S sdlc datasheet q1-2015 v fnl
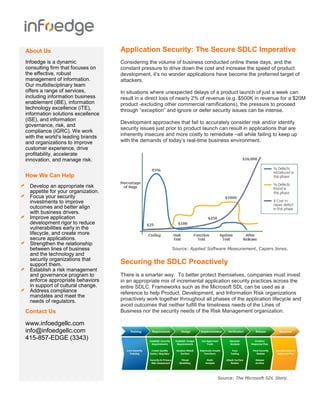
- 1. Application Security: The Secure SDLC Imperative Considering the volume of business conducted online these days, and the constant pressure to drive down the cost and increase the speed of product development, it’s no wonder applications have become the preferred target of attackers. In situations where unexpected delays of a product launch of just a week can result in a direct loss of nearly 2% of revenue (e.g. $500K in revenue for a $20M product -excluding other commercial ramifications), the pressure to proceed through “exception” and ignore or defer security issues can be intense. Development approaches that fail to accurately consider risk and/or identify security issues just prior to product launch can result in applications that are inherently insecure and more costly to remediate –all while failing to keep up with the demands of today’s real-time business environment. Securing the SDLC Proactively There is a smarter way. To better protect themselves, companies must invest in an appropriate mix of incremental application security practices across the entire SDLC. Frameworks such as the Microsoft SDL can be used as a reference to help Product, Development, and Information Risk organizations proactively work together throughout all phases of the application lifecycle and avoid outcomes that neither fulfill the timeliness needs of the Lines of Business nor the security needs of the Risk Management organization. ` About Us Infoedge is a dynamic consulting firm that focuses on the effective, robust management of information. Our multidisciplinary team offers a range of services, including information business enablement (iBE), information technology excellence (iTE), information solutions excellence (iSE), and information governance, risk, and compliance (iGRC). We work with the world’s leading brands and organizations to improve customer experience, drive profitability, accelerate innovation, and manage risk. How We Can Help Develop an appropriate risk appetite for your organization. Focus your security investments to improve outcomes and better align with business drivers. Improve application development rigor to reduce vulnerabilities early in the lifecycle, and create more secure applications. Strengthen the relationship between lines of business and the technology and security organizations that support them. Establish a risk management and governance program to enforce appropriate behaviors in support of cultural change. Address compliance mandates and meet the needs of regulators. Contact Us www.infoedgellc.com info@infoedgellc.com 415-857-EDGE (3343) Source: Applied Software Measurement, Capers Jones. Source: The Microsoft SDL Story.
- 2. Secure Software Development Lifecycle (S-SDLC) Services We understand that different organizations have different requirements and our Secure Software Development Lifecycle approach works for companies at every level of maturity. The S-SDLC service mix delivers a unique set of capabilities to fit each client’s specific security needs and investment appetite. There are four complimentary service offerings that support our approach: Assessment—We work with our clients to thoroughly understand their existing capabilities across the S-SDLC, and then identify opportunities for focused improvement and capability development. Advisory—Using our extensive industry and domain knowledge, we help clients develop practices and apply the most up-to-date S-SDLC thinking across the areas of people, process, and technology. Operationalization—We help our clients implement their S- SDLC strategy using actionable and sustainable program initiatives, coupled with automation activities that ease the developer burden and drive lasting cultural change. Assurance—We help identify impactful business metrics and governance processes that demonstrate the program’s value, and ensure the level of risk management is aligned with the needs of the organization. Examples of Our S-SDLC Services in Action S-SDLC Maturity Assessment S-SDLC Advisory and Operationalization S-SDLC Assessment and Advisory CLIENT CONCERN: Repeated delays in the launch of new products due to late detection of security issues that had to be fixed prior to launch. CLIENT CONCERN: A serious application security bug was released into production without detection, resulting in a potential breach of confidentiality. CLIENT CONCERN: Regulators required additional confidence that the client had taken the right approach to securing applications. OUR SOLUTION: Assessed the service environment and developed new strategies aimed at early notification. Worked with client personnel to implement new services and drive awareness of new touch points and capabilities. OUR SOLUTION: Performed root cause analysis and identified the service gap. Developed capability integration service models and strategy for more effective partnering. Worked with client to implement solution. OUR SOLUTION: Worked with client to develop a multi-year S-SDLC roadmap. Developed and led the implementation of several services across a variety of development approaches (e.g. Agile & Waterfall) and third- party support structures. CLIENT IMPACT: Improved client’s relationship with peers and partners. Reduced the number of last- minute findings and therefore the extent of delays. CLIENT IMPACT: Avoided significant costs and risks by enhancing existing capabilities and integrating new ones. CLIENT IMPACT: Avoided regulatory action, and jump-started an enterprise-wide security transformation across all phases of the application lifecycle.
