Cyber Range - An Open-Source Offensive / Defensive Learning Environment on AWS
•
1 gostou•5,148 visualizações
This is the presentation of the SecDevOps-Cuse/CyberRange project. A project which aims to provide security researchers with a bootstrapped solution for building a personal research lab full of vulnerable assets, researcher tools, and well-known technologies like Nessus, Metasploit, FlareVM + many more...
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh Đông, Nguyễn Tuấn AnhUnrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...

Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...Vietnam Open Infrastructure User Group
Mais conteúdo relacionado
Mais procurados
Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh Đông, Nguyễn Tuấn AnhUnrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...

Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...Vietnam Open Infrastructure User Group
Mais procurados (20)
HKG18-402 - Build secure key management services in OP-TEE

HKG18-402 - Build secure key management services in OP-TEE
TEE - kernel support is now upstream. What this means for open source security

TEE - kernel support is now upstream. What this means for open source security
Six Degrees of Domain Admin - BloodHound at DEF CON 24

Six Degrees of Domain Admin - BloodHound at DEF CON 24
[cb22] Your Printer is not your Printer ! - Hacking Printers at Pwn2Own by A...![[cb22] Your Printer is not your Printer ! - Hacking Printers at Pwn2Own by A...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[cb22] Your Printer is not your Printer ! - Hacking Printers at Pwn2Own by A...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[cb22] Your Printer is not your Printer ! - Hacking Printers at Pwn2Own by A...
Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...

Unrevealed Story Behind Viettel Network Cloud Hotpot | Đặng Văn Đại, Hà Mạnh ...
Semelhante a Cyber Range - An Open-Source Offensive / Defensive Learning Environment on AWS
Semelhante a Cyber Range - An Open-Source Offensive / Defensive Learning Environment on AWS (20)
Control Plane: Continuous Kubernetes Security (DevSecOps - London Gathering, ...

Control Plane: Continuous Kubernetes Security (DevSecOps - London Gathering, ...
SFBay Area Solr Meetup - June 18th: Benchmarking Solr Performance

SFBay Area Solr Meetup - June 18th: Benchmarking Solr Performance
SANS @Night There's Gold in Them Thar Package Management Databases

SANS @Night There's Gold in Them Thar Package Management Databases
CERN OpenStack Cloud Control Plane - From VMs to K8s

CERN OpenStack Cloud Control Plane - From VMs to K8s
Unraveling Docker Security: Lessons From a Production Cloud

Unraveling Docker Security: Lessons From a Production Cloud
Tokyo OpenStack Summit 2015: Unraveling Docker Security

Tokyo OpenStack Summit 2015: Unraveling Docker Security
Deploying and managing SolrCloud in the cloud using the Solr Scale Toolkit

Deploying and managing SolrCloud in the cloud using the Solr Scale Toolkit
Kubernetes 101 for_penetration_testers_-_null_mumbai

Kubernetes 101 for_penetration_testers_-_null_mumbai
Securing your Container Environment with Open Source

Securing your Container Environment with Open Source
How containers helped a SaaS startup be developed and go live

How containers helped a SaaS startup be developed and go live
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Cyber Range - An Open-Source Offensive / Defensive Learning Environment on AWS
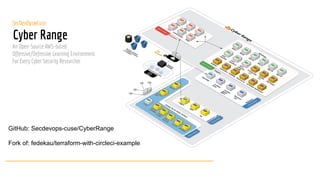
- 1. SecDevOps@Cuse Cyber Range An Open-Source AWS-based Offensive/Defensive Learning Environment For Every Cyber Security Researcher GitHub: Secdevops-cuse/CyberRange Fork of: fedekau/terraform-with-circleci-example
- 3. What & How Much?
- 4. Demo’s First Create the assetsShow what’s going to be setup / created
- 5. Technologies used AWS Git-Secrets Terraform Inspec Kali Packer Chocolatey Cloud-Init Vulnerable Assets: - Metasploitable 2 & 3 windows - Metasploitable 2 nix - Vulnhub vms - Damn Vulnerable* Researcher assets: - Commando - Kali - Remnux - Flarevm - T-Pot - DetectionLab* - HoneyPot Network*
- 6. Terraform - Environments / Region Example ./terraform environments/ ├── eu-west-2 └── us-east-1 eu-west-2/ ├── main.tf ├── terraform.tfvars ├── variables.tf └── versions.tf
- 7. Environment - Main.tf ● Setup provider ● Setup staging-state ● Setup s3 backend ● Setup the infrastructure Variables.tf
- 8. Terraform Tip - Securing Credentials Access Keys: Bad: provider "aws" { region = "eu-west-1" # Ireland region, change as you wish access_key = "1234567890" secret_key = "1234567890" } Good: provider "aws" { region = "${var.region}" shared_credentials_file = "${pathexpand("~/.aws/credentials")}" }
- 9. Infrastructure & Region - Main.tf
- 10. Infrastructure *aaS network/ ├── eips.tf ├── gateways.tf ├── output.tf ├── routes.tf ├── subnets.tf ├── variables.tf └── vpc.tf secdevops/ ├── attackers.tf ├── aws_ami.tf ├── aws_key_pairs.tf ├── ctf.playground.tf ├── honeyPots.tf ├── malware.tf ├── output.tf ├── security_groups.tf ├── security_groups_rules.tf ├── targets.nix.tf ├── targets.windows.tf ├── tenable.tf ├── variables.tf └── variables.tf.template ├── assets │ ├── network │ └── secdevops ├── cloud-init │ ├── awsinspector.setup.yml │ ├── bootstrap.commando.yml │ ├── bootstrap.flarevm.yml │ ├── bootstrap.windows.yml │ ├── docker.setup.yml │ ├── docker.targets.yml │ ├── docker.tools.yml │ ├── fbctf.setup.yml │ ├── kali.yml │ ├── tpot.setup.yml │ └── windows.bootstrap.yml ├── main.tf ├── output.tf └── variables.tf
- 11. CircleCI Build Workflow Configuration file: .circleci/config.yml Build, Plan, Apply Checks Note: terraform v0.12 was just released 5/23 Issue #21515: Apply Graph bug -> plan --out files are not being applied correctly. Workaround exists, impacts CI. Issue #21582: Apply --target does not create all network dependencies
- 13. AWS-Nuke Tips: ● Leveraged a dedicated Organization / Account ID ● 1 Region at a time ● Carefully review Dry-Run output ● Update white-list of required assets often ● Initialize early / Purge often
- 14. Next Phases of R&D
- 15. Inspec Tests Malware Lab - https://github.com/ytisf/theZoo https://www.malware-traffic-analysis.net/ https://cuckoo.sh/docs/installation/guest/linux.html https://github.com/aol/moloch https://github.com/killswitch-GUI/Fuzz-FFmpeg Future Research
- 16. Future Research Packer: http://jen20.com/2015/04/02/windows-amis-without-the-tears.html https://operator-error.com/2018/04/16/windows-amis-with-even/ Compiler Explorers: https://godbolt.org/ HoneyPot Network - https://github.com/threatstream/agave
