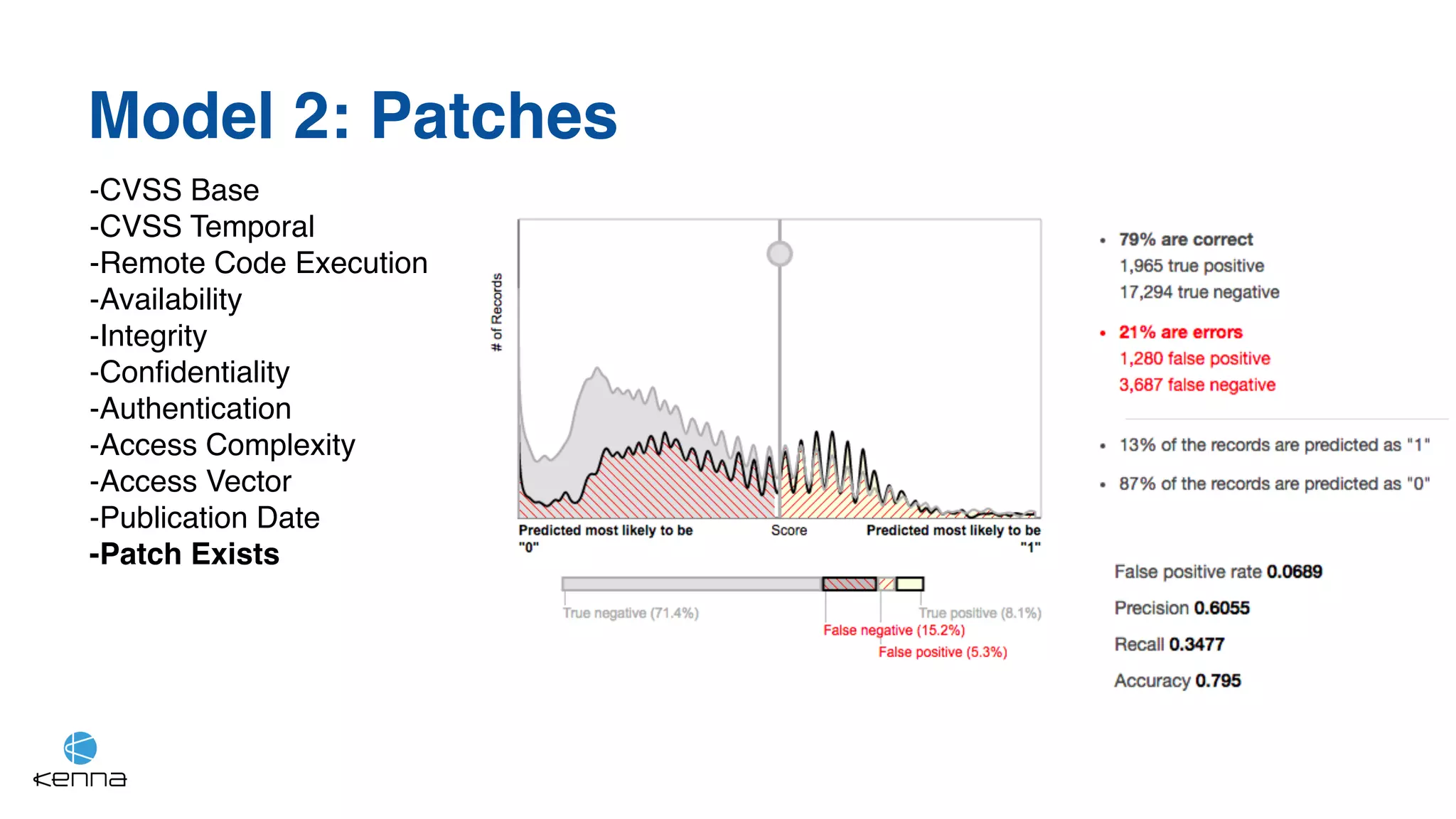
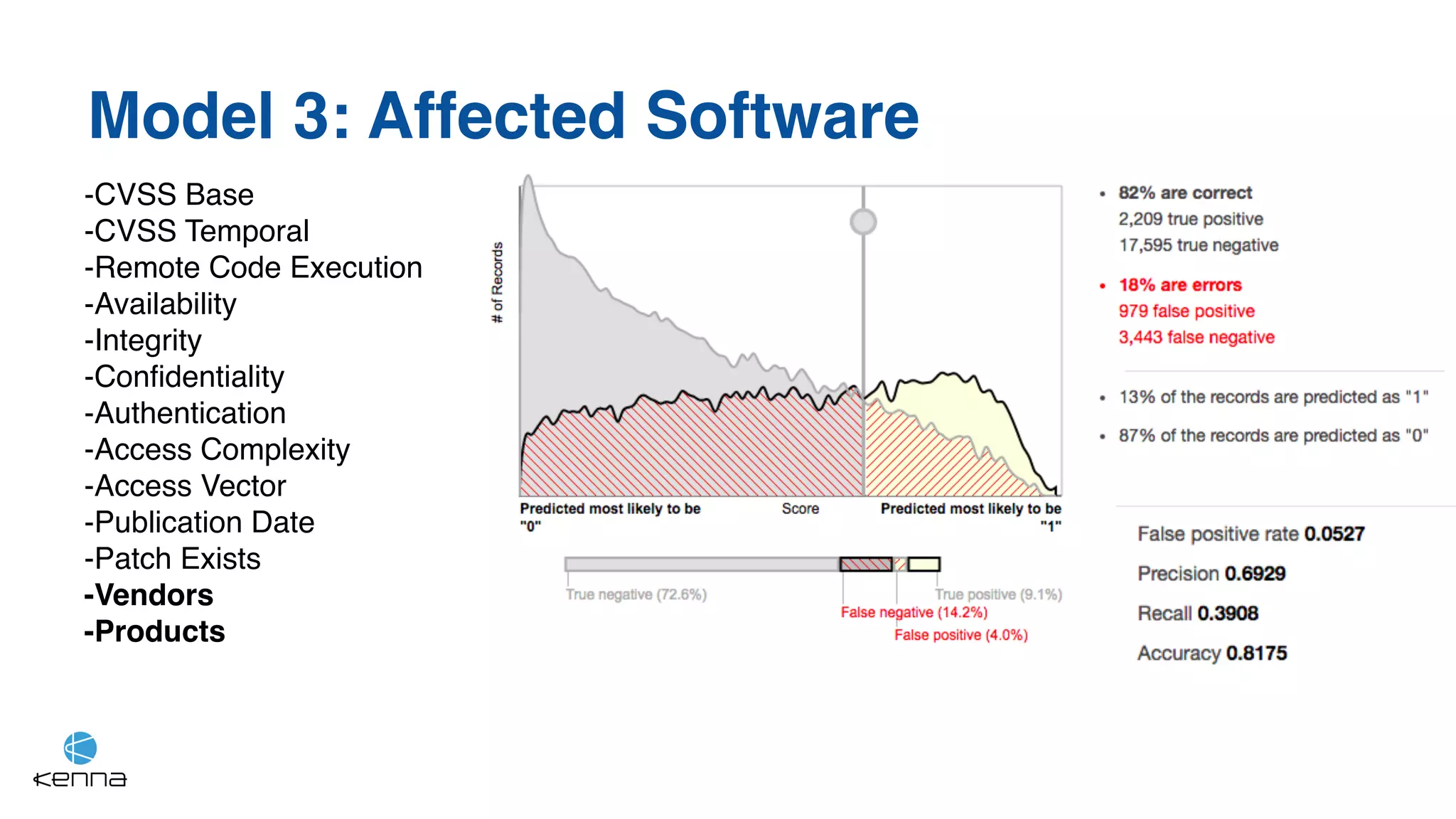
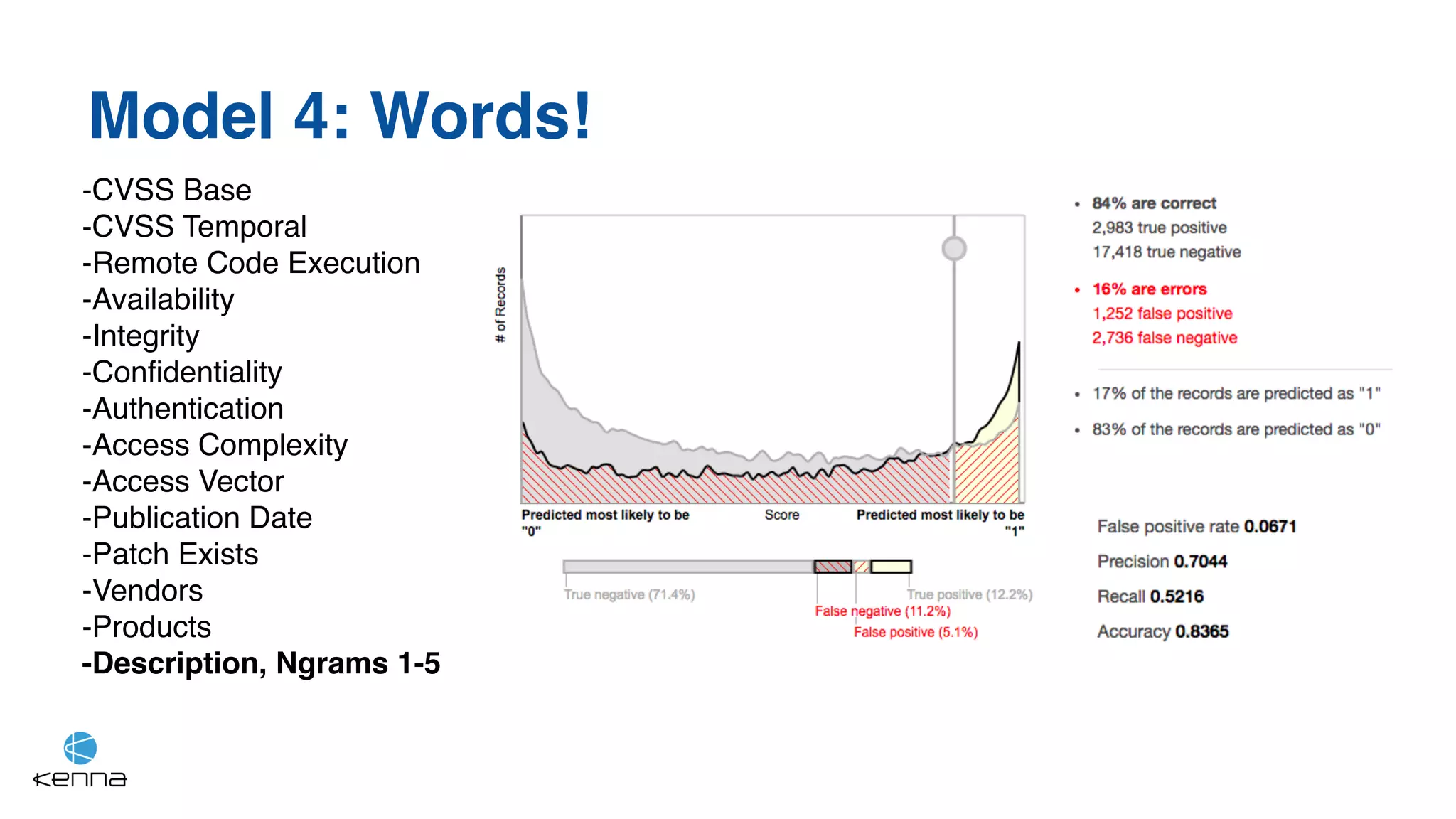
