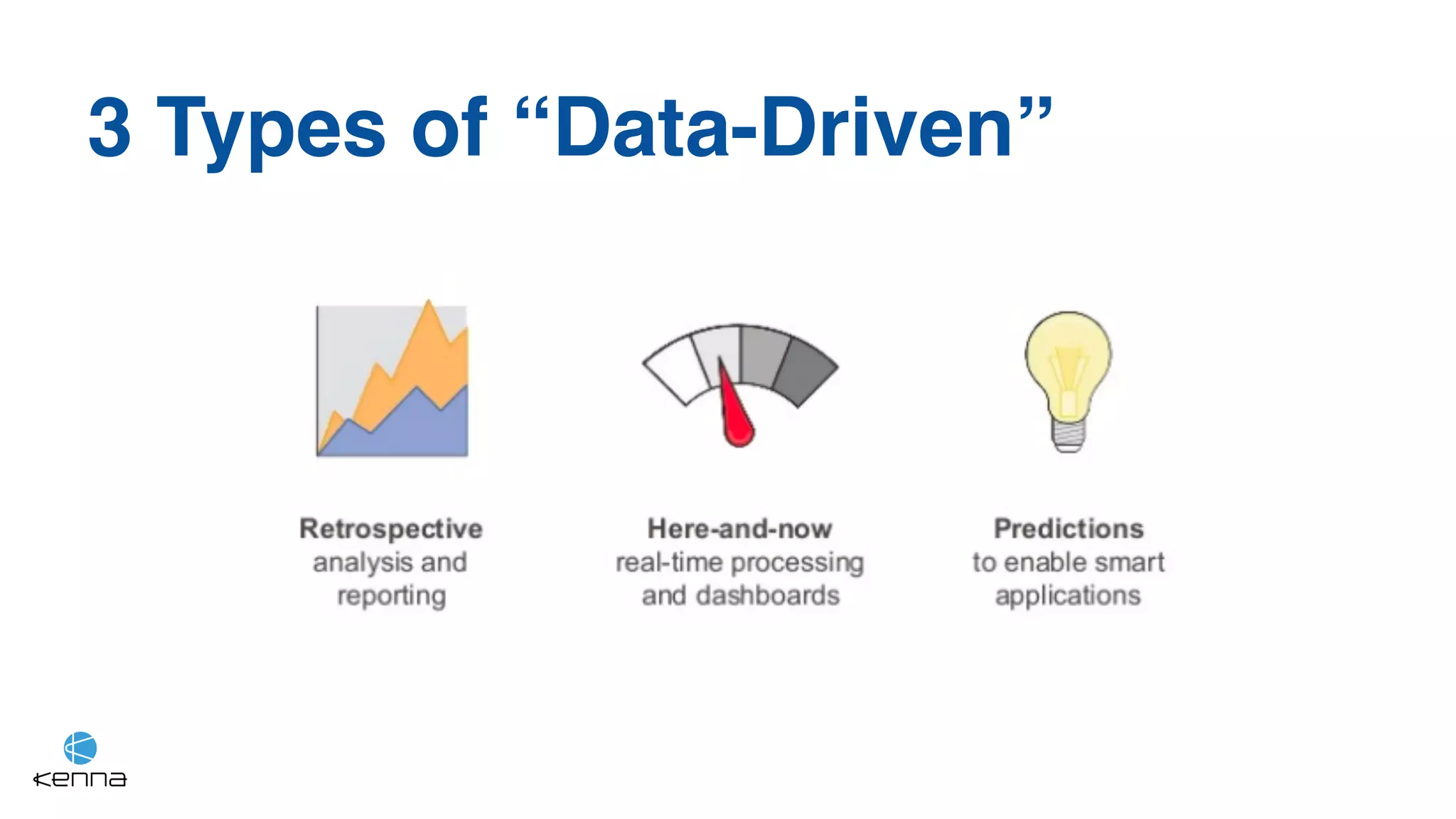
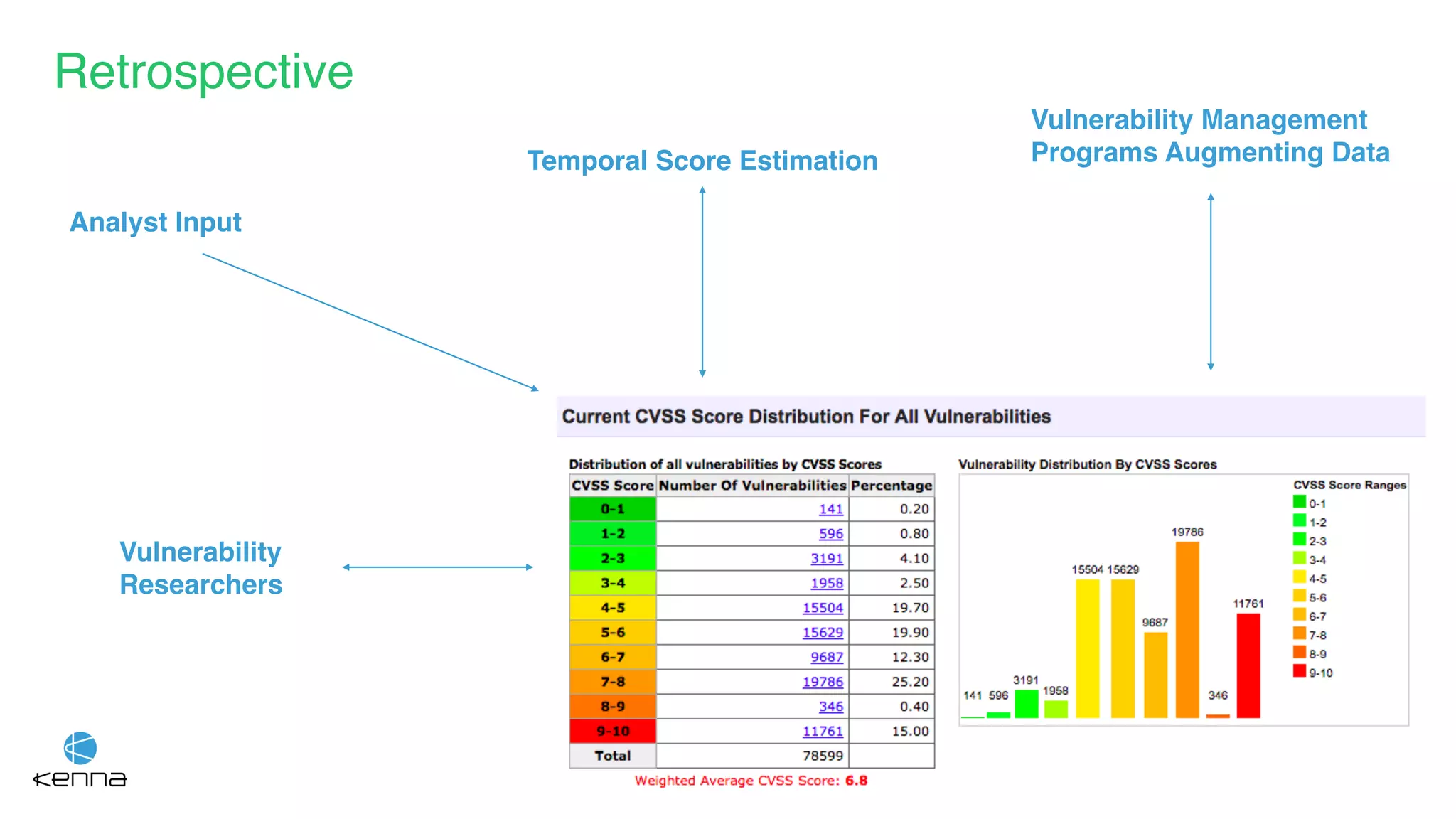
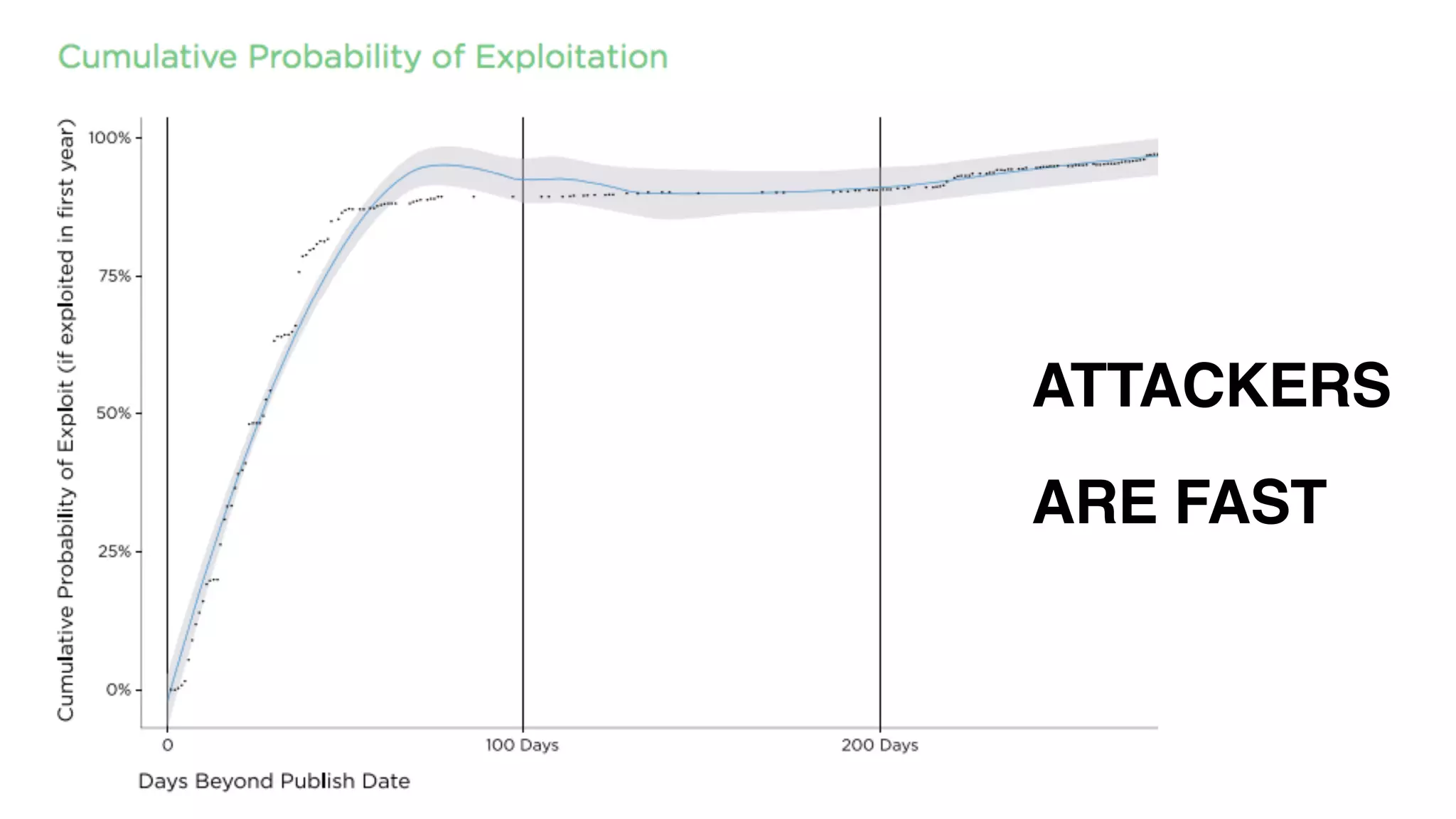
