Network Routing Protocols and IPv4 Addressing
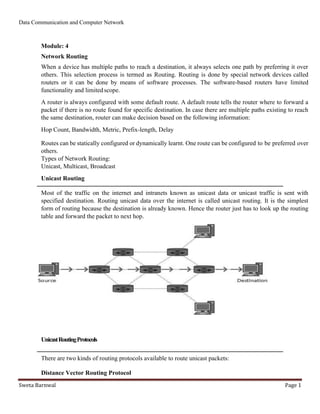
- 1. Data Communication and Computer Network Sweta Barnwal Page 1 Module: 4 Network Routing When a device has multiple paths to reach a destination, it always selects one path by preferring it over others. This selection process is termed as Routing. Routing is done by special network devices called routers or it can be done by means of software processes. The software-based routers have limited functionality and limitedscope. A router is always configured with some default route. A default route tells the router where to forward a packet if there is no route found for specific destination. In case there are multiple paths existing to reach the same destination, router can make decision based on the following information: Hop Count, Bandwidth, Metric, Prefix-length, Delay Routes can be statically configured or dynamically learnt. One route can be configured to be preferred over others. Types of Network Routing: Unicast, Multicast, Broadcast Unicast Routing Most of the traffic on the internet and intranets known as unicast data or unicast traffic is sent with specified destination. Routing unicast data over the internet is called unicast routing. It is the simplest form of routing because the destination is already known. Hence the router just has to look up the routing table and forward the packet to next hop. UnicastRoutingProtocols There are two kinds of routing protocols available to route unicast packets: Distance Vector Routing Protocol
- 2. Data Communication and Computer Network Sweta Barnwal Page 2 Distance Vector is simple routing protocol which takes routing decision on the number of hops between source and destination. A route with a smaller number of hops is considered as the best route. Every router advertises its set best routes to other routers. Ultimately, all routers build up their network topology based on the advertisements of their peer routers, for example, Routing Information Protocol (RIP). Link State Routing Protocol Link State protocol is slightly complicated protocol than Distance Vector. It takes into account the states of links of all the routers in a network. This technique helps routes build a common graph of the entire network. All routers then calculate their best path for routing purposes, for example, Open Shortest Path First (OSPF) and Intermediate System to Intermediate System (ISIS). IPv4 The network layer is the third layer (from bottom) in the OSI Model. The network layer is concerned with the delivery of a packet across multiple networks. The network layer is considered the backbone of the OSI Model. It selects and manages the best logical path for data transfer between nodes. This layer contains hardware devices such as routers, bridges, firewalls, and switches, but it actually creates a logical image of the most efficient communication route and implements it with a physical medium. Network layer protocols exist in every host or router. The router examines the header fields of all the IP packets that pass through it. Internet Protocol and Netware IPX/SPX are the most common protocols associated with the network layer. In the OSI model, the network layer responds to requests from the layer above it (transport layer) and issues requests to the layer below it (data link layer). IPv4 is a connectionless protocol used for packet switched networks. It operates on a best effort delivery model, in which neither delivery is guaranteed, nor is proper sequencing or avoidance of duplicate delivery assured. Internet Protocol Version 4 (IPv4) is the fourth revision of the Internet Protocol and a widely used protocol in data communication over different kinds of networks. IPv4 is a connectionless protocol used in packet-switched layer networks, such as Ethernet. It provides a logical connection between network devices by providing identification for each device. There are many ways to configure IPv4 with all kinds of devices – including manual and automatic configurations – depending on the network type.
