XPath Injection
•
0 gostou•960 visualizações
XPath injection occurs when user-supplied input is used to construct an XPath query without sanitization, allowing an attacker to access unauthorized XML data or elevate privileges. Like SQL injection, malicious XPath can expose sensitive information or take control of authentication by modifying the query. The WebCruiser tool can scan for and prove XPath injection vulnerabilities by modifying queries and observing the results.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Mvc by asp.net development company in india - part 2

Mvc by asp.net development company in india - part 2
Web Security - OWASP - SQL injection & Cross Site Scripting XSS

Web Security - OWASP - SQL injection & Cross Site Scripting XSS
Semelhante a XPath Injection
Semelhante a XPath Injection (20)
Pascarello_Investigating JavaScript and Ajax Security

Pascarello_Investigating JavaScript and Ajax Security
Mais de Magno Logan
Mais de Magno Logan (20)
DevSecOps - Integrating Security in the Development Process (with memes) - Ma...

DevSecOps - Integrating Security in the Development Process (with memes) - Ma...
Katana Security - Consultoria em Segurança da Informação

Katana Security - Consultoria em Segurança da Informação
Tratando as vulnerabilidades do Top 10 do OWASP by Wagner Elias

Tratando as vulnerabilidades do Top 10 do OWASP by Wagner Elias
Mutillidae and the OWASP Top 10 by Adrian Crenshaw aka Irongeek

Mutillidae and the OWASP Top 10 by Adrian Crenshaw aka Irongeek
Co0L 2011 - Segurança em Sites de Compras Coletivas: Vulnerabilidades, Ataqu...

Co0L 2011 - Segurança em Sites de Compras Coletivas: Vulnerabilidades, Ataqu...
AppSec EU 2009 - HTTP Parameter Pollution by Luca Carettoni and Stefano di P...

AppSec EU 2009 - HTTP Parameter Pollution by Luca Carettoni and Stefano di P...
AppSec EU 2011 - An Introduction to ZAP by Simon Bennetts

AppSec EU 2011 - An Introduction to ZAP by Simon Bennetts
OWASP Floripa - Web Spiders: Automação para Web Hacking by Antonio Costa aka ...

OWASP Floripa - Web Spiders: Automação para Web Hacking by Antonio Costa aka ...
AppSec Brazil 2010 - Utilizando a ESAPI para prover Segurança em Aplicações W...

AppSec Brazil 2010 - Utilizando a ESAPI para prover Segurança em Aplicações W...
AppSec DC 2009 - Learning by breaking by Chuck Willis

AppSec DC 2009 - Learning by breaking by Chuck Willis
Just4Meeting 2012 - How to protect your web applications

Just4Meeting 2012 - How to protect your web applications
AppSec Latam 2011 - Treinamento OWASP Top 10 + JavaEE

AppSec Latam 2011 - Treinamento OWASP Top 10 + JavaEE
Último
Último (20)
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
Elevate Developer Efficiency & build GenAI Application with Amazon Q

Elevate Developer Efficiency & build GenAI Application with Amazon Q
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Finding Java's Hidden Performance Traps @ DevoxxUK 2024

Finding Java's Hidden Performance Traps @ DevoxxUK 2024
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
CNIC Information System with Pakdata Cf In Pakistan