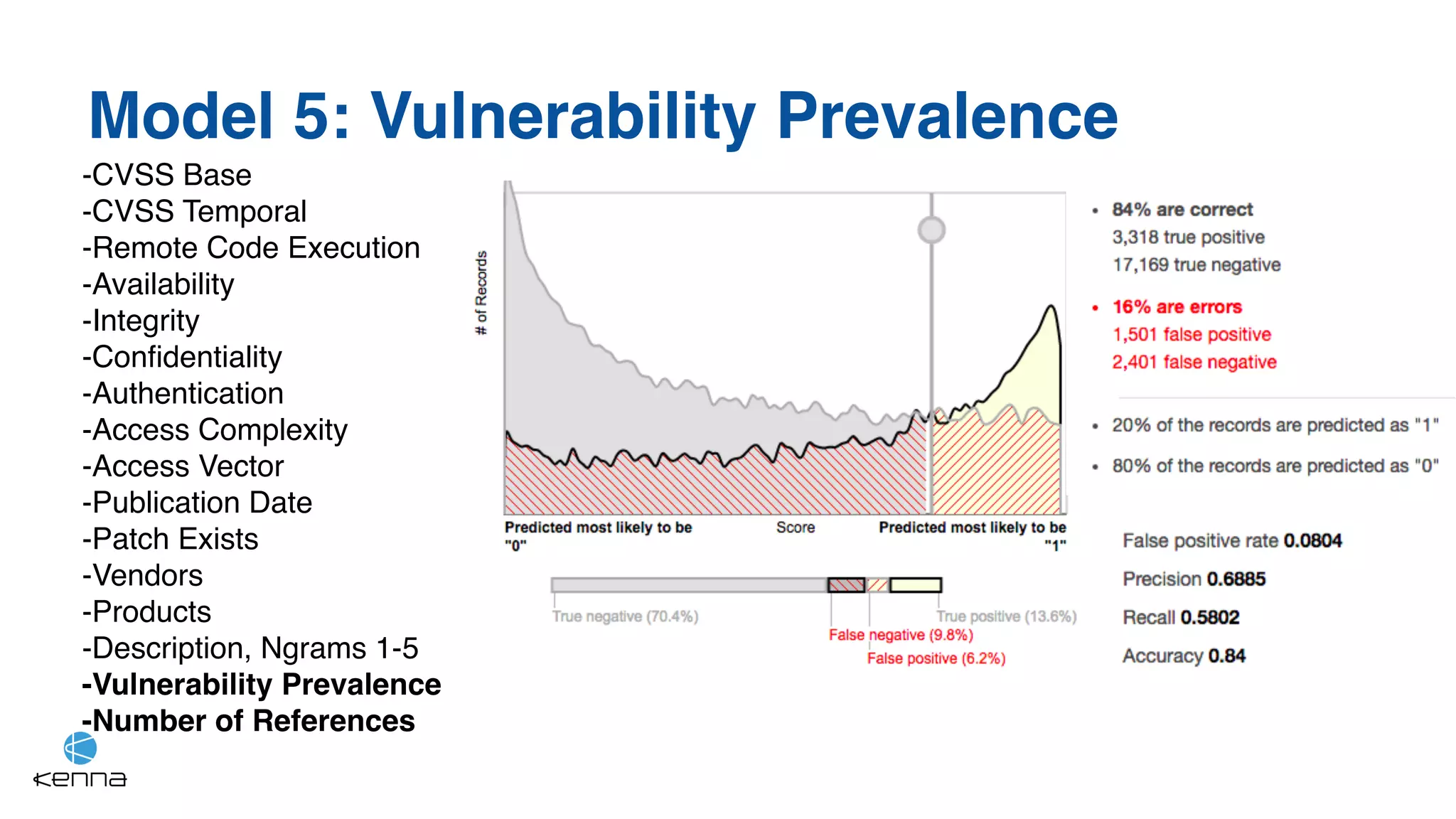
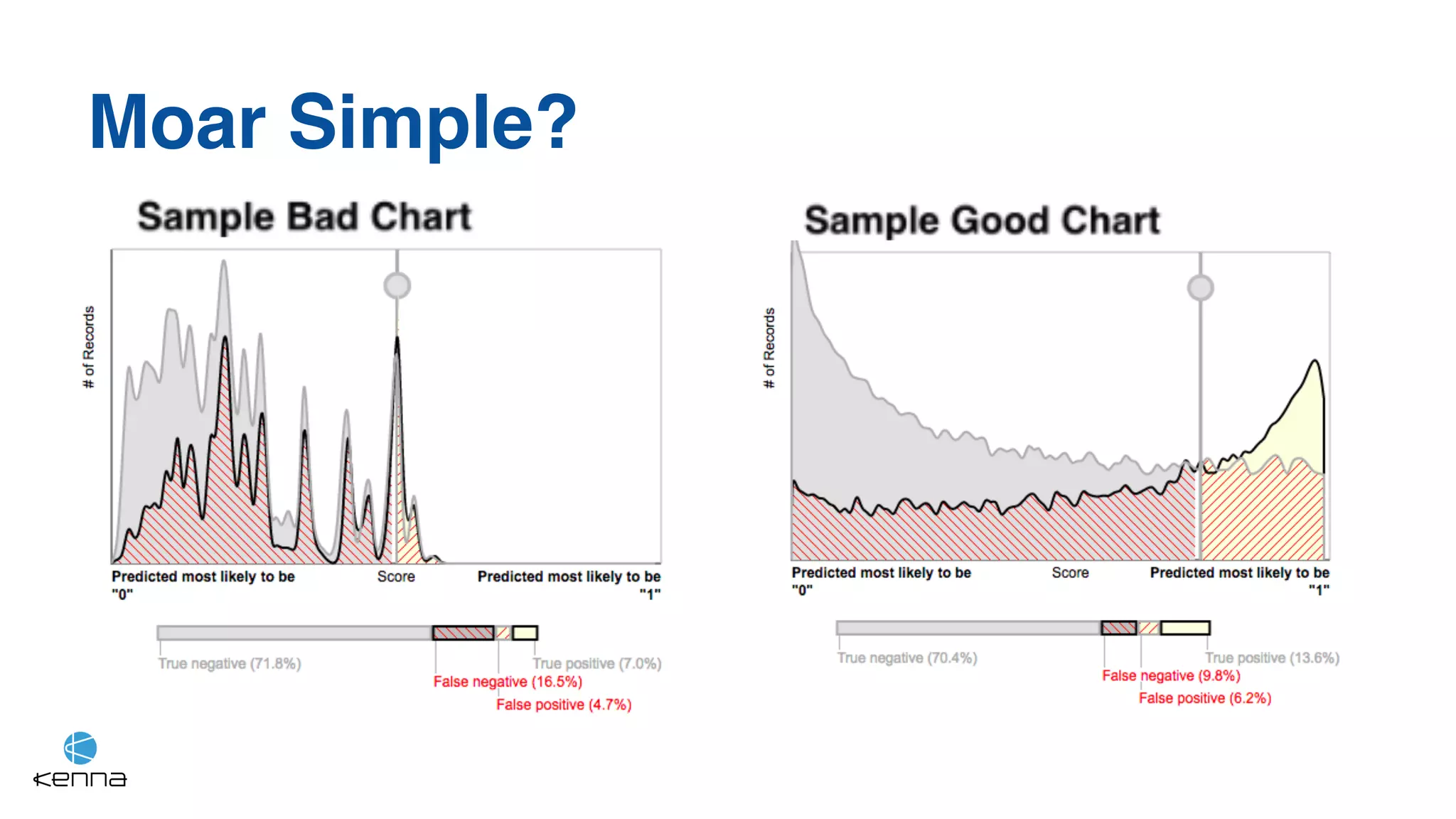
