Siem tools
•Transferir como DOCX, PDF•
2 gostaram•799 visualizações
SIEM tools performance comparison. What is SIEM? SIEM security tools like IBM qradar, archsight, splunk compared according to performance parameters.
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Enhancing SIEM Correlation Rules Through Baselining

Enhancing SIEM Correlation Rules Through Baselining
OSSIM User Training: Detect and Respond to Threats More Quickly with OSSIM v4.5

OSSIM User Training: Detect and Respond to Threats More Quickly with OSSIM v4.5
Five Best and Five Worst Practices for SIEM by Dr. Anton Chuvakin

Five Best and Five Worst Practices for SIEM by Dr. Anton Chuvakin
"You Got That SIEM. Now What Do You Do?" by Dr. Anton Chuvakin

"You Got That SIEM. Now What Do You Do?" by Dr. Anton Chuvakin
How to create correlation rule for threat detection in RuSIEM

How to create correlation rule for threat detection in RuSIEM
SYMANTEC ENDPOINT PROTECTION Advanced Monitoring and Reporting

SYMANTEC ENDPOINT PROTECTION Advanced Monitoring and Reporting
Sol 03 - Office 365 Advanced Security Hardening with cFocus Software

Sol 03 - Office 365 Advanced Security Hardening with cFocus Software
Presentatie McAfee: Optimale Endpoint Protection 26062015

Presentatie McAfee: Optimale Endpoint Protection 26062015
Using Logs for Breach Investigations and Incident Response by Dr Anton Chuvakin

Using Logs for Breach Investigations and Incident Response by Dr Anton Chuvakin
Semelhante a Siem tools
Semelhante a Siem tools (20)
RedisConf18 - Auto-Scaling Redis Caches - Observability, Efficiency & Perform...

RedisConf18 - Auto-Scaling Redis Caches - Observability, Efficiency & Perform...
Amazon EC2 deepdive and a sprinkel of AWS Compute | AWS Floor28

Amazon EC2 deepdive and a sprinkel of AWS Compute | AWS Floor28
Hive + Amazon EMR + S3 = Elastic big data SQL analytics processing in the cloud

Hive + Amazon EMR + S3 = Elastic big data SQL analytics processing in the cloud
Architecting and Tuning IIB/eXtreme Scale for Maximum Performance and Reliabi...

Architecting and Tuning IIB/eXtreme Scale for Maximum Performance and Reliabi...
times ten in-memory database for extreme performance

times ten in-memory database for extreme performance
Anna Vergeles, Nataliia Manakova "Unsupervised Real-Time Stream-Based Novelty...

Anna Vergeles, Nataliia Manakova "Unsupervised Real-Time Stream-Based Novelty...
Extend HPC Workloads to Amazon EC2 Instances with Intel and Rescale (CMP373-S...

Extend HPC Workloads to Amazon EC2 Instances with Intel and Rescale (CMP373-S...
Webinar slides: An Introduction to Performance Monitoring for PostgreSQL

Webinar slides: An Introduction to Performance Monitoring for PostgreSQL
New Business Applications Powered by In-Memory Technology @MIT Forum for Supp...

New Business Applications Powered by In-Memory Technology @MIT Forum for Supp...
Matlab Based High Level Synthesis Engine for Area And Power Efficient Arithme...

Matlab Based High Level Synthesis Engine for Area And Power Efficient Arithme...
Mais de Ertugrul Akbas
Mais de Ertugrul Akbas (20)
BDDK, SPK, TCMB, Cumhurbaşkanlığı Dijital Dönüşüm Ofisi ve ISO27001 Denetiml...

BDDK, SPK, TCMB, Cumhurbaşkanlığı Dijital Dönüşüm Ofisi ve ISO27001 Denetiml...
Olay Müdahale İçin Canlı Kayıtların Saklanmasının Önemi

Olay Müdahale İçin Canlı Kayıtların Saklanmasının Önemi
SureLog SIEM Has The Best On-Line Log Retention Time (Hot Storage).

SureLog SIEM Has The Best On-Line Log Retention Time (Hot Storage).
SIEM ve KVKK Teknik Tedbirlerinin ANET SureLog SIEM ile uygulanması 

SIEM ve KVKK Teknik Tedbirlerinin ANET SureLog SIEM ile uygulanması
Último
Último (20)
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
Apidays New York 2024 - The value of a flexible API Management solution for O...

