Trident Warrior '10: Dataline Secure Cloud Computing
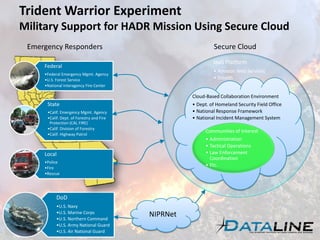
- 1. Trident Warrior Experiment Military Support for HADR Mission Using Secure Cloud Emergency Responders Secure Cloud IaaS Platform Federal • Amazon Web Services •Federal Emergency Mgmt. Agency •U.S. Forest Service • Stealth •National Interagency Fire Center Cloud-Based Collaboration Environment State • Dept. of Homeland Security Field Office •Calif. Emergency Mgmt. Agency • National Response Framework •Calif. Dept. of Forestry and Fire • National Incident Management System Protection (CAL FIRE) •Calif. Division of Forestry Communities of Interest •Calif. Highway Patrol • Administration • Tactical Operations Local • Law Enforcement Coordination •Police •Fire • Etc. •Rescue DoD •U.S. Navy •U.S. Marine Corps •U.S. Northern Command NIPRNet •U.S. Army National Guard •U.S. Air National Guard
- 2. Government Cloud Computing United States Federal Chief Information Officers Council Data.gov & IT Dashboard Defense Information Systems Agency (DISA) Rapid Access Computing Environment (RACE) US Department of Energy (DOE) Magellan General Services Administration (GSA) Apps.gov Department of the Interior National Business Center (NBC) Cloud Computing NASA Nebula National Institute of Standards and Technology (NIST) United Kingdom G-Cloud European Union Resources and Services Virtualization without Barriers Project (RESERVOIR) Canada Canada Cloud Computing Cloud Computing and the Canadian Environment Japan The Digital Japan Creation Project (ICT Hatoyama Plan) The Kasumigaseki Cloud
- 3. Federal Cloud Computing Initiative (FCCI)
- 6. Secure Collaboration https://xmpp.je.jfcom.mil/ Cloud-based Cross Domain Collaborative Information Environment (CDCIE) Chat Use any of the same-domain functions to communicate with local users. Use the cross-domain functions (including Group Chat, Language Translation, Whiteboard*, Monitor for Text, and Keyword Highlighting) to communicate with remote users. Use these same-domain and cross-domain functions within the same session of TransVerse. Secured with cryptographic bit splitting technology Developed by:
- 7. SecureParser® Cryptographically splits data Document Email -E -mail Database Database Video Map Imagery Imagery Creates physically separate fault tolerant Shares High-efficiency cryptographic module: CDIP & COI Framework • Provably-secure Computational Secret Sharing • Cryptographic Data Splitting AES Encryption • Data Integrity Protection • Modules can be change out, e.g. AES could be Random Bit Split changed with a TYPE I encryption as requirement “M of N Fault Tolerance ” called for Share Authentication Physically Separate Shares • Written to Storage – Data at Rest • Written to Networks – Data in Motion • Created at any IO Point in the system 1 2 3 4 User Definable • Number of Shares • Fault Tolerance • Key Management
- 9. Trident Warrior Lab 1
- 10. Tactical Cloud Computing The use of cloud computing technology and techniques to support localized, short-lived information access and processing. Use cases could include: • “Cloudbursting” to support cyclic data processing requirements • Establishing a cloud-based collaboration environment in order to coordinate firefighting resources during a wildfire • Virtually binding shipboard IT infrastructures in order to create a battlegroup infrastructure-as-a-service platform • Virtually binding land vehicle based servers and storage resources into a battlefield data center • Dynamic provisioning of virtual cloud-based servers in order to automate exploitation and dissemination of unmanned air vehicle (UAV) streaming video feeds rev date 10/31/2009