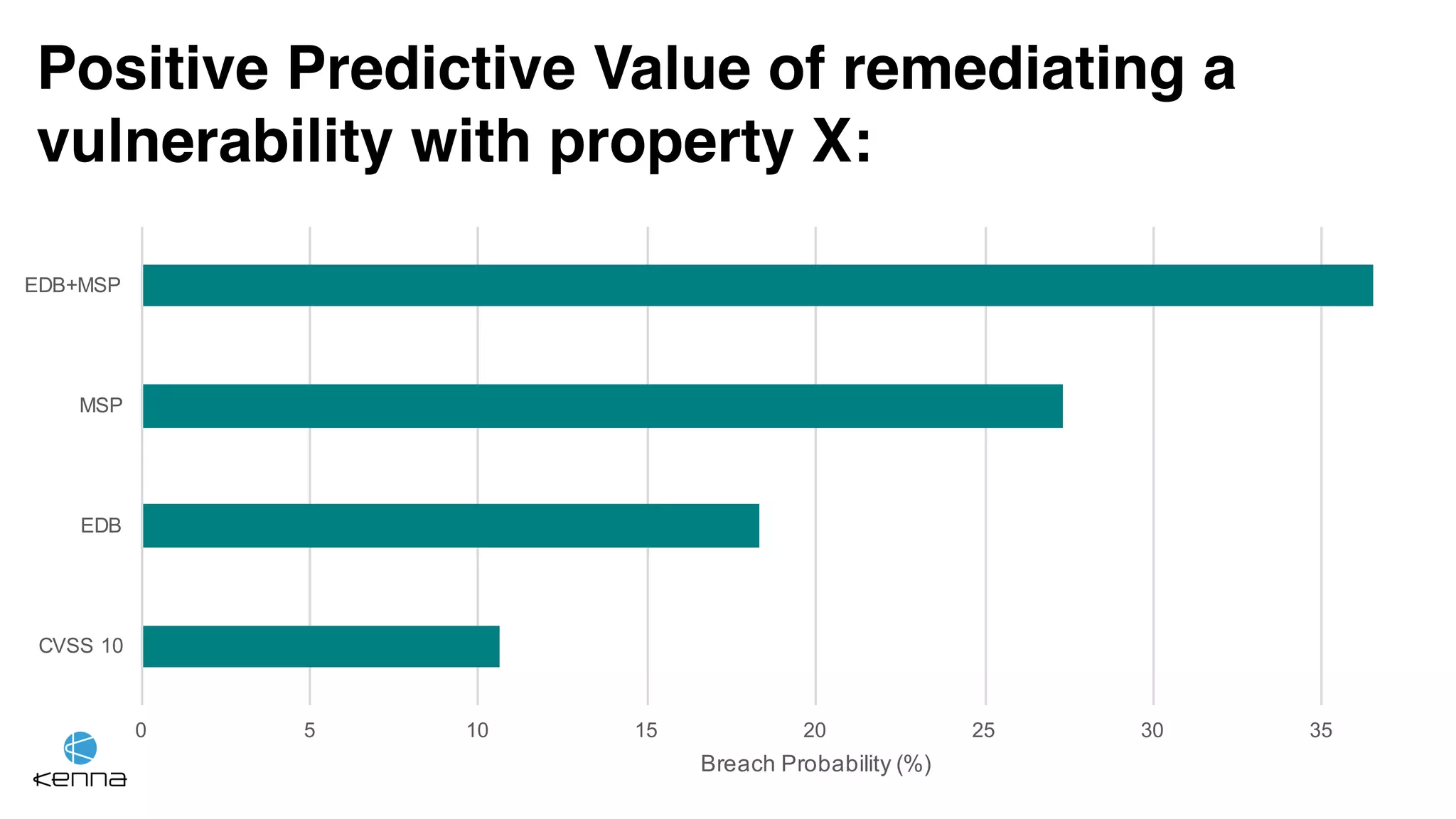
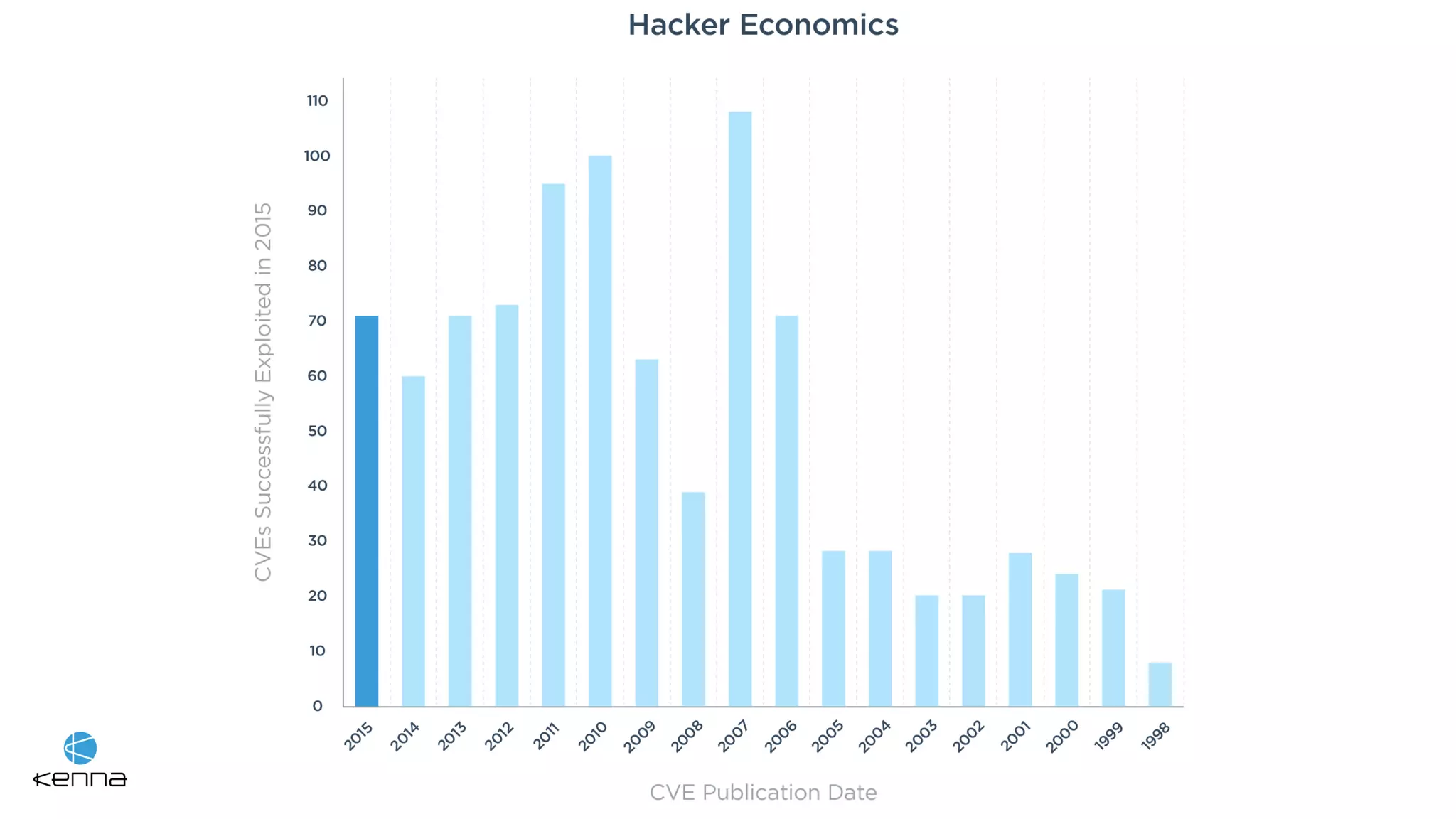
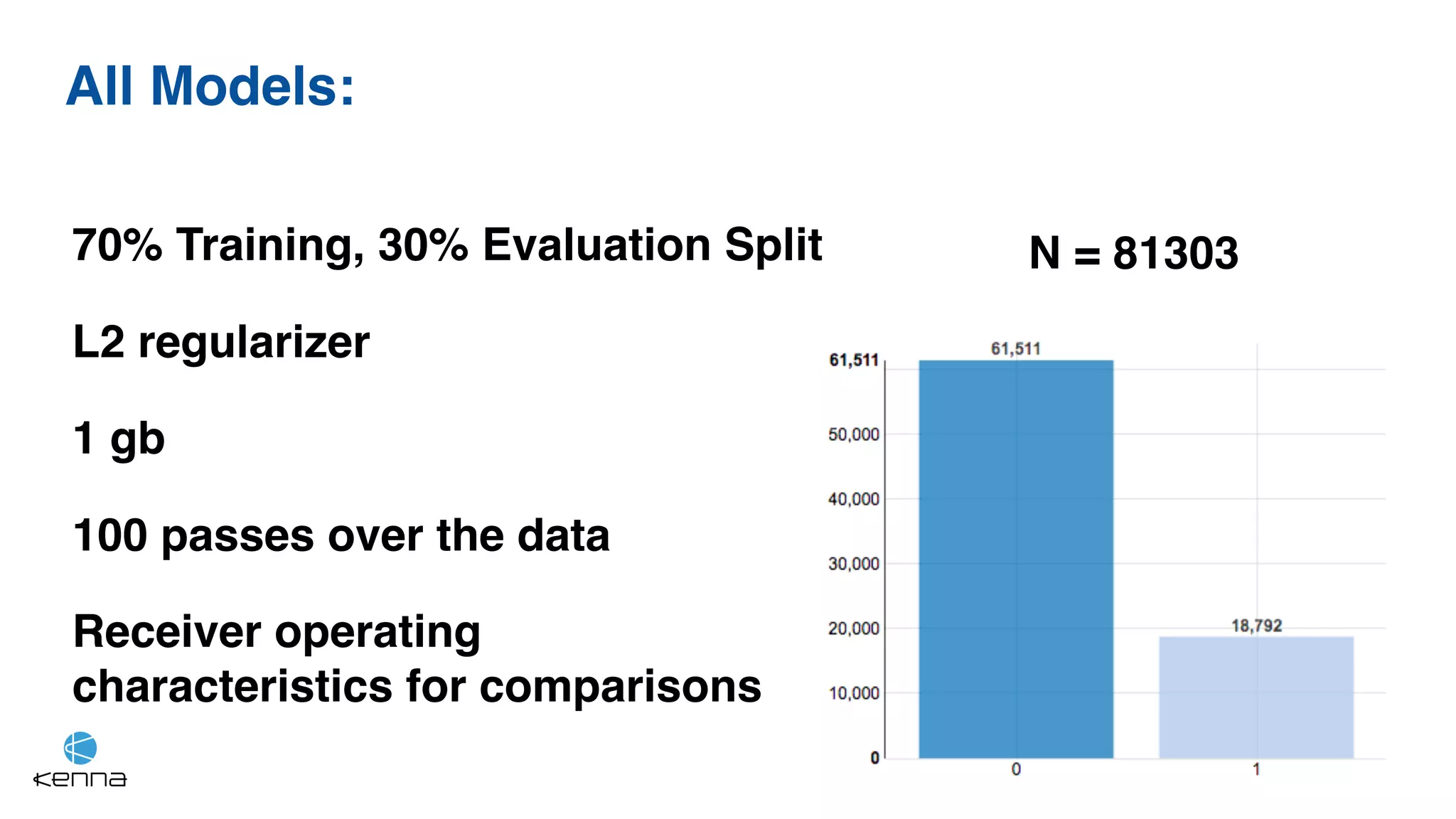
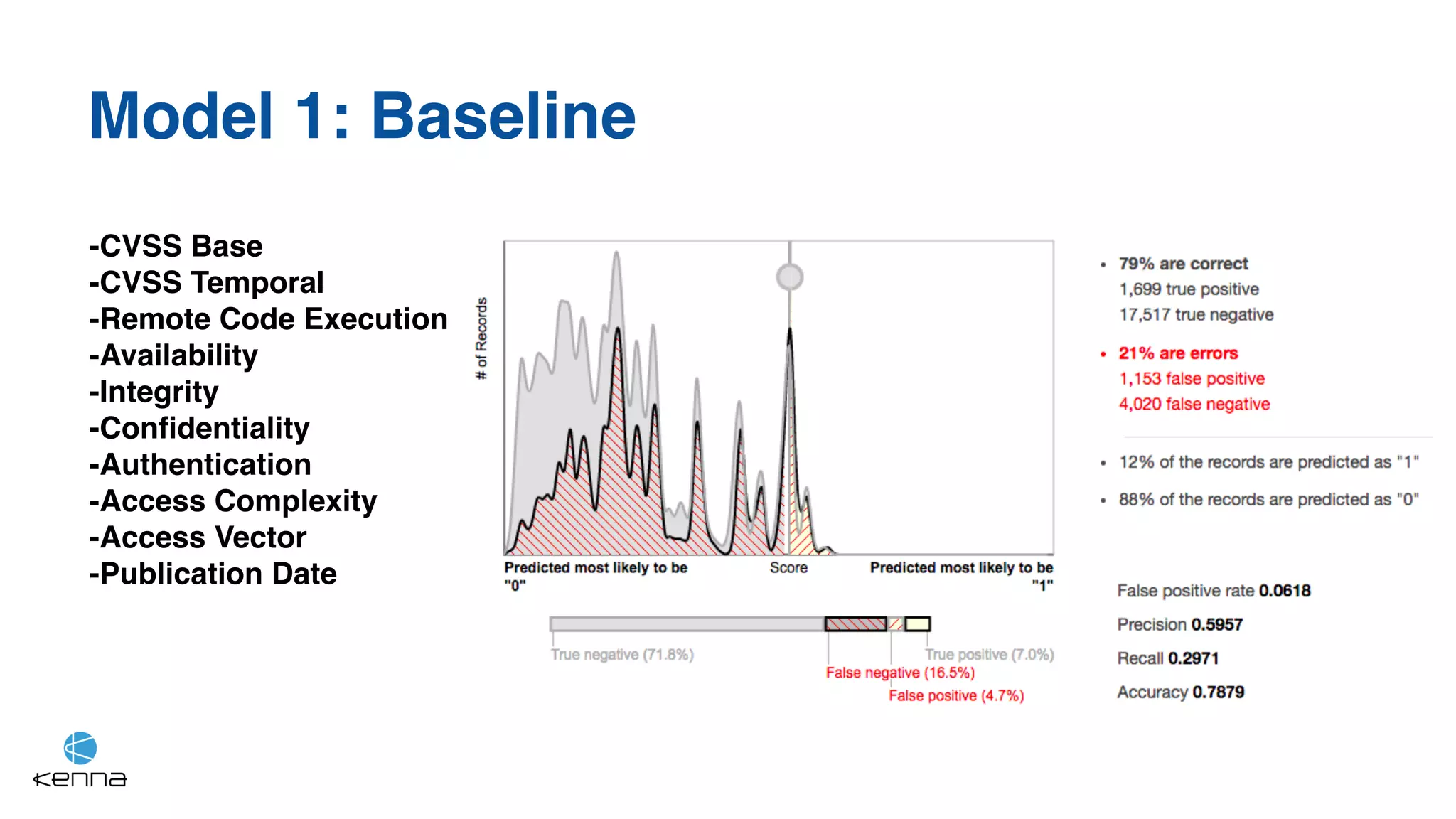
