US Consumer Privacy Index 2016 – Infographic from TRUSTe & NCSA
•
0 gostou•1,240 visualizações
Infographic on the US consumer privacy and 2016 Data Privacy Day from TRUSTe and National Cyber Security Alliance (NCSA).
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
The State of Marketing Technology Today The State of Marketing Technology Today 

The State of Marketing Technology Today The State of Marketing Technology Today
The Third Wave of Enterprise Communications by Bryan Martin, 8x8

The Third Wave of Enterprise Communications by Bryan Martin, 8x8
The Evolution of Data Privacy: 3 things you didn’t know

The Evolution of Data Privacy: 3 things you didn’t know
No More Snake Oil: Why InfoSec Needs Security Guarantees

No More Snake Oil: Why InfoSec Needs Security Guarantees
15 Years of Web Security: The Rebellious Teenage Years

15 Years of Web Security: The Rebellious Teenage Years
Cobb Digital Bitesize workshop - GDPR, are you compliant?

Cobb Digital Bitesize workshop - GDPR, are you compliant?
Where Flow Charts Don’t Go -- Website Security Statistics Report (2015)

Where Flow Charts Don’t Go -- Website Security Statistics Report (2015)
The Evolution of Data Privacy: 3 Things You Need To Consider

The Evolution of Data Privacy: 3 Things You Need To Consider
Destaque
Destaque (16)
EU US Privacy Shield vs. GDPR Infographic from TRUSTe

EU US Privacy Shield vs. GDPR Infographic from TRUSTe
EU Privacy Shield - Understanding the New Framework from TRUSTe

EU Privacy Shield - Understanding the New Framework from TRUSTe
Building an Effective Data Privacy Program – 6 Steps from TRUSTe

Building an Effective Data Privacy Program – 6 Steps from TRUSTe
Interoperable Solutions for Cross Border Data Transfers – APEC, CBPR, BCR fro...

Interoperable Solutions for Cross Border Data Transfers – APEC, CBPR, BCR fro...
UX, ethnography and possibilities: for Libraries, Museums and Archives

UX, ethnography and possibilities: for Libraries, Museums and Archives
Webinar on New DAA Guidelines for Ads Compliance in 2016 from TRUSTe

Webinar on New DAA Guidelines for Ads Compliance in 2016 from TRUSTe
[Webinar Slides] Privacy Shield is Here – What You Need to Know![[Webinar Slides] Privacy Shield is Here – What You Need to Know](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Webinar Slides] Privacy Shield is Here – What You Need to Know](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Webinar Slides] Privacy Shield is Here – What You Need to Know
[Privacy Webinar Slides] Global Enforcement Priorities![[Privacy Webinar Slides] Global Enforcement Priorities](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Privacy Webinar Slides] Global Enforcement Priorities](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Privacy Webinar Slides] Global Enforcement Priorities
3 Things Every Sales Team Needs to Be Thinking About in 2017

3 Things Every Sales Team Needs to Be Thinking About in 2017
BigWeatherGear Group and Corporate Services Brochure 2013

BigWeatherGear Group and Corporate Services Brochure 2013
Semelhante a US Consumer Privacy Index 2016 – Infographic from TRUSTe & NCSA
Semelhante a US Consumer Privacy Index 2016 – Infographic from TRUSTe & NCSA (20)
White Paper: The 2015 State of Consumer Privacy & Personalization

White Paper: The 2015 State of Consumer Privacy & Personalization
TFOE - Social | A importância dos cookies e 1st party data para o e-commerce

TFOE - Social | A importância dos cookies e 1st party data para o e-commerce
State of the Industry: Creating a 360 View: Leveraging the Right Data for Tod...