- 3. Data Communication and Computer Network Sweta Barnwal Page 3 IPv4 uses 32-bit addresses for Ethernet communication in five classes: A, B, C, D and E. Classes A, B and C have a different bit length for addressing the network host. Class D addresses are reserved for military purposes, while class E addresses are reserved for future use. IPv4 uses 32-bit (4 byte) addressing, which gives 232 addresses. IPv4 addresses are written in the dot- decimal notation, which comprises of four octets of the address expressed individually in decimal and separated by periods, for instance, 192.168.1.5. VERSION: Version of the IP protocol (4 bits), which is 4 for IPv4 HLEN: IP header length (4 bits), which is the number of 32 bit words in the header. The minimum value for this field is 5 and the maximum is 15 Type of service: Low Delay, High Throughput, Reliability (8 bits) Total Length: Length of header + Data (16 bits), which has a minimum value 20 bytes and the maximum is 65,535 bytes Identification: Unique Packet Id for identifying the group of fragments of a single IP datagram (16 bits) Flags: 3 flags of 1 bit each : reserved bit (must be zero), do not fragment flag, more fragments flag (same order) Fragment Offset: Represents the number of Data Bytes ahead of the particular fragment in the particular Datagram. Specified in terms of number of 8 bytes, which has the maximum value of 65,528 bytes Time to live: Datagram’s lifetime (8 bits), It prevents the datagram to loop through the network by restricting the number of Hops taken by a Packet before delivering to the Destination. Protocol: Name of the protocol to which the data is to be passed (8 bits) Header Checksum: 16 bits header checksum for checking errors in the datagram header Source IP address: 32 bits IP address of the sender Destination IP address: 32 bits IP address of the receiver Option: Optional information such as source route, record route. Used by the Network administrator to check whether a path is working or not. Internet Control Message Protocol (ICMP) ICMP is network diagnostic and error reporting protocol. ICMP belongs to IP protocol suite and uses IP as carrier protocol. After constructing ICMP packet, it is encapsulated in IP packet. Because IP itself is a best-effort non-reliable protocol, so is ICMP. Any feedback about network is sent back to the originating host. If some error in the network occurs, it is reported by means of ICMP. ICMP contains dozens of diagnostic and error reporting messages. ICMP-echo and ICMP-echo-reply are the most commonly used ICMP messages to check the reachability of end-to-end hosts. When a host receives an ICMP-echo request, it is bound to send back an ICMP-echo-reply. If there is any problem in the transit network, the ICMP will report that problem. Internet Control Message Protocol (both ICMPv4 and ICMPv6) is a protocol which acts as a communication messenger protocol between the communicating devices in IP network. ICMP messages provide feedback, error reporting and network diagnostic functions in IP networks which are necessary for the smooth operation of IPv6. ICMPv6 is an integral part of IPv6 and ICMPv6 protocol in IPv6 and has much more importance and functions than ICMPv4 protocol in IPv4. Main functions of ICMPv6 are listed below. • Error Reporting
- 4. Data Communication and Computer Network Sweta Barnwal Page 4 • Network Diagnostics • Neighbor Discovery • Multicast Membership Reporting • Router Solicitation and Router Advertisements ICMPv6 removed the ICMPv4 functions that are obsolete and took over the functions of two major IPv4 protocols IGMP (Internet Group Membership Protocol) and ARP (Address Resolution Protocol). IGMP and ARP are no more with IPv6. ICMPv6 messages are encapsulated with IPv6 datagram packets as shown below. ICMPv6 Message Packet Format ICMPv6 messages can be classified into ICMPv6 error messages and ICMPv6 information messages. ICMPv6 Error Messages ICMPv6 error messages are used to report errors in the forwarding or delivery of IPv6 packets. The ICMPv6 "Type field" values for the error message are between 0 and 127. ICMPv6 error messages are Destination Unreachable, Packet Too Big, Time Exceeded, and Parameter Problem. "Destination Unreachable" ICMPv6 error message: Destination Unreachable ICMPv6 error message is generated by the source host or a router when an IPv6 datagram packet cannot be delivered for any reason other than congestion.