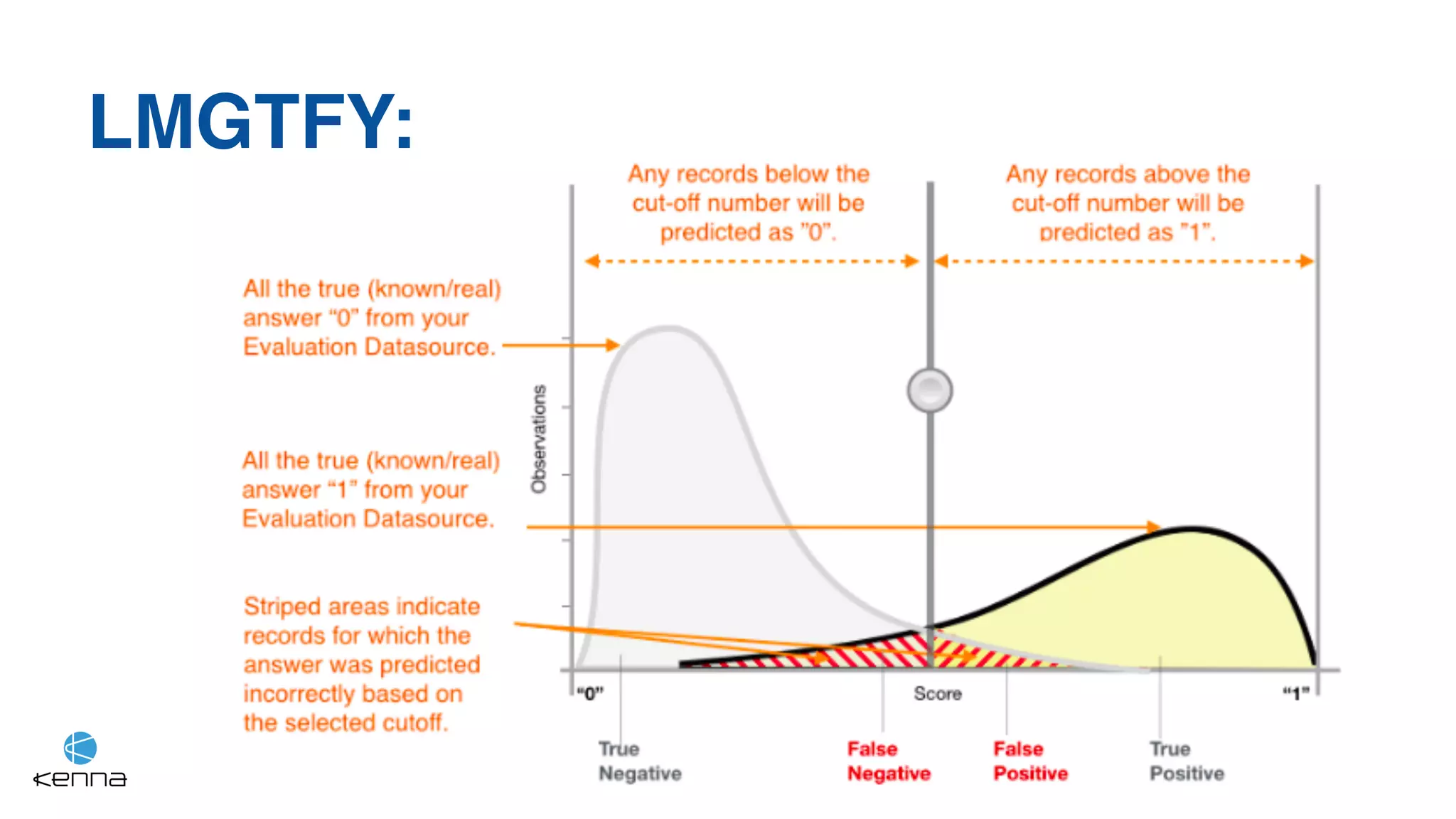
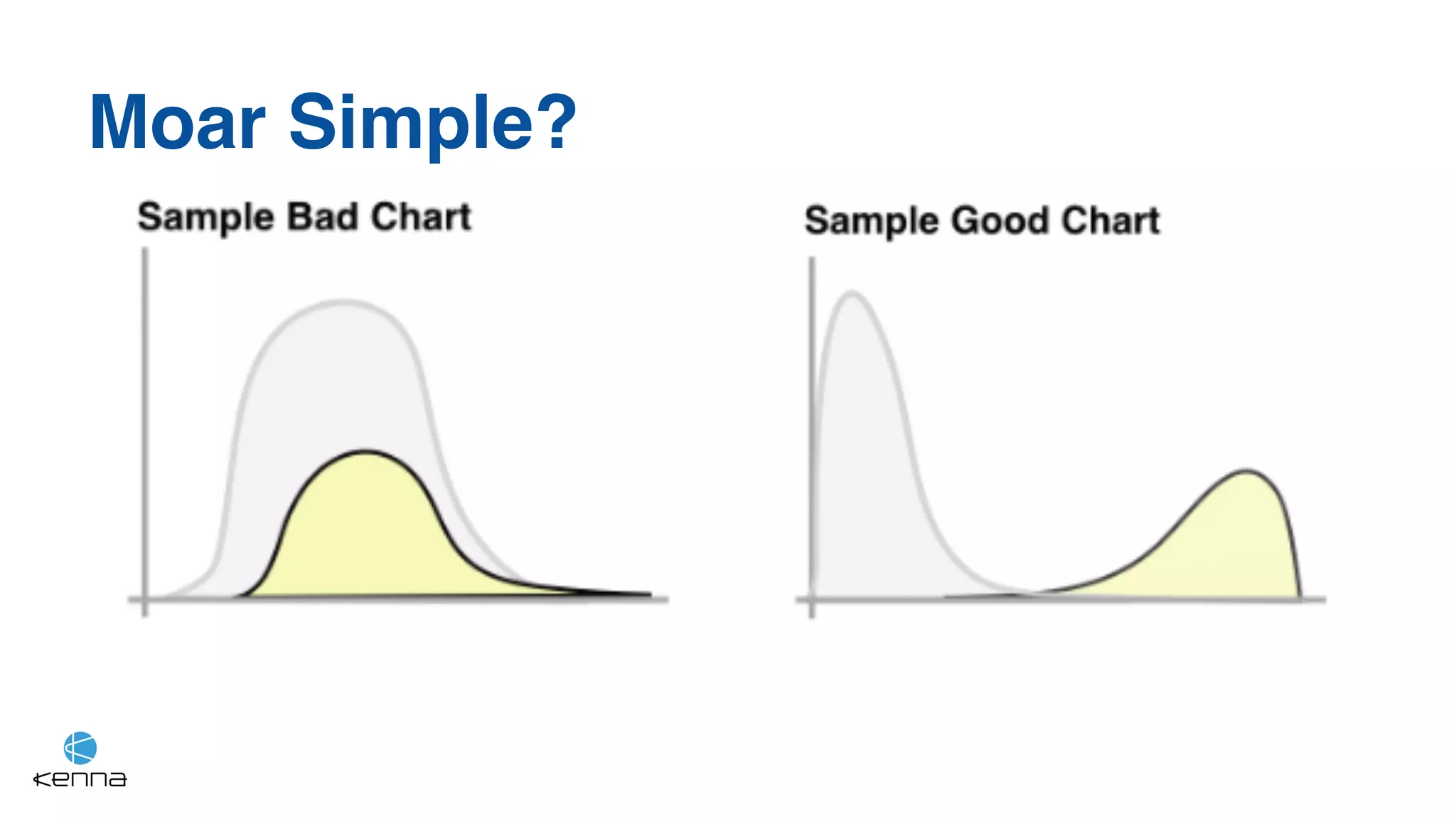
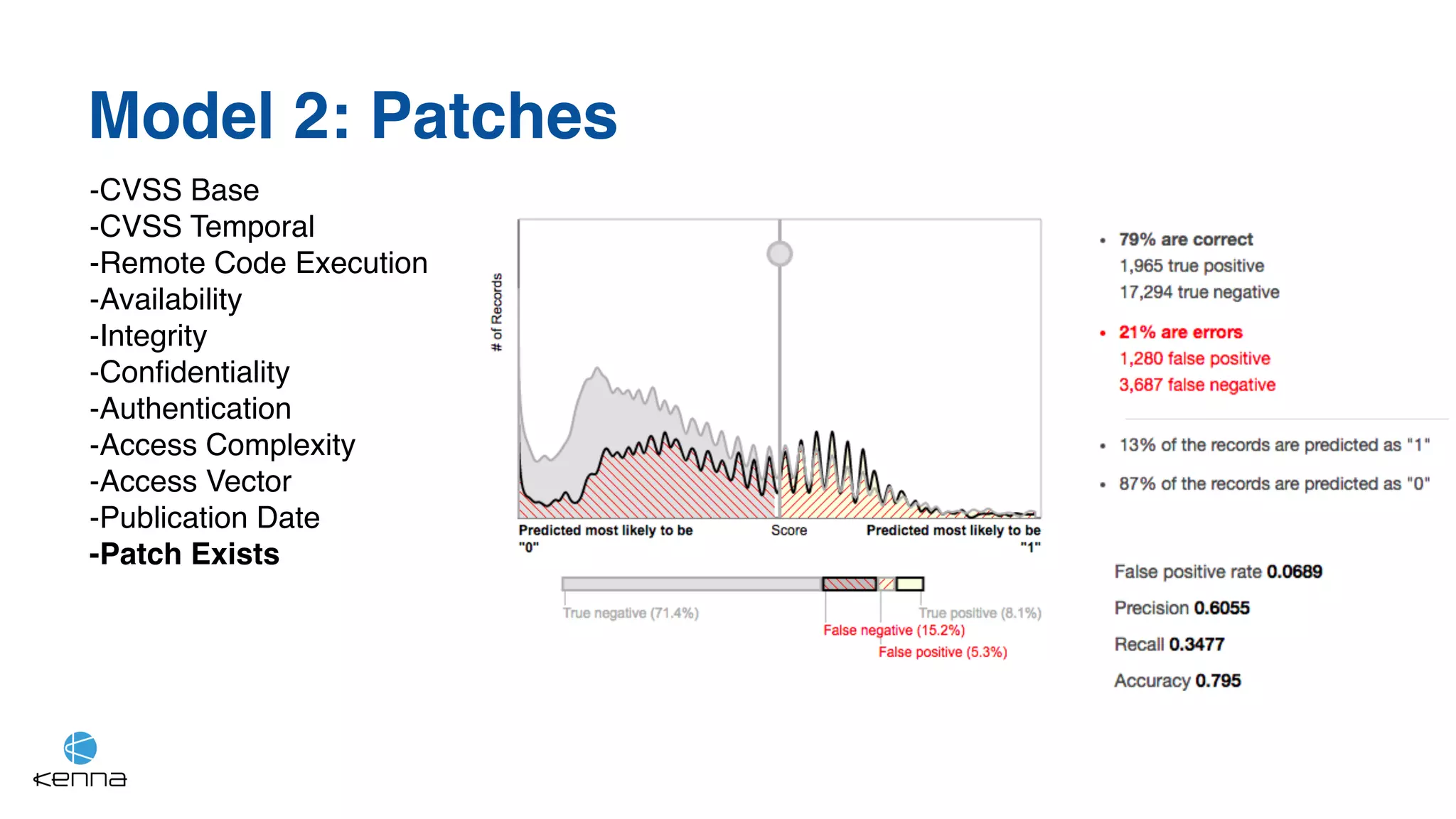
