Hashing
•Transferir como PPT, PDF•
0 gostou•619 visualizações
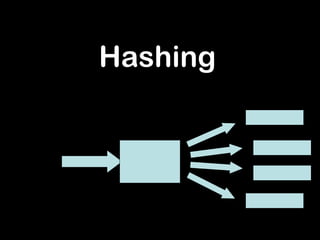
Hashing involves using an algorithm to generate a numeric key from input data. It maps keys to integers in order to store and retrieve data more efficiently. A simple hashing algorithm uses the modulus operator (%) to distribute keys uniformly. Hashing is commonly used for file management, comparing complex values, and cryptography. Collisions occur when different keys hash to the same value, requiring strategies like open hashing, closed hashing, or deleting data. Closed hashing supplements the hash table with linked lists to store colliding entries outside the standard table.
Denunciar
Compartilhar
Denunciar
Compartilhar
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Hashing and Hashtable, application of hashing, advantages of hashing, disadva...

Hashing and Hashtable, application of hashing, advantages of hashing, disadva...
Searching and Sorting Techniques in Data Structure

Searching and Sorting Techniques in Data Structure
PPT On Sorting And Searching Concepts In Data Structure | In Programming Lang...

PPT On Sorting And Searching Concepts In Data Structure | In Programming Lang...
Destaque
زیرساخت کلید عمومی (PKI)، مفاهیم، کاربردها و کاربری امضای دیجیتال

زیرساخت کلید عمومی (PKI)، مفاهیم، کاربردها و کاربری امضای دیجیتالمرکز دولتی صدور گواهی الکترونیکی ریشه
اصالتسنجی اسناد الکترونیکی (راهکار جلوگیری از جعل اسناد الکترونیکی)

اصالتسنجی اسناد الکترونیکی (راهکار جلوگیری از جعل اسناد الکترونیکی)مرکز دولتی صدور گواهی الکترونیکی ریشه
Destaque (20)
بروشور معرفی مرکز دولتی صدور گواهی الکترونیکی ریشه

بروشور معرفی مرکز دولتی صدور گواهی الکترونیکی ریشه
Introduction by Rogier Ormeling about the collection of Henk and Leonie Pij...

Introduction by Rogier Ormeling about the collection of Henk and Leonie Pij...
زیرساخت کلید عمومی (PKI)، مفاهیم، کاربردها و کاربری امضای دیجیتال

زیرساخت کلید عمومی (PKI)، مفاهیم، کاربردها و کاربری امضای دیجیتال
اصالتسنجی اسناد الکترونیکی (راهکار جلوگیری از جعل اسناد الکترونیکی)

اصالتسنجی اسناد الکترونیکی (راهکار جلوگیری از جعل اسناد الکترونیکی)
Semelhante a Hashing
Semelhante a Hashing (20)
Hashing techniques, Hashing function,Collision detection techniques

Hashing techniques, Hashing function,Collision detection techniques
unit-1-dsa-hashing-2022_compressed-1-converted.pptx

unit-1-dsa-hashing-2022_compressed-1-converted.pptx
Mais de grahamwell
Mais de grahamwell (20)
Hashing
- 1. Hashing
- 2. What is hashing • Simply, generating a numeric key using an algorithm (hash function) • Definition: A function that maps keys to integers, usually to get an even distribution on a smaller set of values. • The very simplest hash function is to use the modulus operator % • Input range % key range
- 3. Input and key range • Example. We want to store 7 digit telephone numbers so that they can be quickly retrieved. – Number of expected entries = 100 – Range of telephone numbers = 0 – 9999999 Simple hashing algorithm hash = inputNumber % 100 What’s the effect?
- 4. Applications of hashing • File management – working out where to store records • Comparing complex values • Cryptography – creating digital signatures – eg: md5
- 5. Collisions • Where the hash value returned for two keys is the same. • What to do? – Open hashing – Closed hashing – Deleting • The 2/3rds rule
- 6. Closed Hashing 1 23 32 44 End 2 3 4 33 Hash table is supplemented by 5 a linked list, which is used to store colliding entries. 6 7 Therefore, some values are found outside of the standard hash table (in the linked list)
- 7. ‘Open’ Hashing Some strategy is used to fit colliding entries in a predictable way inside the 1 23 existing table 2 32 3 44 For this to work, the size of 4 33 the table needs to be 5 significantly bigger than the total number of records 6 7 At least 3:2
- 8. DJB Hash function • “An algorithm produced by Professor Daniel J. Bernstein and shown first to the world on the usenet newsgroup comp.lang.c. It is one of the most efficient hash functions ever published. “ def DJBHash(key): hash = 5381 for i in range(len(key)): hash = ((hash << 5) + hash) + ord(key[i]) return hash