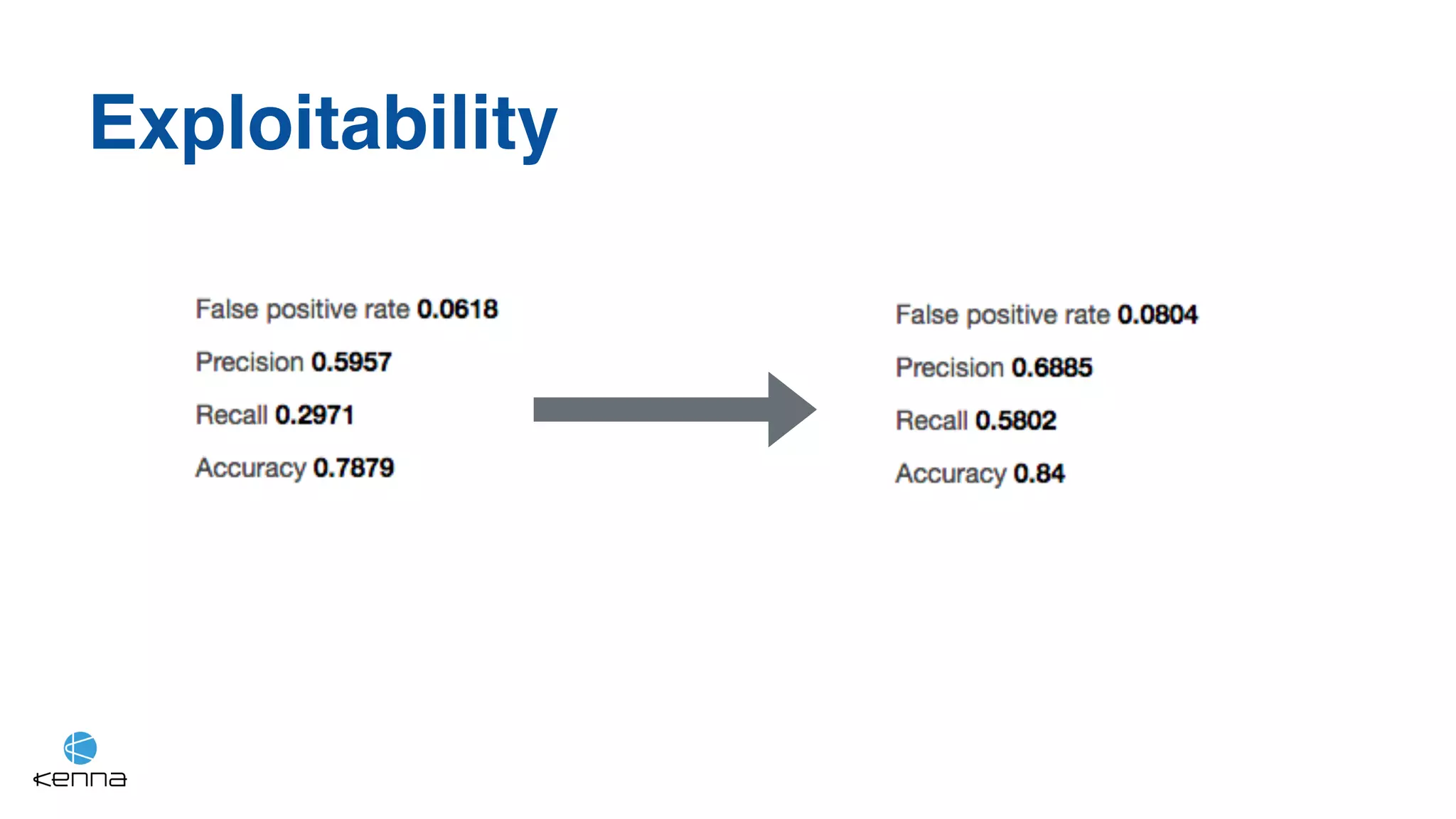
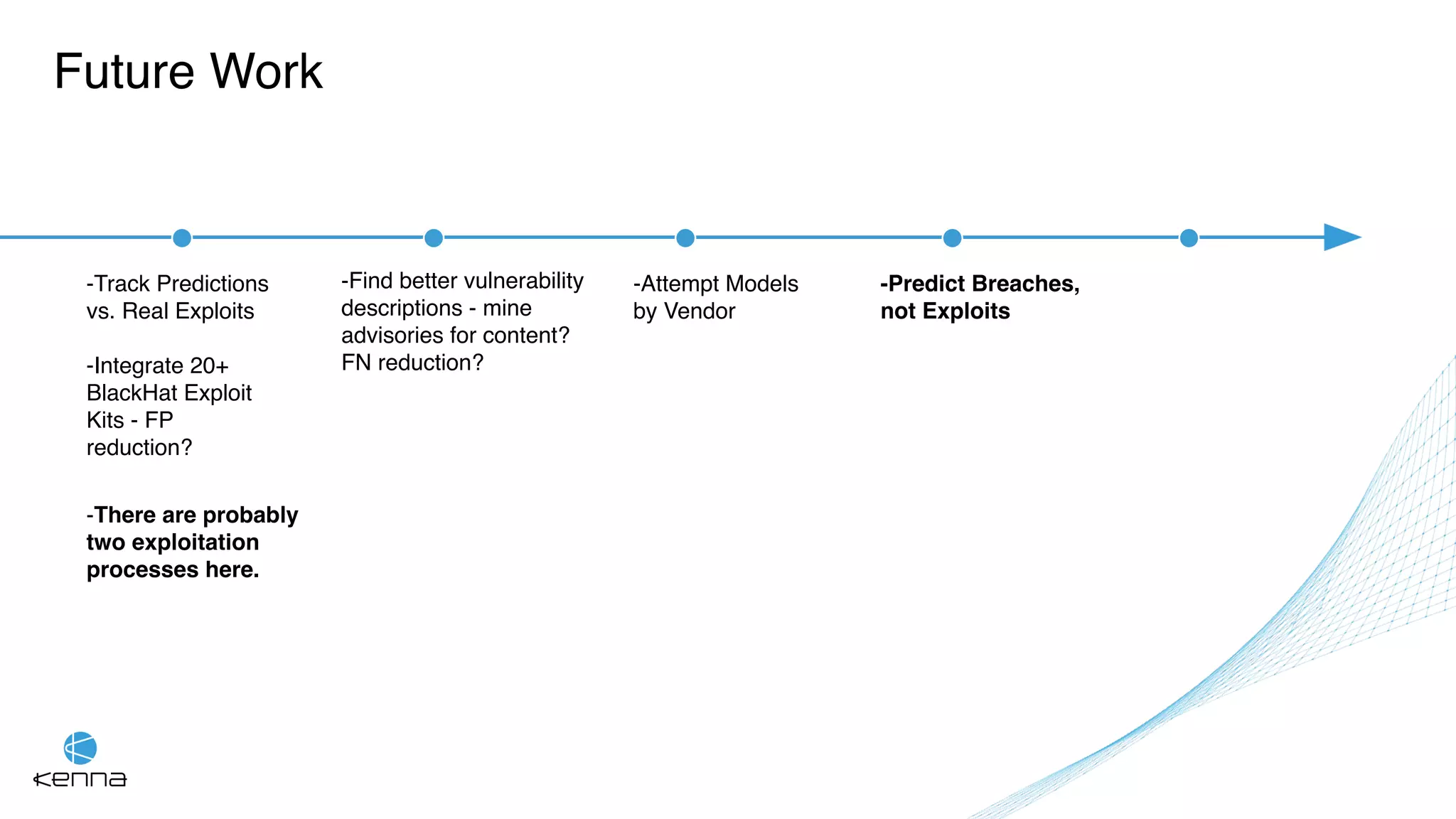
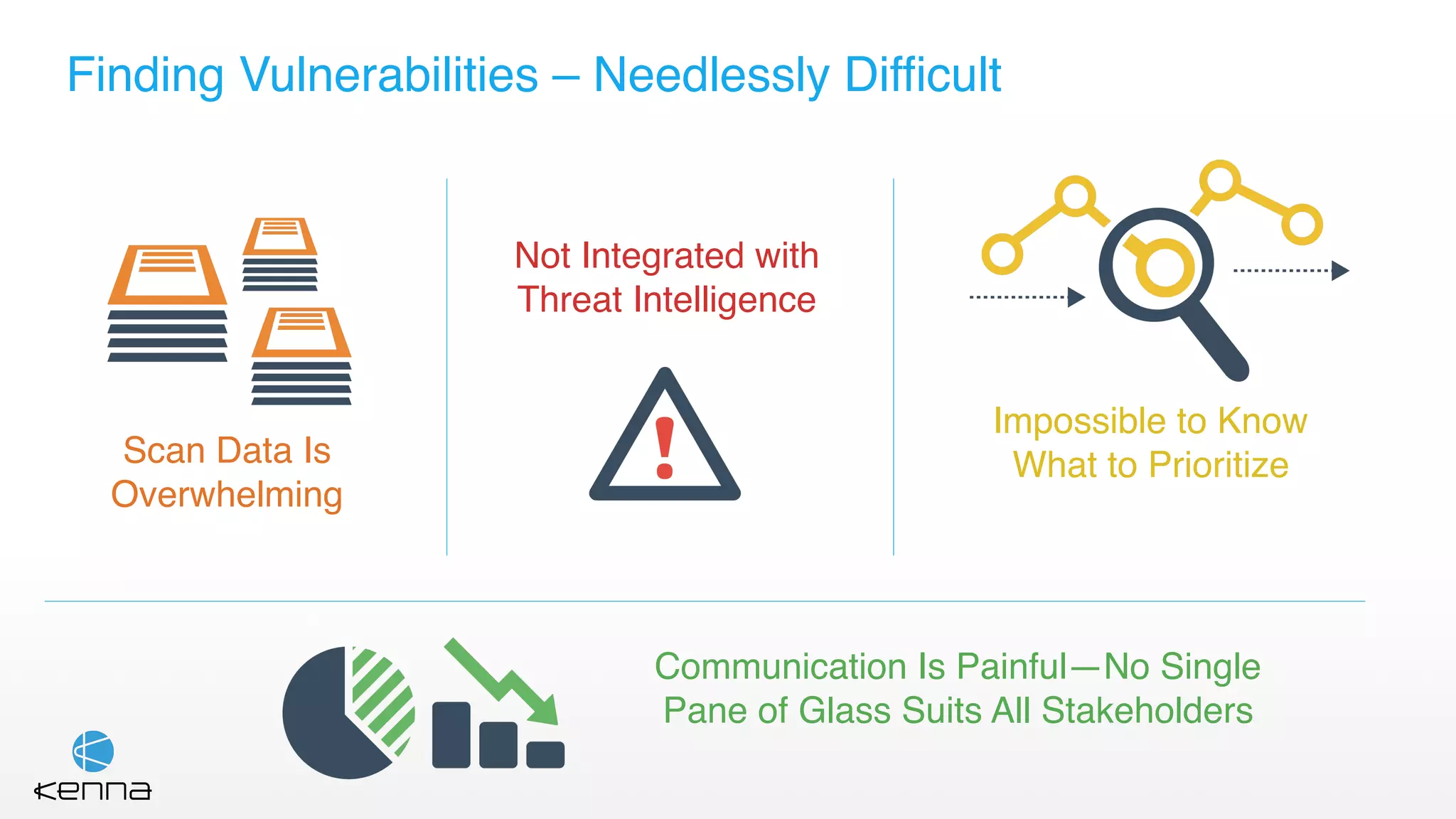
