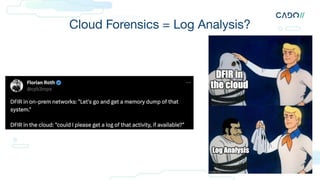
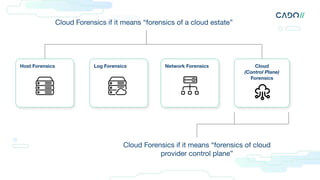
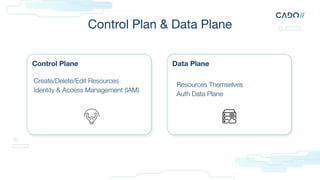
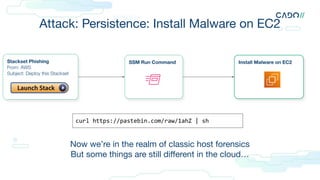
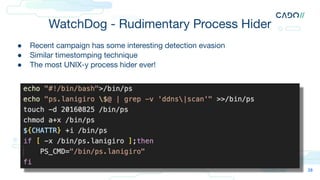
The document discusses cloud forensics, emphasizing the importance of analyzing both logs and resources for incident response in cloud environments. It highlights various forensic techniques, cloud incident domains, and the necessity of establishing standards for audit logging and preservation in the cloud. Additionally, it examines case studies involving cloud attacks and best practices for managing cloud security logs and resources effectively.











![SSM “Official” Logs
Logs live under /var/log/amazon/ssm/
Can forward with CloudWatch Agent/SIEM
Or pull from disk
More for diagnostics
Generally not that useful for security
2021-06-08 11:15:14 INFO [ssm-agent-worker]
[MessagingDeliveryService] received plugin:
aws:runShellScript result from Processor
2021-06-08 11:15:14 INFO [ssm-agent-worker]
[MessagingDeliveryService] Sending reply {
"additionalInfo": {
"agent": {
amazon-ssm-agent.log](https://image.slidesharecdn.com/sansanewperspectiveonresource-levelcloudforensics-230805155626-95ab1674/85/A-New-Perspective-on-Resource-Level-Cloud-Forensics-18-320.jpg)
![Undocumented SSM Logs
sh-4.2$
[ec2-user@ip-10-0-2-54 ~]$ ls
key
[ec2-user@ip-10-0-2-54 ~]$ aws s3 cp staff.txt
s3://eu-west-1-prod-data --region eu-west-1
Completed 802 Bytes/802 Bytes (9.4 KiB/s) with 1
file(s) remaining
[ec2-user@ip-10-0-2-54 ~]$ logout
sh-4.2$ exit
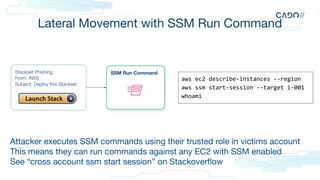
The best data is in an undocumented log called
ipcTempFile.log
Contains full session data, both directions
Credit to Al & Korstiaan for the discovery
Linux:
/var/lib/amazon/ssm/<EC2-INSTANCE-ID>/ses
sion/orchestration/<USER>-<RANDOM ID>/
Windows:
C:ProgramDataAmazonSSMInstanceData<
EC2 INSTANCE ID>sessionorchestration
ipcTempFile.log
See “IPC YOU: How the Cado Platform Reveals Attacker Command Outputs” by Cado Security](https://image.slidesharecdn.com/sansanewperspectiveonresource-levelcloudforensics-230805155626-95ab1674/85/A-New-Perspective-on-Resource-Level-Cloud-Forensics-19-320.jpg)








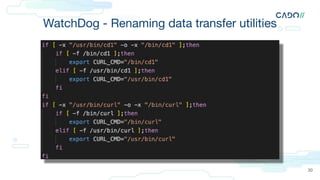










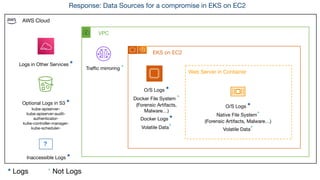


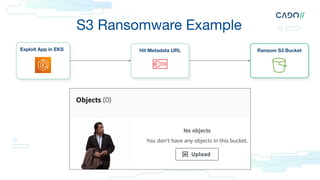




![Make sure your cloud logs are turned on
● “Logging in the Cloud: From Zero to (Incident Response) Hero”
by Jonathon Poling [AWS, GCP, Azure]
● https://github.com/prowler-cloud/prowler [AWS, GCP, Azure]
● Spreadsheet of where each services logs: https://bit.ly/3XidVm3 [AWS]
● https://github.com/awslabs/assisted-log-enabler-for-aws [AWS]
● FOR509](https://image.slidesharecdn.com/sansanewperspectiveonresource-levelcloudforensics-230805155626-95ab1674/85/A-New-Perspective-on-Resource-Level-Cloud-Forensics-49-320.jpg)