CNIC Information System with Pakdata Cf In Pakistan
XPath Injection
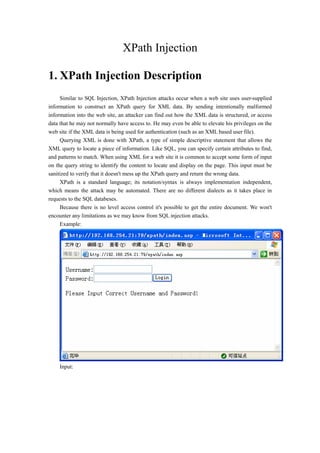
- 1. XPath Injection 1. XPath Injection Description Similar to SQL Injection, XPath Injection attacks occur when a web site uses user-supplied information to construct an XPath query for XML data. By sending intentionally malformed information into the web site, an attacker can find out how the XML data is structured, or access data that he may not normally have access to. He may even be able to elevate his privileges on the web site if the XML data is being used for authentication (such as an XML based user file). Querying XML is done with XPath, a type of simple descriptive statement that allows the XML query to locate a piece of information. Like SQL, you can specify certain attributes to find, and patterns to match. When using XML for a web site it is common to accept some form of input on the query string to identify the content to locate and display on the page. This input must be sanitized to verify that it doesn't mess up the XPath query and return the wrong data. XPath is a standard language; its notation/syntax is always implementation independent, which means the attack may be automated. There are no different dialects as it takes place in requests to the SQL databeses. Because there is no level access control it's possible to get the entire document. We won't encounter any limitations as we may know from SQL injection attacks. Example: Input:
- 2. Result: The result includes much sensitive information, now you can get a conclusion that the application use XML file to store user authentication data. In order to analyze the injection process, we modify the sever script to output the query sentence to user’s browser. Input the following username or password: 999'] | * | user[@role='admin
- 3. Result: The text with red frame is the XPath query sentence. 999'] | * | user[@role='admin has been injected the sentence successfully. Now, let’s see the source code of index.asp: <script language="javascript" runat="server"> Response.write("<html><body>"); uid=Request.form("uid"); pwd=Request.form("pwd"); Response.write("<form method="POST">Username:<input name="uid" size="20"/><br>Password:<input name="pwd" size="20"/><input type="submit" value="Login"/></form>"); var xmlDom=new ActiveXObject("Microsoft.XMLDOM"); xmlDom.async="false"; xmlDom.load("/Inetpub/wwwroot/xpath/user.xml"); var auth="//users/user[loginID/text()='"+uid+"' and password/text()='"+pwd+"']";
- 4. Response.write(auth); var UserObj=xmlDom.selectNodes(auth); if(UserObj.length>0) Response.write("<br><br>Login OK!"); else Response.write("Please Input Correct Username and Password!"); Response.write(UserObj.Xml); for(var i=0;i<UserObj.length;i++) { Response.write("<xmp>"); Response.write(UserObj(i).xml); Response.write("</xmp>"); } Response.write("</body></html>"); </script> user authentication file user.xml : <?xml version="1.0" encoding="UTF-8"?> <users> <user> <firstname>Ben</firstname> <lastname>Elmore</lastname> <loginID>abc</loginID> <password>test123</password> </user> <user> <firstname>Shlomy</firstname> <lastname>Gantz</lastname> <loginID>xyz</loginID> <password>123test</password> </user> </users> You can get the XPath query sentence as follow: auth="//users/user[loginID/text()='"+uid+"' and password/text()='"+pwd+"']" It means that, select user nodes which uid is equal to your input uid and password is equal to your input pwd; The actual XPath sentence is set to: //users/user[loginID/text()='999' and password/text()='999'] | * | user[@role='admin'] , The logic result is select all nodes, XPath injection occurred. 2. XPath Injection Tool WebCruiser - Web Vulnerability Scanner
- 5. WebCruiser - Web Vulnerability Scanner, a compact but powerful web security scanning tool! It has a Crawler and Vulnerability Scanner(SQL Injection, Cross Site Scripting, XPath Injection etc. ). It can support scanning website as well as POC( Prooving of concept) for web vulnerabilities: SQL Injection, Cross Site Scripting, XPath Injection etc. So, WebCruiser is also a SQL Injector, a XPath Injector , and a Cross Site Scripting tool! Function: * Crawler(Site Directories And Files); * Vulnerability Scanner(SQL Injection, Cross Site Scripting, XPath Injection etc.); * POC(Proof of Concept): SQL Injection, Cross Site Scripting, XPath Injection etc.; * GET/Post/Cookie Injection; * SQL Server: PlainText/FieldEcho(Union)/Blind Injection; * MySQL/Oracle/DB2/Access: FieldEcho(Union)/Blind Injection; * Administration Entrance Search; * Time Delay For Search Injection; * Auto Get Cookie From Web Browser For Authentication; * Report Output. http://sec4app.com