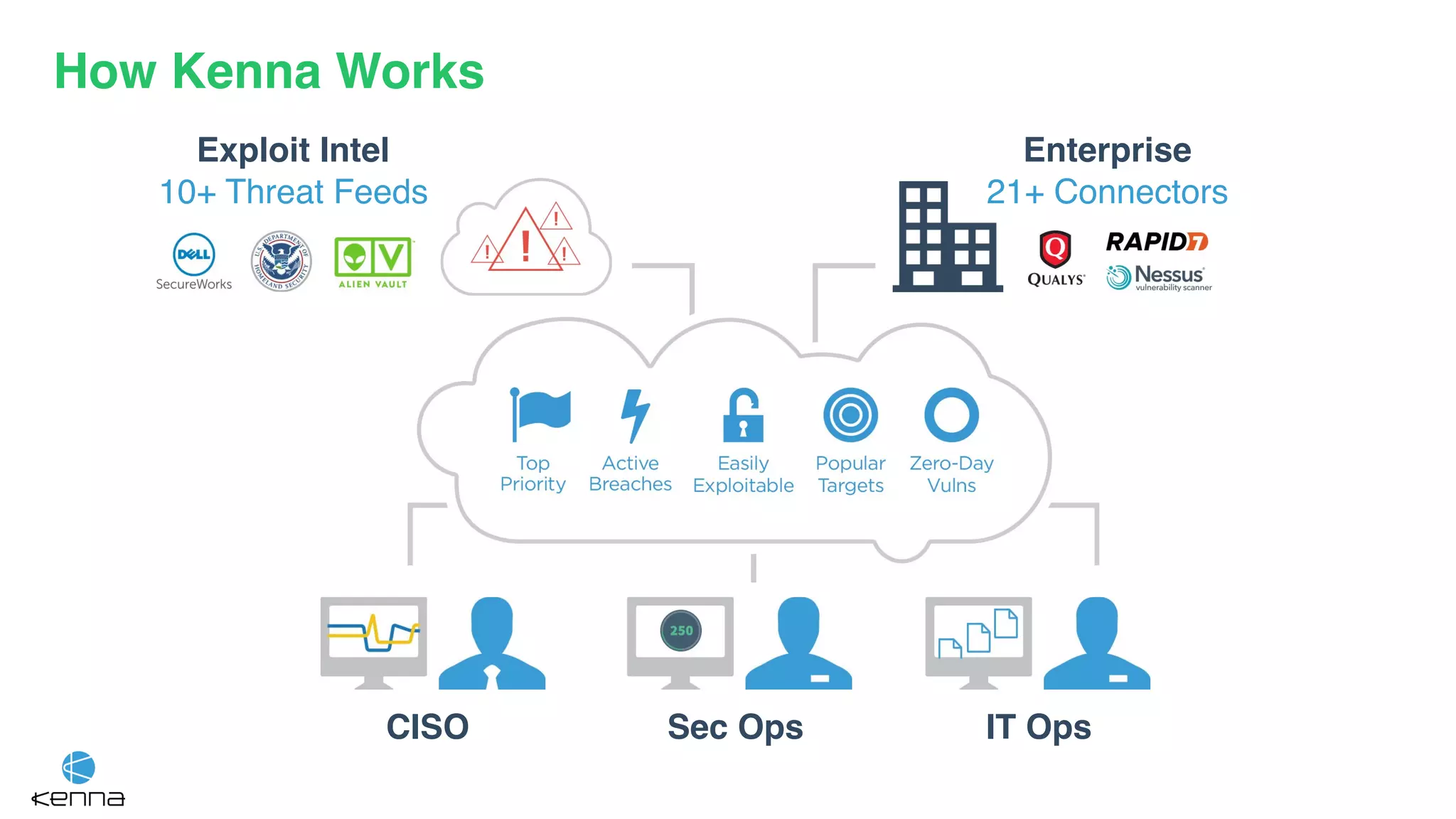
The document discusses the challenges in predicting exploitability of software vulnerabilities and categorizes it into retrospective, real-time, and predictive methods. It highlights the use of machine learning models, various data points, and integration with threat intelligence to improve vulnerability management and prioritization. The future work suggests predicting breaches rather than just exploits and emphasizes the complexity of integrating various stakeholders' needs.