- 5. Data Communication and Computer Network Sweta Barnwal Page 5 "Packet Too Big" ICMPv6 error message: "Packet Too Big" ICMPv6 error messages are generated by the router when a packet cannot be forwarded to the next hop link because the size of the IPv6 datagram is larger than the MTU (Maximum Transmission Unit) of the link. "Packet Too Big" ICMPv6 error message includes the MTU (Maximum Transmission Unit) of the next link also. MTU (Maximum Transmission Unit) is the size of the largest protocol data unit that is supported over the link. "Time Exceeded" ICMPv6 error message: Similar to the Time-to-Live field value in IPv4 datagram header, IPv6 header includes a Hop Limit field. The Hop Limit field value in IPv6 header is used to prevent routing loops. Hop Limit field in IPv6 datagram header is decremented by each router that forwards the packet. When the Hop Limit field value in IPv6 header reaches zero, the router discards the IPv6 datagram packet and returns a "Time Exceeded" ICMPv6 error message to the source host. "Parameter Problem" ICMPv6 error message: "Parameter Problem" ICMPv6 error message is typically related with the problems and mistakes related with IPv6 header itself. When a problem or mistake with an IPv6 header make a router cannot process the packet, the router stops processing the IPv6 datagram packet, discards the packet and returns a "Parameter Problem" ICMPv6 error message to the source host. ICMPv6 informational messages ICMPv6 informational messages are used for network diagnostic functions and additional critical network functions like Neighbor Discovery, Router Solicitation & Router Advertisements, Multicast Memberships. Echo Request and Echo Reply (used by many commands and utilities like "ping" for network diagnostics and communication trouble shooting) are also ICMPv6 informational messages. The ICMPv6 informational messages have values for the Type field (8 bit binary number) between 128 and 255. Diagnostic Messages: ICMPv6 Echo request and Echo reply are the Diagnostic messages. Every IPv6 host must return an ICMPv6 Echo reply when it receives an ICMPv6 Echo request. Echo request and Echo reply messages are used by the ping command to check the network connectivity between two IPv6 hosts. MLD (Multicast Listener Discovery) Messages: ICMPv6 MLD (Multicast Listener Discovery) Messages are used by an IPv6 enabled router to discover hosts who are interested in multicast packets, and the multicast addresses they are interested. MLD (Multicast Listener Discovery) messages are used by MLD (Multicast Listener Discovery) Protocol. MLD (Multicast Listener Discovery) Protocol is the IPv6 equivalent of IGMP (Internet Group Management) Protocol in IPv4. ND (Neighbor Discovery) Messages: ICMPv6 ND (Neighbor Discovery) Messages are used for the Neighbor Discovery Protocol (NDP). ND (Neighbor Discovery) Messages includes Router Solicitation & Router Advertisement, Neighbor Solicitation and Neighbor Advertisement. Internet Protocol Version 4 (IPv4) IPv4 is 32-bit addressing scheme used as TCP/IP host addressing mechanism. IP addressing enables every host on the TCP/IP network to be uniquely identifiable. IPv4 provides hierarchical addressing scheme which enables it to divide the network into sub- networks, each with well-defined number of hosts. IP addresses are divided into many categories: Class A: It uses first octet for network addresses and last three octets for host addressing. Class B: It uses first two octets for network addresses and last two for host addressing. Class C: It uses first three octets for network addresses and last one for host addressing. Class D: It provides flat IP addressing scheme in contrast to hierarchical structure for above three. Class E: It is used as experimental.
- 6. Data Communication and Computer Network Sweta Barnwal Page 6 IPv4 also has well-defined address spaces to be used as private addresses (not routable on internet), and public addresses (provided by ISPs and are routable on internet). Though IP is not reliable one; it provides ‘Best-Effort-Delivery’ mechanism. IPv6 IPV6 is also known as IPng (Internetworking Protocol, next generation). The numbers of users of the internet are increasing day by day and the services offered to these users are also increasing. A huge number of addresses are needed to accommodate such vast number of hosts. The internet not only transmits textual data. It also allows us to transmit audio and video data. In such data, the high speed data transfer is desired. Internet working protocol version 6 (IPv6) was developed to overcome the shortcomings of IPv4. The problem of address depletion, lack of accommodation for real-time audio and video transmission , and encryption and authentication of data for some applications motivated the development of IPv6. The internet protocol version 4 is being used in the current internet. The internet protocol version 6 has been designed for the future needs of the internet. IPv6 has following new features to make the network ready for next generation of the internet. (i) IPv6 address is 128 bits long. This is far more than 32 bit long addresses used by Ipv4. This provides 296 more unique addresses (ii) Ipv6 header has got separate options field. This speeds up the routing as most of the times, options are not needed. (iii) Several new options have been added to set of options. (iv) To accommodate the real time traffic, the Ipv6 uses Flow Label field instead of Type of Service field of Ipv4. With this field, a user can request for the type of service to be given to the datagram. (v) The Ipv6 contains options for encryption and decryption of data. This provides additional security to the information. In this protocol, the IP address is of 128 bits long. The address is divided into eight sections of 16 bits in length. Each 16 bit section is represented by four hexadecimal digits. A colon is used to separate every four hexadecimal digits. This way, the address consists of 32 hexadecimal digits. Structure of IPv6 Hexadecimal colon notation • An IPv6 address consists of 16 bytes (octets) • Thus an IPv6 address is 128 bits long • It uses hexadecimal colon notation. • In this notation 128 bits is divided into eight sections. Each section is 2 bytes long. • Two bytes in hexadecimal notation require four hexadecimal digits. Thus, the address consists of 32 hexadecimal digits, with every four digits separated by a colon. Abbreviation • We can also write the IP address in abbreviated form. This can be done by omitting the leading zeros of a section (four digits between two colons) • In such a form, only leading zero can be omitted and not the trailing zeros. • Using this form of abbreviation, 0074 can be written as 74, 000F as F, and 000 as 0.Note 3210 cannot be abbreviated.