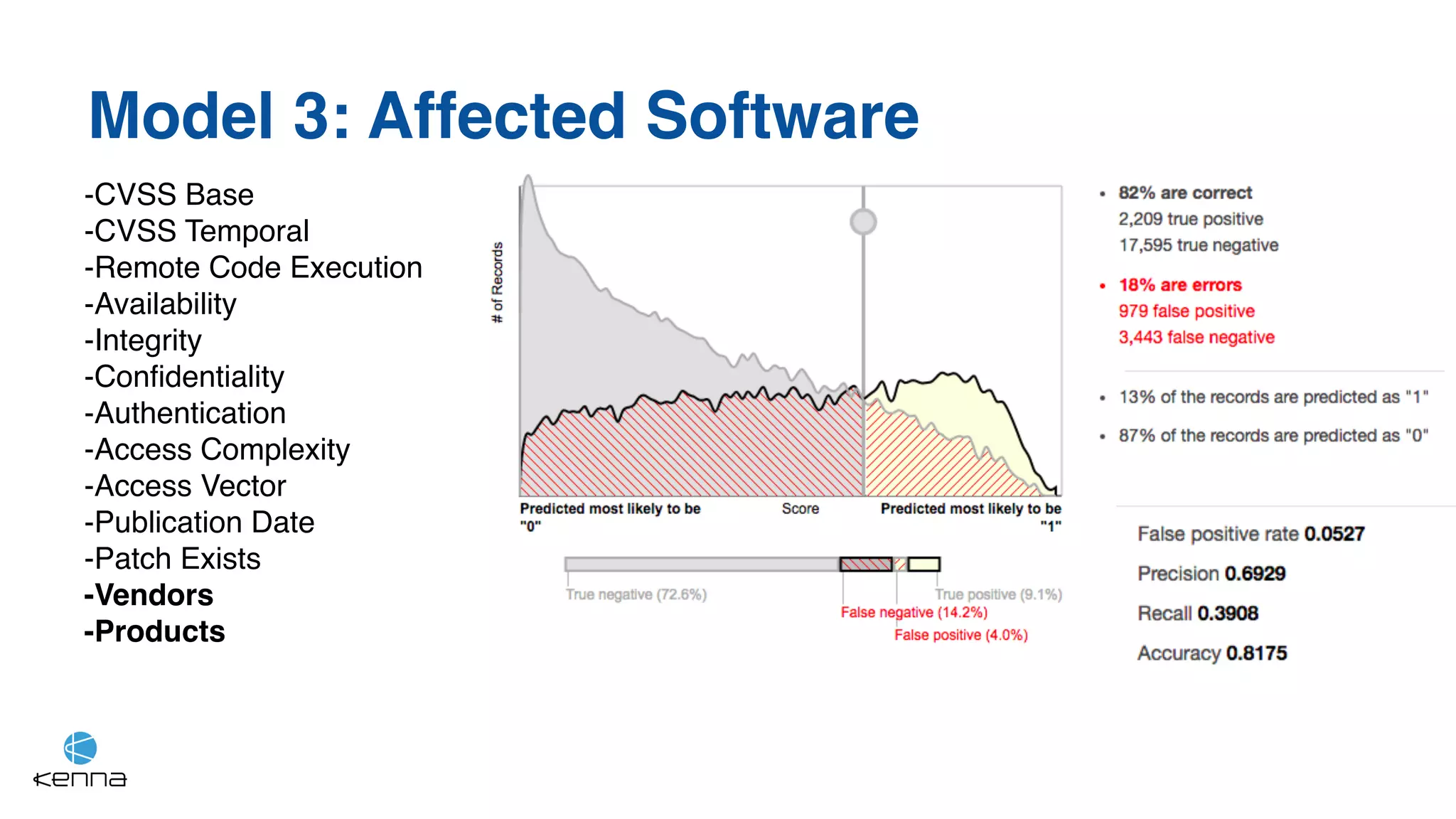
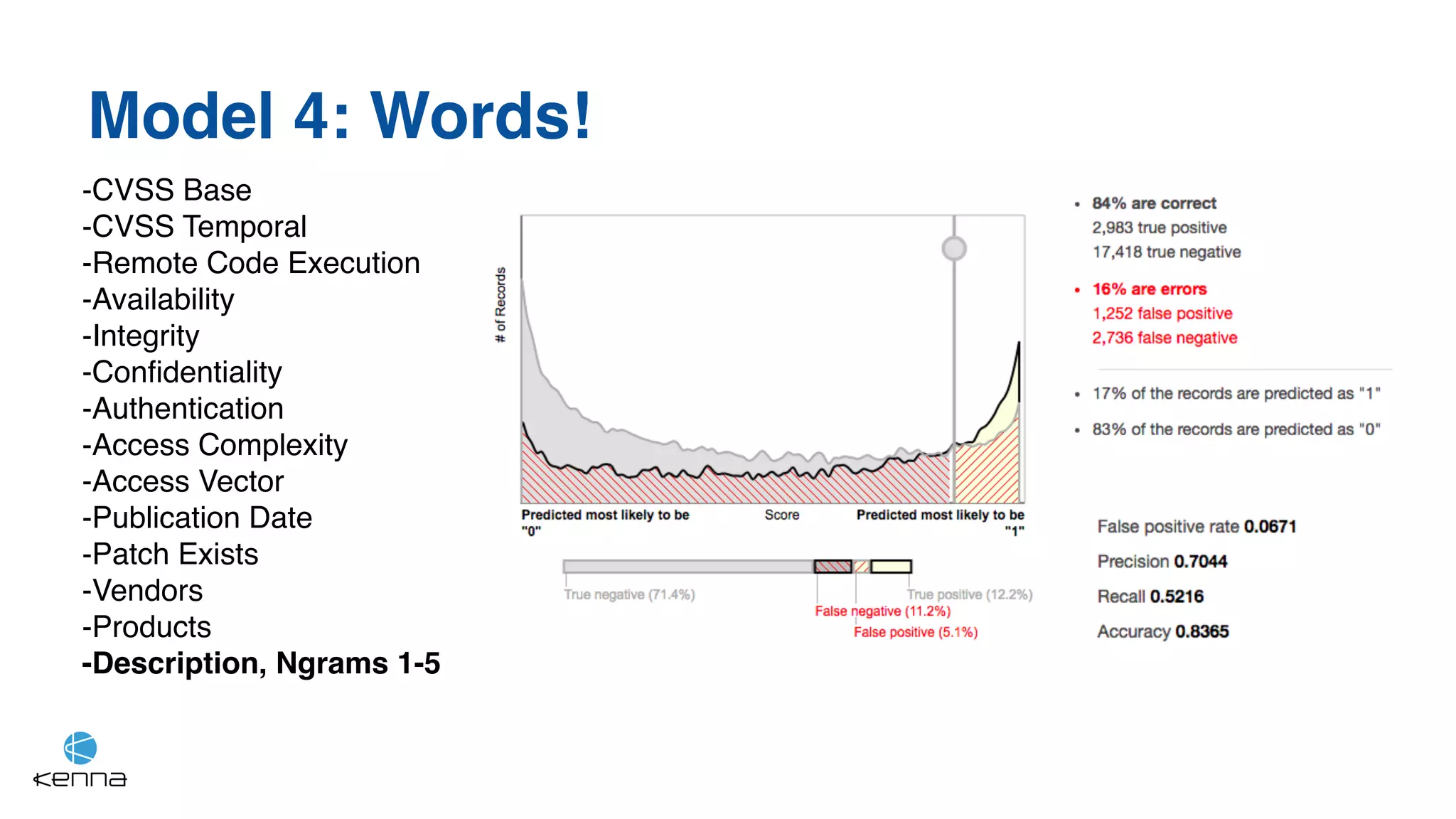
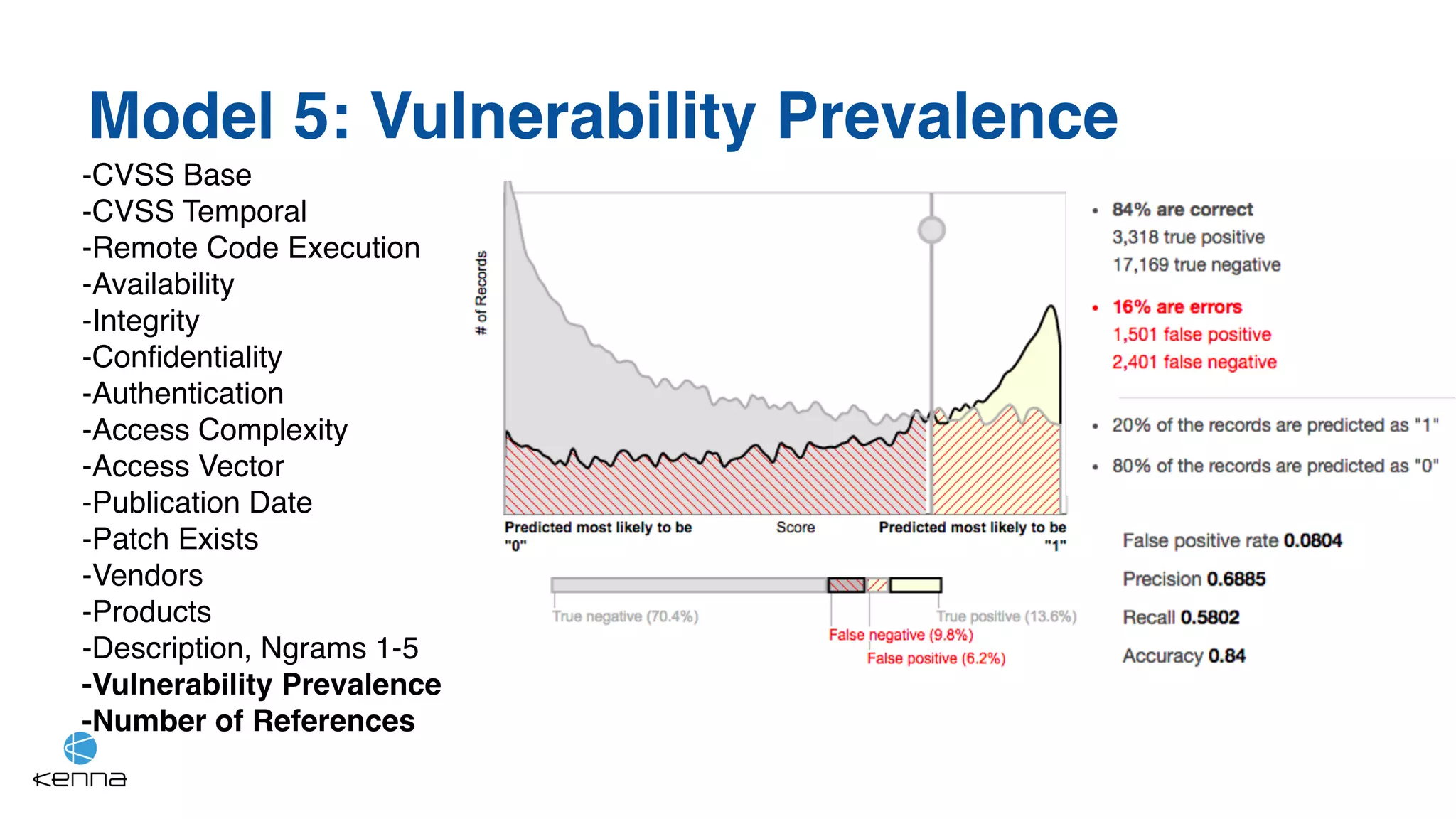
