Tests
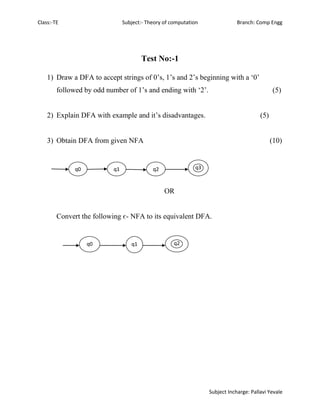
- 1. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale Test No:-1 1) Draw a DFA to accept strings of 0’s, 1’s and 2’s beginning with a ‘0’ followed by odd number of 1’s and ending with ‘2’. (5) 2) Explain DFA with example and it’s disadvantages. (5) 3) Obtain DFA from given NFA (10) OR Convert the following є- NFA to its equivalent DFA. q0 q1 q2 q3 q0 q1 q2
- 2. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale Test No:-2 1. Attempt any five. (5) a) Obtain a regular expression to accept the strings of 0’s and 1’s having no two consecutive 0’s. b) Obtain a regular expression to accept the strings of a’s and b’s starting with ‘a’ and ending with ‘b’. c) Obtain a regular expression to accept the strings of a’s and b’s whose second symbol from the right end is ‘a’.’ d) Obtain a regular expression to accept the strings of a’s and b’s such that 3rd symbol from the right is ‘a’ and 4th symbol the right end is ‘b’. e) Obtain a regular expression to accept the words with two or more letters but beginning and ending with same letter where ∑ = {a,b} f) Obtain a regular expression for the language L={an bm | m+n is even} g) Obtain a regular expression for the language L={an bm | m≥1,n≥ 1,nm≥ 3} 2. Following FA recognize the languages L1 and L2. Draw FA recognizing language L1- L2 (5) M1 M2
- 3. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale 3. Minimize the number of states of following FA. (10) OR Find out the regular expression of following FA’s. δ a b A B A B A C C D B *D D A E D F F G E G F G H G D δ a b *1 1 2 *2 1 3 3 1 2
- 4. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale Test No:-3 Solve any two Questions. 1. Obtain the grammar for the following FA. [10] a. Obtain grammar to generate string consisting of any number of a’s. b. Obtain grammar to generate string consisting of at least one a. c. Obtain grammar to generate string consisting of any number of a’s and b’s. d. Obtain grammar to generate string consisting of at least two a’s. e. Obtain grammar to generate string consisting of even number of a’s. 2. A) Is the following grammar ambiguobs? [5] S→ AB | aaB A→ a | Aa B→ b B) Eliminate the useless symbols from the following grammar. [5] S→ aA | bB A→ aA | a B→ bB D→ ab | Ea E→ ac | d
- 5. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale 3. A) Eliminate all unit productions From the grammar [5] S→ AB A→ a B→ C | b C→ D D→ E | bc E→ d | Ab B) Convert the following grammar into CNF. [5] S→ 0A | B A→ 0AA | 1S | 1 B→ 1BB | 0S | 0
- 6. Class:-TE Subject:- Theory of computation Branch: Comp Engg Subject Incharge: Pallavi Yevale Test No:-4 1. Explain a. Definition of PDA [4] b. Acceptance of PDA [2] 2. Design a DPDA for a binary number divisible by 3. [6] 3. Construct the PDA from the following CFG for the language L={ x є {a,b}*| na(x) >nb(x)} [8] S a |aS | bSS | SSb | SbS And show the sequence of moves to accept the string abbaaa. OR Write the rules for converting the PDA to CFG and obtain CFG form following PDA. [8] Moves no. State Input Stack symbols Moves 1 q0 a Z0 (q0,AZ0) 2 q0 b Z0 (q0,BZ0) 3 q0 a A (q0,AA) 4 q0 b A (q0,BA) 5 q0 a B (q0,AB) 6 q0 b B (q0,BB) 7 q0 c Z0 (q1,Z0) 8 q0 c A (q1,A) 9 q0 c B (q1,B) 10 q1 a A (q1, є) 11 q1 b B (q1, є) 12 q1 є Z0 (q1, є)