- 7. Data Communication and Computer Network Sweta Barnwal Page 7 • Further abbreviations are also possible if there are consecutive sections consisting of zeros only. Using this scheme, zeros can be removed altogether and can be replaced with a double colon. • Such a kind of abbreviation is allowed only once per address. If there are two runs of zero sections only one of them can be abbreviated. • For example, if the address is 0 : 15 : : 1 : 12 : 1213, it would be expanded to its original form. Address space • The address space- of IPv6 is much larger as compared to IPv4. • In IPv6 2128 addresses are available • The IPv6 address is divided into several categories. • The category of address can be determined from the few leftmost bits of address. These leftmost bits that determine the category of address is called type prefix.
- 8. Data Communication and Computer Network Sweta Barnwal Page 8 • The type prefix is variable in length and is designed in such a way that no code is identical to the first part of any other code. • Table below shows the prefix for each type of address. The third column shows the fraction of each type of address relative to the whole address space. Packet format • Each IPv6 packet consists of a mandatory base header. This based header is of 40 • Base header is followed by the payload field. • The payload consists of two parts: extension header and data from an upper layer. • The use of extension header is optional. • The extension header and data from upper layer contain up to 65,536 bytes of information. • There are 8 fields in the base header. These are: 1. Version: This four bit field indicates the version of internet protocol which is 6 for IPv6. 2. Priority: This four bit field specifies the priority of level of the packet with respect to traffic congestion. It specifies the class of traffic to which the IP packet belongs. 3. Flow Label: This is a 3 byte (24 bit) field. It is used to identify all the packet in an individual flow. A flow is uniquely identified by a combination of source address, destination address and a non-zero flow label. Thus, all the packets that are part of the same flow are assigned the same label by the source. 4. Payload length: This 2 byte field indicates the number of octets present in the payload. 5. Next header: The next header is an 8 bit field and describes the header that follows the base header in datagram. The next can be an extension header or header of the upper layer. 6. HOP limit: This 8-bit field has the same function as TTL in IPv4. In IPv6, it is decremented by one on each hop. 7. Source address: This field is of 16 byte (128 bit) and identifies the original source of datagram. 8. Destination address: This 16 byte (128-bit) field determines the final destination of the datagram. Difference between IPv4 vs. IPv6 Basis for differences IPv4 IPv6 Size of IP IPv4 is a 32-Bit IP IPv6 is 128 Bit IP Address.
- 9. Data Communication and Computer Network Sweta Barnwal Page 9 address Address. Addressing method IPv4 is a numeric address, and its binary bits are separated by a dot (.) IPv6 is an alphanumeric address whose binary bits are separated by a colon (:). It also contains hexadecimal. Number of header fields 12 8 Length of header filed 20 40 Checksum Has checksum fields Does not have checksum fields Example 12.244.233.165 2001:0db8:0000:0000:0000:ff00:0042:7879 Type of Addresses Unicast, broadcast, and multicast. Unicast, multicast, and anycast. Number of classes IPv4 offers five different classes of IP Address. Class A to E. lPv6 allows storing an unlimited number of IP Address. Configuration You have to configure a newly installed system before it can communicate with other systems. In IPv6, the configuration is optional, depending upon on functions needed. VLSM support IPv4 support VLSM (Virtual Length Subnet Mask). IPv6 does not offer support for VLSM. Fragmentation Fragmentation is done by sending and forwarding routes. Fragmentation is done by the sender. Routing Information Protocol (RIP) RIP is a routing protocol supported by the routed daemon. RIP does not support IPv6. It uses static routes. Network Configuration Networks need to be configured either manually or with DHCP. IPv4 had IPv6 support autoconfiguration capabilities.