State of the Industry: Creating a 360 View: Leveraging the Right Data for Tod...
X Series Programmatic - Publisher Audience Data - Ray Philipose - Olive Media

X Series Programmatic - Publisher Audience Data - Ray Philipose - Olive Media
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Verizon Media - Identity decoded apac_master leave behind

Verizon Media - Identity decoded apac_master leave behind
2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap

2018 Survey: Consumer Attitudes in a Post-Breach Era - The Generational Gap
Mais de TrustArc
Mais de TrustArc (20)
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
TrustArc Webinar - How to Live in a Post Third-Party Cookie World

TrustArc Webinar - How to Live in a Post Third-Party Cookie World
TrustArc Webinar - TrustArc's Latest AI Innovations

TrustArc Webinar - TrustArc's Latest AI Innovations
TrustArc Webinar - Managing Online Tracking Technology Vendors_ A Checklist f...

TrustArc Webinar - Managing Online Tracking Technology Vendors_ A Checklist f...
TrustArc Webinar - Privacy in Healthcare_ Ensuring Data Security

TrustArc Webinar - Privacy in Healthcare_ Ensuring Data Security
Unlocking AI Potential: Leveraging PIA Processes for Comprehensive Impact Ass...

Unlocking AI Potential: Leveraging PIA Processes for Comprehensive Impact Ass...
Mitigating Third-Party Risks: Best Practices for CISOs in Ensuring Robust Sec...

Mitigating Third-Party Risks: Best Practices for CISOs in Ensuring Robust Sec...
Nymity Framework: Privacy & Data Protection Update in 7 States

Nymity Framework: Privacy & Data Protection Update in 7 States
CBPR - Navigating Cross-Border Data Privacy Compliance

CBPR - Navigating Cross-Border Data Privacy Compliance
Everything You Need to Know about DPF But Are Afraid to Ask.pdf

Everything You Need to Know about DPF But Are Afraid to Ask.pdf
Your Guide to Understanding the Global Privacy Control (GPC): Preparing for C...

Your Guide to Understanding the Global Privacy Control (GPC): Preparing for C...
Privacy Enhancing Technologies: Exploring the Benefits and Recommendations

Privacy Enhancing Technologies: Exploring the Benefits and Recommendations
Building Trust and Competitive Advantage: The Value of Privacy Certifications

Building Trust and Competitive Advantage: The Value of Privacy Certifications
The California Age Appropriate Design Code Act Navigating the New Requirement...

The California Age Appropriate Design Code Act Navigating the New Requirement...
2023 Global Privacy Benchmarks Survey - Webinar May 30 2023.pdf

2023 Global Privacy Benchmarks Survey - Webinar May 30 2023.pdf
Artificial Intelligence Bill of Rights: Impacts on AI Governance

Artificial Intelligence Bill of Rights: Impacts on AI Governance
The Ultimate Balancing Act: Using Consumer Data and Maintaining Trust

The Ultimate Balancing Act: Using Consumer Data and Maintaining Trust
The Cost of Privacy Teams: What Your Business Needs To Know

The Cost of Privacy Teams: What Your Business Needs To Know
Último
Último (20)
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...

Automating Business Process via MuleSoft Composer | Bangalore MuleSoft Meetup...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Presentation on how to chat with PDF using ChatGPT code interpreter

