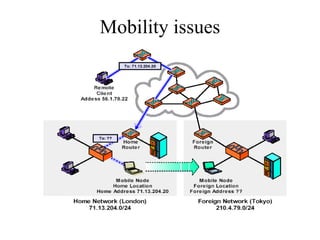
Mobility And Mobile I Pv4
•Transferir como PPT, PDF•
1 gostou•706 visualizações
Unit 3 Of ACN
Denunciar
Compartilhar
Denunciar
Compartilhar
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Performance of Various Mobile IP Protocols and Security Considerations

Performance of Various Mobile IP Protocols and Security Considerations
Tracing An IP Address or Domain Name by Raghu Khimani

Tracing An IP Address or Domain Name by Raghu Khimani
Destaque
Destaque (20)
Computer Security Lecture 3: Classical Encryption Techniques 2

Computer Security Lecture 3: Classical Encryption Techniques 2
Computer Security Lecture 2: Classical Encryption Techniques 1

Computer Security Lecture 2: Classical Encryption Techniques 1
Classical Encryption Techniques in Network Security

Classical Encryption Techniques in Network Security
IS Unit 1_Conventional Encryption_Classical Encryption Techniques

IS Unit 1_Conventional Encryption_Classical Encryption Techniques
Revista qué pasa ranking UNIVERSIDADES 2010. (1de2)

Revista qué pasa ranking UNIVERSIDADES 2010. (1de2)
Semelhante a Mobility And Mobile I Pv4
Semelhante a Mobility And Mobile I Pv4 (20)
Mais de Ram Dutt Shukla
Mais de Ram Dutt Shukla (20)
Último
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam

DEV meet-up UiPath Document Understanding May 7 2024 Amsterdam
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024

Modular Monolith - a Practical Alternative to Microservices @ Devoxx UK 2024
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)

AI+A11Y 11MAY2024 HYDERBAD GAAD 2024 - HelloA11Y (11 May 2024)
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Six Myths about Ontologies: The Basics of Formal Ontology

Six Myths about Ontologies: The Basics of Formal Ontology
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Mobility And Mobile I Pv4
- 12. Mobile IP Mobility Agent Advertisement Extension Format
- 18. Mobile tunneling Triangle path