- 10. Data Communication and Computer Network Sweta Barnwal Page 10 several overlays to handle Internet growth, which require more maintenance efforts. Best feature Widespread use of NAT (Network address translation) devices which allows single NAT address can mask thousands of non-routable addresses, making end-to-end integrity achievable. It allows direct addressing because of vast address Space. Address Mask Use for the designated network from host portion. Not used. SNMP SNMP is a protocol used for system management. SNMP does not support IPv6. Mobility & Interoperability Relatively constrained network topologies to which move restrict mobility and interoperability capabilities. IPv6 provides interoperability and mobility capabilities which are embedded in network devices. Security Security is dependent on applications - IPv4 was not designed with security in mind. IPSec(Internet Protocol Security) is built into the IPv6 protocol, usable with a proper key infrastructure. Packet size Packet size 576 bytes required, fragmentation optional 1208 bytes required without fragmentation Packet fragmentation Allows from routers and sending host Sending hosts only Packet header Does not identify packet flow for QoS handling which includes checksum Packet head contains Flow Label field that specifies packet flow for QoS handling
- 11. Data Communication and Computer Network Sweta Barnwal Page 11 Advantages of IPv6 options. DNS records Address (A) records, maps hostnames Address (AAAA) records, maps hostnames Address configuration Manual or via DHCP Stateless address autoconfiguration using Internet Control Message Protocol version 6 (ICMPv6) or DHCPv6 IP to MAC resolution Broadcast ARP Multicast Neighbour Solicitation Local subnet Group management Internet Group Management Protocol GMP) Multicast Listener Discovery (MLD) Optional Fields Has Optional Fields Does not have optional fields. But Extension headers are available. IPSec Internet Protocol Security (IPSec) concerning network security is optional Internet Protocol Security (IPSec) Concerning network security is mandatory Dynamic host configuration Server Clients have approach DHCS (Dynamic Host Configuration server) whenever they want to connect to a network. A Client does not have to approach any such server as they are given permanent addresses. Mapping Uses ARP(Address Resolution Protocol) to map to MAC address Uses NDP(Neighbour Discovery Protocol) to map to MAC address Combability with mobile devices IPv4 address uses the dot- decimal notation. That's why it is not suitable for mobile networks. IPv6 address is represented in hexadecimal, colon- separated notation. IPv6 is better suited to mobile networks.
- 12. Data Communication and Computer Network Sweta Barnwal Page 12 The various advantages of IPv6 over IPv4 are: 1. Larger address space: An IPv6 address is 128 bit long as compared to 32- bit address ofIPv4. It has huge 296 increases in the address space. 2. Allowance for extension: IPv6 is designed to allow the extension of the protocol if required by new technologies or applications. 3. Better header format: IPv6 uses a new header format in which options are separated from the base header and inserted, when needed, between the base header and upper-layer data. 4. New options: IPv6 has new options to allow for additional functionalities. 5. Support for more security: The encryption and authentication options in IPv6 provide confidentiality and integrity of the packet. 6. Support for resource allocation: In IPv6, the source can request the special handling of the packet with the help of flow label field. This mechanism can be used to support traffic such as real-time audio and video. IPv4 & IPv6 are both addresses that are used to identify machines connected to a network. In principle, they are the same, but they are different in how they work. IPv4 and IPv6 cannot communicate with other but can exist together on the same network. This is known as Dual Stack. Transition from IPv4 to IPv6 address When we want to send a request from an IPv4 address to an IPv6 address but it isn’t possible because IPv4 and IPv6 transition is not compatible. For solution to this problem, we use some technologies. These technologies are: Dual Stack Routers, Tunneling, and NAT Protocol Translation. These are explained as following below. Dual Stack Routers: In dual stack router, A router’s interface is attached with Ipv4 and IPv6 addresses configured is used in order to transition from IPv4 to IPv6.
- 13. Data Communication and Computer Network Sweta Barnwal Page 13 In this above diagram, A given server with both IPv4 and IPv6 address configured can communicate with all hosts of IPv4 and IPv6 via dual stack router (DSR). The dual stack router (DSR) gives the path for all the hosts to communicate with server without changing their IP addresses. Tunneling: Tunneling is used as a medium to communicate the transit network with the different ip versions. In this above diagram, the different IP versions such as IPv4 and IPv6 are present. The IPv4 networks can communicate with the transit or intermediate network on IPv6 with the help of Tunnel. It’s also possible that the IPv6 network can also communicate with IPv4 networks with the help of Tunnel. NAT Protocol Translation: By the help of NAT Protocol Translation technique, the IPv4 and IPv6 networks can also communicate with each other which do not understand the address of different IP version. Generally, an IP version doesn’t understand the address of different IP version, for the solution of this problem we use NAT-PT device which remove the header of first (sender) IP version address and add the second (receiver) IP version address so that the Receiver IP version address understand that the request is send by the same IP version, and its vice-versa is also possible.