Apidays New York 2024 - The value of a flexible API Management solution for O...
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Vector Search -An Introduction in Oracle Database 23ai.pptx

Vector Search -An Introduction in Oracle Database 23ai.pptx
Siem tools
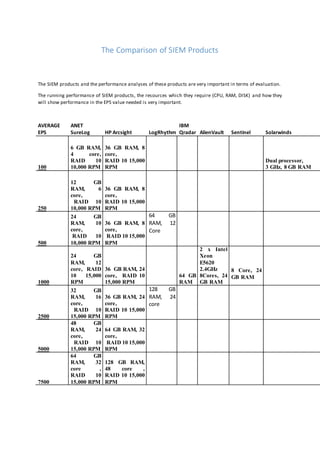
- 1. The Comparison of SIEM Products The SIEM products and the performance analyses of these products are very important in terms of evaluation. The running performance of SIEM products, the resources which they require (CPU, RAM, DISK) and how they will show performance in the EPS value needed is very important. AVERAGE EPS ANET SureLog HP Arcsight LogRhythm IBM Qradar AlienVault Sentinel Solarwinds 100 6 GB RAM, 4 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM Dual processor, 3 GHz, 8 GB RAM 250 12 GB RAM, 6 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM 500 24 GB RAM, 10 core, RAID 10 10,000 RPM 36 GB RAM, 8 core, RAID 10 15,000 RPM 64 GB RAM, 12 Core 1000 24 GB RAM, 12 core, RAID 10 15,000 RPM 36 GB RAM, 24 core, RAID 10 15,000 RPM 64 GB RAM 2 x Intel Xeon E5620 2.4GHz 8Cores, 24 GB RAM 8 Core, 24 GB RAM 2500 32 GB RAM, 16 core, RAID 10 15,000 RPM 36 GB RAM, 24 core, RAID 10 15,000 RPM 128 GB RAM, 24 core 5000 48 GB RAM, 24 core, RAID 10 15,000 RPM 64 GB RAM, 32 core, RAID 10 15,000 RPM 7500 64 GB RAM, 32 core , RAID 10 15,000 RPM 128 GB RAM, 48 core , RAID 10 15,000 RPM
- 2. The relationship between the average EPS values and the maximum EPS values of the system in SIEM projects worked on and planning of system resources accordingly is a critical stage. How much EPS value the system reaches which will produce1000 EPS logs under normal conditions,in casean attack happens or a virus infects. If such cases occurs in the system, how SIEM system reacts. It is very critical planning all those cases. [1,6] HP Arcsight, ANET SureLog, IBM Qradar, LogRhthym, AlienVault, Novell Sentinel and Solarwinds LEM are compared with each other in this study. ANET SureLog has one other advantage over others that Log Management is also integrated in ANET SureLog while others are just SIEM. While the average EPS values are specified in some of the manufacturer tables, the max EPS values are specified in the others. The average EPS values are taken for each SIEM product in the table shown above. The some of the parameters which will affect the values in the table above [10,11] The number of total rules [12] The difficulty degree of the rules o Warn if user A can’t log into X server and caused failed authentication, and in two hours if that user A can’t log into the same X server. o Warn for a traffic whose destination port is 67, protocol is UDP, and destination IP is not in registered DHCP server list, occurs more than two times in one minute. o Warn if the servers are accessed out of hours. o Warn if more than 100 connections are established from different external IPs to the same destination IP in one minute. o Warn if 100 connections are established from the same external IP through different ports to the same destination IP in one minute. o Warn if the same user tries more than three failed logon attempts to the same machine in an hour. o Warn if the source or destination IP access attempt occurs to an IP address in the IP Reputation list. The correlation speed The Taxonomy features and the number of categories The type of correlation o A true correlation engine and in-memory correlation o ELK-based, the methods which are actually search based. In some products like HP Arcsight and Qradar; given values are just for correlation engine. Log collecting, parsing and reporting servers also needs additional machines. This study is conducted over average EPS values. For reaching max EPS values, the resources should be expanded by 1,5-2 times. The accurate planning of the EPS values and the behavior of the system under high load depend fully upon these system resources. Also the other critical matter is that the system resource requirements of Log Management solutions and SEIM solutions are completely different from each other. References: 1. http://www.slideshare.net/anetertugrul/log-ynetimi-sisteminizin-log-karp-karmadn-test-etmek-ister- misiniz 2. http://www8.hp.com/tr/tr/software-solutions/arcsight-esm-enterprise-security-management/tech- specs.html 3. http://www.solarwinds.com/log-event-manager.aspx#p_systemrequirements
- 3. 4. https://www.alienvault.com/docs/data-sheets/AV-USM.pdf 5. http://www- 01.ibm.com/support/knowledgecenter/SS42VS_7.2.4/com.ibm.qradar.doc_7.2.4/c_hwg_3105_allone _base.html 6. http://www.slideshare.net/anetertugrul/normal-artlarda-200-250-eps-logum-anca-oluyor-yksek- performansa-neden-ihtiya-duyaym 7. http://www.slideshare.net/anetertugrul/log-yonetiminde-cihaz-sayilari-ile-eps-degerleri-arasindaki- iliski 8. http://www.slideshare.net/anetertugrul/surelog-international-edition 9. https://www.netiq.com/documentation/sentinel70/s701_install/data/btmckgy.html#bwwvoik 10. http://blogs.gartner.com/anton-chuvakin/2014/06/17/on-siem-tool-and-operation-metrics/ 11. https://www.sans.org/reading-room/whitepapers/analyst/benchmarking-security-information-event- management-siem-34755 12. http://www.slideshare.net/NOVL/how-to-architect-a-novell-sentinel-implementation
