Chpt9 patternmatching
•Transferir como PPT, PDF•
2 gostaram•1,560 visualizações
design patterns
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Regular expression to NFA (Nondeterministic Finite Automata)

Regular expression to NFA (Nondeterministic Finite Automata)
Semelhante a Chpt9 patternmatching
WHAT IS PATTERN RECOGNISITION ?
Given a text string T[0..n-1] and a pattern P[0..m-1], find all occurrences of the pattern within the text.
Example: T = 000010001010001 and P = 0001, the occurrences are:
first occurrence starts at T[1]
second occurrence starts at T[5]
third occurrence starts at T[11]
APPLICATION :
Image preprocessing
• Computer vision
• Artificial intelligence
• Radar signal classification/analysis
• Speech recognition/understanding
• Fingerprint identification
• Character (letter or number) recognition
• Handwriting analysis
• Electro-cardiographic signal analysis/understanding
• Medical diagnosis
• Data mining/reduction
ALGORITHM DESCRIPTION
The Knuth-Morris-Pratt (KMP) algorithm:
It was published by Donald E. Knuth, James H.Morris and Vaughan R. Pratt, 1977 in: “Fast Pattern Matching in Strings.“
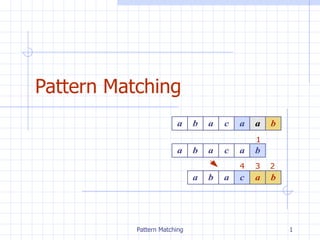
To illustrate the ideas of the algorithm, consider the following example:T = xyxxyxyxyyxyxyxyyxyxyxxy
And P = xyxyyxyxyxx
it considers shifts in order from 1 to n-m, and determines if the pattern matches at that shift. The difference is that the KMP algorithm uses information gleaned from partial matches of the pattern and text to skip over shifts that are guaranteed not to result in a match.
The text and pattern are included in Figure 1, with numbering, to make it easier to follow.
1.Consider the situation when P[1……3] is successfully matched with T[1……..3]. We then find a mismatch: P[4] = T[4]. Based on our knowledge that P[1…… 3] =T[1…… 3], and ignoring symbols of the pattern and text after position 3, what can we deduce about where a potential match might be? In this case, the algorithm slides the pattern 2 positions to the right so that P[1] is lined up with T[3]. The next comparison is between P[2] and T[4].
P: x y x y y x y x y x x
q: 1 2 3 4 5 6 7 8 9 10 11
_(q): 0 0 1 2 0 3
Table 1: Table of values for pattern P.
Time Complexity :
The call to compute prefix is O(m)
using q as the value of the potential function, we argue in the same manner as above to show the loop is O(n)
Therefore the overall complexity is O(m + n)
Boyer-Moore algorithm:
It was developed by Bob Boyer and J Strother Moore in 1977. The algorithm preprocesses the pattern string that is being searched in text string.
String pattern matching - Boyer-Moore:
This algorithm uses fail-functions to shift the pattern efficiently. Boyer-Moore starts however at the end of the pattern, which can result in larger shifts.Two heuristics are used:1: if we encounter a mismatch at character c in Q, we can shift to the first occurrence of c in P from the right:
Q a b c a b c d g a b c e a b c d a c e d
P a b c e b c d
a b c e b c d
(restart here)
Time Complexity:
• performs the comparisons from right to left;
• preprocessing phase in O(m+ ) tIMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM 

IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM NETAJI SUBHASH ENGINEERING COLLEGE , KOLKATA
Semelhante a Chpt9 patternmatching (20)
PatternMatching2.pptnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn

PatternMatching2.pptnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnnn
IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM 

IMPLEMENTATION OF DIFFERENT PATTERN RECOGNITION ALGORITHM
Último
Último (20)
Where to Learn More About FDO _ Richard at FIDO Alliance.pdf

Where to Learn More About FDO _ Richard at FIDO Alliance.pdf
Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...

Event-Driven Architecture Masterclass: Engineering a Robust, High-performance...
The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf

The Value of Certifying Products for FDO _ Paul at FIDO Alliance.pdf
“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf

“Iamnobody89757” Understanding the Mysterious of Digital Identity.pdf
JavaScript Usage Statistics 2024 - The Ultimate Guide

JavaScript Usage Statistics 2024 - The Ultimate Guide
WebRTC and SIP not just audio and video @ OpenSIPS 2024

WebRTC and SIP not just audio and video @ OpenSIPS 2024
Portal Kombat : extension du réseau de propagande russe

Portal Kombat : extension du réseau de propagande russe
Intro to Passkeys and the State of Passwordless.pptx

Intro to Passkeys and the State of Passwordless.pptx
Long journey of Ruby Standard library at RubyKaigi 2024

Long journey of Ruby Standard library at RubyKaigi 2024
How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf

How Red Hat Uses FDO in Device Lifecycle _ Costin and Vitaliy at Red Hat.pdf
Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...

Event-Driven Architecture Masterclass: Integrating Distributed Data Stores Ac...
Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots

Continuing Bonds Through AI: A Hermeneutic Reflection on Thanabots
Simplified FDO Manufacturing Flow with TPMs _ Liam at Infineon.pdf

Simplified FDO Manufacturing Flow with TPMs _ Liam at Infineon.pdf
Using IESVE for Room Loads Analysis - UK & Ireland

Using IESVE for Room Loads Analysis - UK & Ireland
Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx

Harnessing Passkeys in the Battle Against AI-Powered Cyber Threats.pptx
Chpt9 patternmatching
- 8. Example
- 14. Example 0 c 3 1 a 4 2 1 0 j 1 0 0 F ( j ) b a b a P [ j ]