- 14. Data Communication and Computer Network Sweta Barnwal Page 14 In above diagram, an IPv4 address communicates with the IPv6 address via NAT-PT device to communicate easily. In this situation IPv6 address understands that the request is send by the same IP version (IPv6) and it respond. Network Performance Network performance is the analysis and review of collective network statistics, to define the quality of services offered by the underlying computer network. It is a qualitative and quantitative process that measures and defines the performance level of a given network. It guides a network administrator in the review, measure and improvement of network services. Network performance is primarily measured from an end-user perspective (i.e. quality of network services delivered to the user). Broadly, network performance is measured by reviewing the statistics and metrics from the following network components: • Network bandwidth or capacity - Available data transfer • Network throughput - Amount of data successfully transferred over the network in a given time • Network delay, latency and jittering - Any network issue causing packet transfer to be slower than usual • Data loss and network errors - Packets dropped or lost in transmission and delivery TCP & UDP TCP stands for Transmission Control Protocol. It is a transport layer protocol that facilitates the transmission of packets from source to destination. It is a connection-oriented protocol that means it establishes the connection prior to the communication that occurs between the computing devices in a network. This protocol is used with an IP protocol, so together, they are referred to as a TCP/IP. The main functionality of the TCP is to take the data from the application layer. Then it divides the data into a several packets, provides numbering to these packets, and finally transmits these packets to the destination. The TCP, on the other side, will reassemble the packets and transmits them to the application layer. As we know that TCP is a connection-oriented protocol, so the connection will remain established until the communication is not completed between the sender and the receiver. Features of TCP protocol: o Transport Layer Protocol TCP is a transport layer protocol as it is used in transmitting the data from the sender to the receiver. 24.7M 415 Hello Java Program for Beginners Next Stay
- 15. Data Communication and Computer Network Sweta Barnwal Page 15 o Reliable TCP is a reliable protocol as it follows the flow and error control mechanism. It also supports the acknowledgment mechanism, which checks the state and sound arrival of the data. In the acknowledgment mechanism, the receiver sends either positive or negative acknowledgment to the sender so that the sender can get to know whether the data packet has been received or needs to resend. o Order of the data is maintained This protocol ensures that the data reaches the intended receiver in the same order in which it is sent. It orders and numbers each segment so that the TCP layer on the destination side can reassemble them based on their ordering. o Connection-oriented It is a connection-oriented service that means the data exchange occurs only after the connection establishment. When the data transfer is completed, then the connection will get terminated. o Full duplex It is a full-duplex means that the data can transfer in both directions at the same time. o Stream-oriented TCP is a stream-oriented protocol as it allows the sender to send the data in the form of a stream of bytes and also allows the receiver to accept the data in the form of a stream of bytes. TCP creates an environment in which both the sender and receiver are connected by an imaginary tube known as a virtual circuit. This virtual circuit carries the stream of bytes across the internet.
- 16. Data Communication and Computer Network Sweta Barnwal Page 16 TCP Header Format o Source port: It defines the port of the application, which is sending the data. So, this field contains the source port address, which is 16 bits. o Destination port: It defines the port of the application on the receiving side. So, this field contains the destination port address, which is 16 bits. o Sequence number: This field contains the sequence number of data bytes in a particular session. o Acknowledgment number: When the ACK flag is set, then this contains the next sequence number of the data byte and works as an acknowledgment for the previous data received. For example, if the receiver receives the segment number 'x', then it responds 'x+1' as an acknowledgment number. o HLEN: It specifies the length of the header indicated by the 4-byte words in the header. The size of the header lies between 20 and 60 bytes. Therefore, the value of this field would lie between 5 and 15. o Reserved: It is a 4-bit field reserved for future use, and by default, all are set to zero. o Flags There are six control bits or flags: 1. URG: It represents an urgent pointer. If it is set, then the data is processed urgently. 2. ACK: If the ACK is set to 0, then it means that the data packet does not contain an acknowledgment. 3. PSH: If this field is set, then it requests the receiving device to push the data to the receiving application without buffering it. 4. RST: If it is set, then it requests to restart a connection.