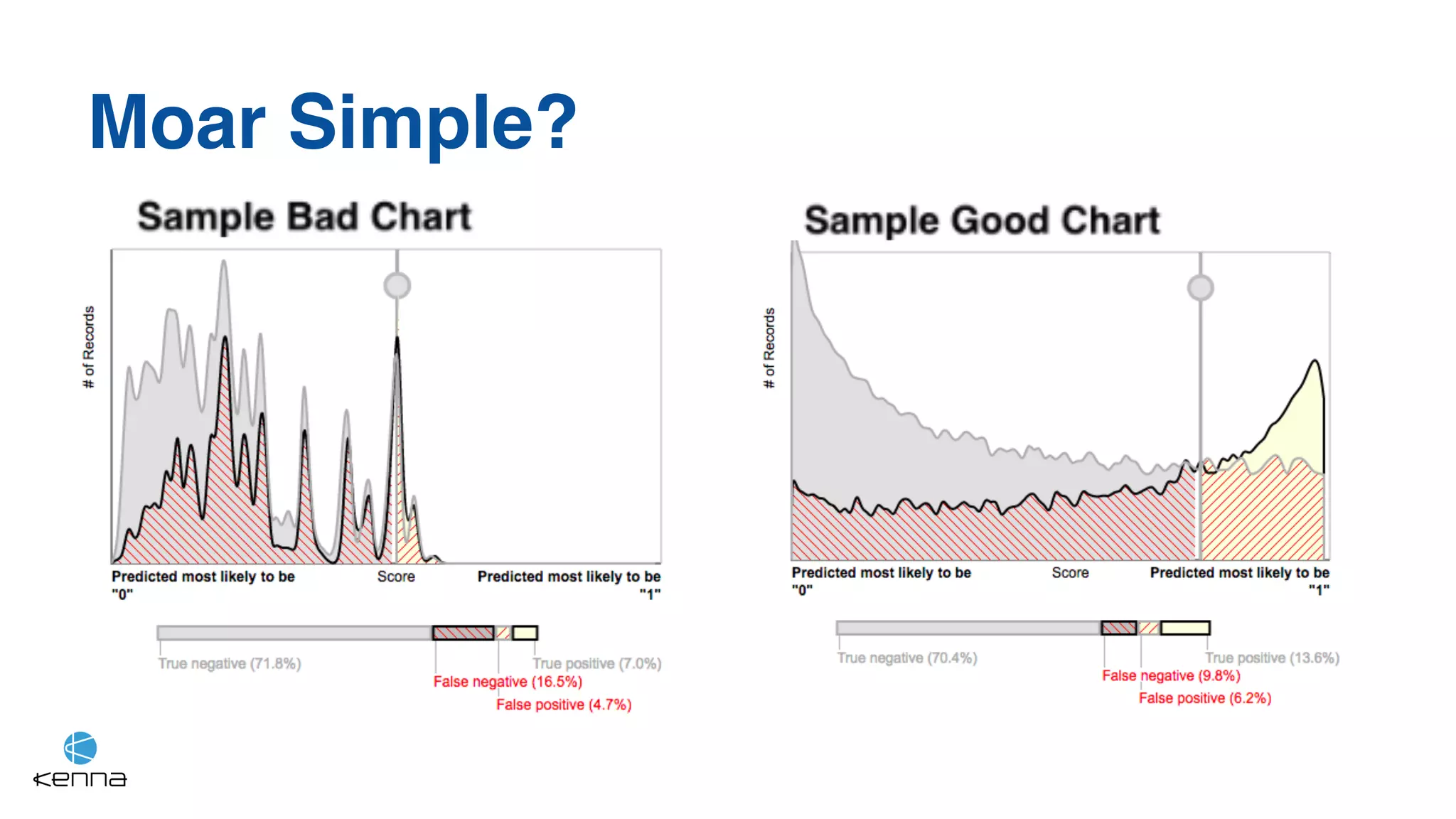
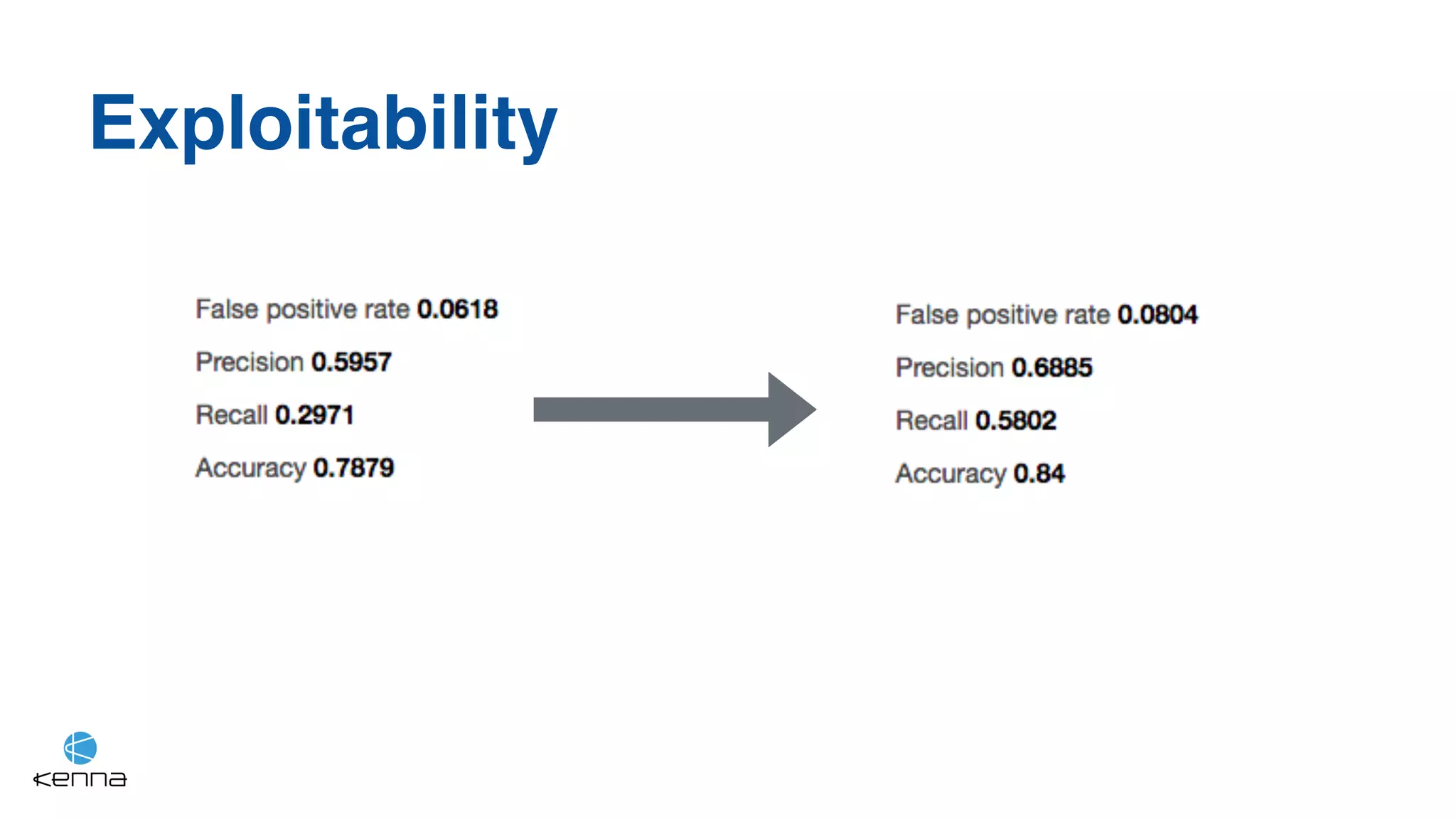
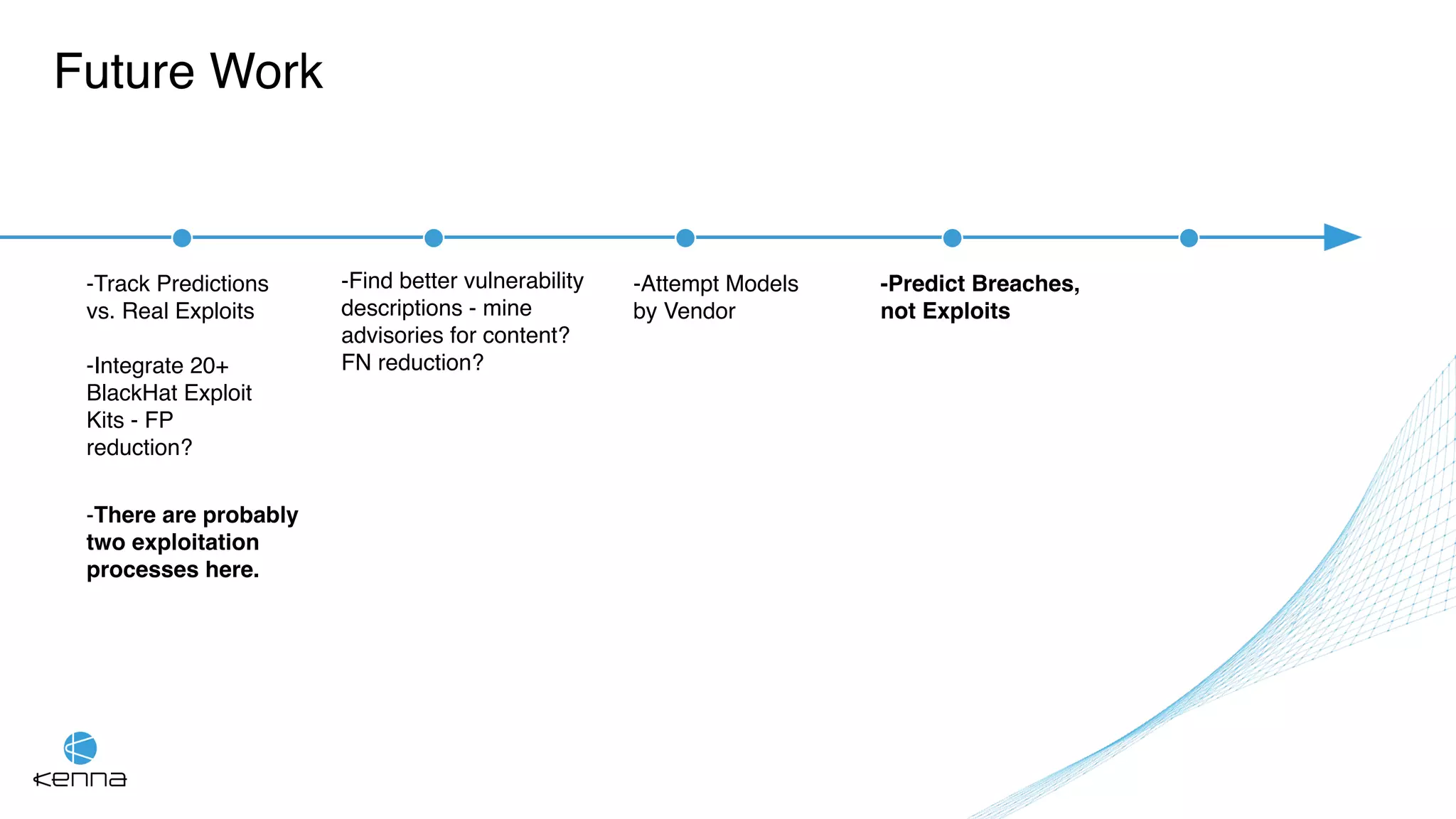
The document discusses strategies for predicting the exploitability of vulnerabilities, focusing on retrospective, real-time, and predictive methodologies. It highlights the use of machine learning models to assess various factors influencing vulnerability management, such as vulnerability prevalence and existing patches. Future work aims to refine these models and predict breaches rather than exploits while integrating data from numerous sources.