Presentation on how to chat with PDF using ChatGPT code interpreter
US Consumer Privacy Index 2016 – Infographic from TRUSTe & NCSA
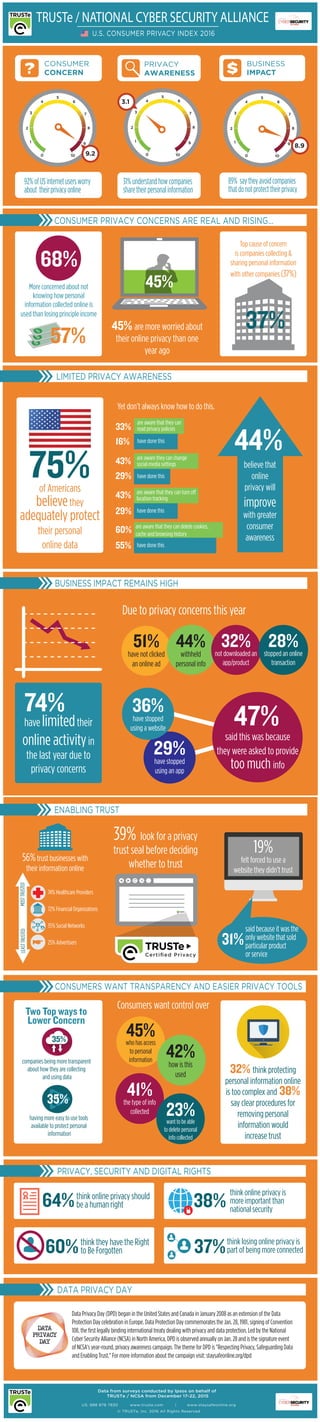
- 1. 0 1 2 3 4 5 6 7 8 9 10 9.2 0 1 2 3 4 5 6 7 8 9 10 8.9 0 1 2 3 4 5 6 7 8 9 10 3.1 45% 45% are more worried about their online privacy than one year ago Yet don’t always know how to do this. Top cause of concern is companies collecting & sharing personal information with other companies (37%) 37% 75%of Americans believethey adequately protect their personal online data 44% believe that online privacy will improve with greater consumer awareness have limitedtheir online activityin the last year due to privacy concerns 74% 51% have not clicked an online ad 44% withheld personal info 32%not downloaded an app/product 28%stopped an online transaction Due to privacy concerns this year CONSUMER PRIVACY CONCERNS ARE REAL AND RISING... LIMITED PRIVACY AWARENESS BUSINESS IMPACT REMAINS HIGH ENABLING TRUST Certified Privacy Certified Privacy 39% look for a privacy trust seal before deciding whether to trust CONSUMERS WANT TRANSPARENCY AND EASIER PRIVACY TOOLS 19% felt forced to use a website they didn’t trust PRIVACY, SECURITY AND DIGITAL RIGHTS 45%who has access to personal information 42% how is this used 41%the type of info collected 23%want to be able to delete personal info collected Consumers want control over 32% think protecting personal information online is too complex and 38% say clear procedures for removing personal information would increase trust 64%think online privacy should be a human right 38% think online privacy is more important than national security 37%think losing online privacy is part of being more connected60%think they have the Right to Be Forgotten DATA PRIVACY DAY Data Privacy Day (DPD) began in the United States and Canada in January 2008 as an extension of the Data Protection Day celebration in Europe. Data Protection Day commemorates the Jan. 28, 1981, signing of Convention 108, the first legally binding international treaty dealing with privacy and data protection. Led by the National Cyber Security Alliance (NCSA) in North America, DPD is observed annually on Jan. 28 and is the signature event of NCSA's year-round, privacy awareness campaign. The theme for DPD is "Respecting Privacy, Safeguarding Data and Enabling Trust." For more information about the campaign visit: staysafeonline.org/dpd Data from surveys conducted by Ipsos on behalf of TRUSTe / NCSA from December 17-22, 2015 US: 888 878 7830 www.truste.com | www.staysafeonline.org © TRUSTe, Inc. 2016 All Rights Reserved 56%trust businesses with their information online TRUSTe / NATIONAL CYBER SECURITY ALLIANCE U.S. CONSUMER PRIVACY INDEX 2016 are aware that they can delete cookies, cache and browsing history 60% 55% have done this 43% 29% are aware that they can turn off location tracking have done this 43% 29% are aware they can change social media settings have done this 33% 16% are aware that they can read privacy policies have done this 31% said because it was the only website that sold particular product or service 92%ofUSinternetusersworry about theirprivacyonline 31%understandhowcompanies sharetheirpersonalinformation 89% saytheyavoidcompanies thatdonotprotecttheirprivacy 74% Healthcare Providers 72% Financial Organizations 35% Social Networks 25% Advertisers LEASTTRUSTEDMOSTTRUSTED 29%have stopped using an app said this was because they were asked to provide too much info 47%36%have stopped using a website PRIVACY AWARENESS CONSUMER CONCERN BUSINESS IMPACT 68% More concerned about not knowing how personal information collected online is used than losing principle income 57% Two Top ways to Lower Concern 35% companies being more transparent about how they are collecting and using data having more easy to use tools available to protect personal information 35%