- 17. Data Communication and Computer Network Sweta Barnwal Page 17 5. SYN: It is used to establish a connection between the hosts. 6. FIN: It is used to release a connection, and no further data exchange will happen. o Window size: It is a 16-bit field. It contains the size of data that the receiver can accept. This field is used for the flow control between the sender and receiver and also determines the amount of buffer allocated by the receiver for a segment. The value of this field is determined by the receiver. o Checksum: It is a 16-bit field. This field is optional in UDP, but in the case of TCP/IP, this field is mandatory. o Urgent pointer: It is a pointer that points to the urgent data byte if the URG flag is set to 1. It defines a value that will be added to the sequence number to get the sequence number of the last urgent byte. o Options: It provides additional options. The optional field is represented in 32-bits. If this field contains the data less than 32-bit, then padding is required to obtain the remaining bits. Need of Transport Control Protocol In the layered architecture of a network model, the whole task is divided into smaller tasks. Each task is assigned to a particular layer that processes the task. In the TCP/IP model, five layers are application layer, transport layer, network layer, data link layer, and physical layer. The transport layer has a critical role in providing end-to-end communication to the directly application processes. It creates 65,000 ports so that the multiple applications can be accessed at the same time. It takes the data from the upper layer, and it divides the data into smaller packets and then transmits them to the network layer.
- 18. Data Communication and Computer Network Sweta Barnwal Page 18 Working of TCP In TCP, the connection is established by using three-way handshaking. The client sends the segment with its sequence number. The server, in return, sends its segment with its own sequence number as well as the acknowledgement sequence, which is one more than the client sequence number. When the client receives the acknowledgment of its segment, then it sends the acknowledgment to the server. In this way, the connection is established between the client and the server. Advantages of TCP o It provides a connection-oriented reliable service, which means that it guarantees the delivery of data packets. If the data packet is lost across the network, then the TCP will resend the lost packets. o It provides a flow control mechanism using a sliding window protocol. o It provides error detection by using checksum and error control by using Go Back or ARP protocol. o It eliminates the congestion by using a network congestion avoidance algorithm that includes various schemes such as additive increase/multiplicative decrease (AIMD), slow start, and congestion window. Disadvantage of TCP It increases a large amount of overhead as each segment gets its own TCP header, so fragmentation by the router increases the overhead. UDP User Datagram Protocol (UDP) is a Transport Layer protocol. UDP is a part of the Internet Protocol suite, referred to as UDP/IP suite. Unlike TCP, it is an unreliable and connectionless protocol. So, there is no need to establish a connection prior to data transfer.
- 19. Data Communication and Computer Network Sweta Barnwal Page 19 Though Transmission Control Protocol (TCP) is the dominant transport layer protocol used with most of the Internet services; provides assured delivery, reliability, and much more but all these services cost us additional overhead and latency. Here, UDP comes into the picture. For real-time services like computer gaming, voice or video communication, live conferences; we need UDP. Since high performance is needed, UDP permits packets to be dropped instead of processing delayed packets. There is no error checking in UDP, so it also saves bandwidth. User Datagram Protocol (UDP) is more efficient in terms of both latency and bandwidth. UDP Header – UDP header is an 8-bytes fixed and simple header, while for TCP it may vary from 20 bytes to 60 bytes. The first 8 Bytes contains all necessary header information and the remaining part consist of data. UDP port number fields are each 16 bits long, therefore the range for port numbers is defined from 0 to 65535; port number 0 is reserved. Port numbers help to distinguish different user requests or processes. 1. Source Port: Source Port is a 2 Byte long field used to identify the port number of the source. 2. Destination Port: It is a 2 Byte long field, used to identify the port of the destined packet. 3. Length: Length is the length of UDP including the header and the data. It is a 16-bits field. 4. Checksum: Checksum is 2 Bytes long field. It is the 16-bit one’s complement of the one’s complement sum of the UDP header, the pseudo-header of information from the IP header, and the data, padded with zero octets at the end (if necessary) to make a multiple of two octets. Transmission control protocol (TCP) User datagram protocol (UDP) TCP is a connection-oriented protocol. Connection-orientation means that the communicating devices should establish a connection before transmitting data and should close the connection after transmitting the data. UDP is the Datagram oriented protocol. This is because there is no overhead for opening a connection, maintaining a connection, and terminating a connection. UDP is efficient for broadcast and multicast type of network transmission. TCP is reliable as it guarantees the delivery of The delivery of data to the destination cannot be
- 20. Data Communication and Computer Network Sweta Barnwal Page 20 data to the destination router. guaranteed in UDP. TCP provides extensive error checking mechanisms. It is because it provides flow control and acknowledgement of data. UDP has only the basic error checking mechanism using checksums. Acknowledgement segment is present. No acknowledgement segment. Sequencing of data is a feature of Transmission Control Protocol (TCP). this means that packets arrive in-order at the receiver. There is no sequencing of data in UDP. If the order is required, it has to be managed by the application layer. TCP is comparatively slower than UDP. UDP is faster, simpler, and more efficient than TCP. Retransmission of lost packets is possible in TCP, but not in UDP. There is no retransmission of lost packets in the User Datagram Protocol (UDP). TCP has a (20-60) bytes variable length header. UDP has an 8 bytes fixed-length header. TCP is heavy-weight. UDP is lightweight. Uses handshakes such as SYN, ACK, SYN-ACK It’s a connectionless protocol i.e. No handshake TCP doesn’t support Broadcasting. UDP supports Broadcasting. TCP is used by HTTP, HTTPs, FTP, SMTP and Telnet. UDP is used by DNS, DHCP, TFTP, SNMP, RIP, and VoIP. Stop and Wait protocol Stop and Wait protocol is a protocol for flow control mechanism. In this protocol, sender sends one frame at a time and waits for acknowledgment from the receiver. Once acknowledged, sender sends another frame to the receiver. If acknowledgment is not received then frame/packet is retransmitted. Go Back N protocol Go Back N is also a protocol for flow control mechanism. In this protocol, sender sends n frames at a time and wait for cumulative acknowledgment. If acknowledgment is not received then entire frames are retransmitted again. Selective Repeat protocol Selective Repeat is also a protocol for flow control mechanism. In this protocol, sender sends n frames at a time and wait for acknowledgment of packets received in particular order. If acknowledgment is not received then lost packets are transmitted again which is based on receiver acknowledgment. Receiver maintains a buffer of lost packets. Following are some of the important differences between Stop and Wait protocol and Sliding Window protocol. Sr. No. Key Stop and Wait protocol Go Back N protocol Selective Repeat protocol 1 Sender window size In Stop and Wait protocol, Sender window size is 1. In GoBackN protocol, Sender window size is N. In Selective Repeat protocol, Sender window size is N.
- 21. Data Communication and Computer Network Sweta Barnwal Page 21 Sr. No. Key Stop and Wait protocol Go Back N protocol Selective Repeat protocol 2 Receiver Window size In Stop and Wait protocol, Receiver window size is 1. In GoBackN protocol, Receiver window size is 1. In Selective Repeat protocol, Receiver window size is N. 3 Minimum Sequence Number In Stop and Wait protocol, Minimum Sequence Number is 2. In GoBackN protocol, Minimum Sequence Number is N+1 where N is number of packets sent. In Selective Repeat protocol, Minimum Sequence Number is 2N where N is number of packets sent. 4 Efficiency In Stop and Wait protocol, Efficiency formular is 1/(1+2*a) where a is ratio of propagation delay vs transmission delay. In GoBackN protocol, Efficiency formular is N/(1+2*a) where a is ratio of propagation delay vs transmission delay and N is number of packets sent. In Selective Repeat protocol, Efficiency formular is N/(1+2*a) where a is ratio of propagation delay vs transmission delay and N is number of packets sent. 5 Acknowledgement Type In Stop and Wait protocol, Acknowledgement type is individual. In GoBackN protocol, Acknowledgement type is cumulative. In Selective Repeat protocol, Acknowledgement type is individual. 6 Supported Order In Stop and Wait protocol, no specific order is needed at receiver end. In this protocol, in-order delivery only is accepted at receiver end. In Selective Repeat protocol, out-of-order deliveries also can be accepted at receiver end. 7 Retransmissions In Stop and Wait protocol, in case of packet drop, number of retransmissions is 1. In this protocol, in case of packet drop, numbers of retransmission are N. In Selective Repeat protocol, in case of packet drop, number of retransmissions is 1. 8 Sender window size 1 N N 9 Receiver Window size 1 1 N 10 Minimum Sequence number 2 N+1 2N
- 22. Data Communication and Computer Network Sweta Barnwal Page 22 Sr. No. Key Stop and Wait protocol Go Back N protocol Selective Repeat protocol 11 Efficiency 1/(1+2*a) N/(1+2*a) N/(1+2*a) 12 Type of Acknowledgement Individual Cumulative Individual Supported order at the Receiving end – In-order delivery only Out-of-order delivery as well Number of retransmissions in case of packet drop 1 N 1 Bidirectional transport protocol (BTP), has demonstrated reliable performance regarding time spent for packet transmission. This protocol provides a novel congestion control technique which enhances application and transport layer. TCP is bidirectional because it can send data in both directions, and it is full-duplex because it can do that simultaneously.
