SANS 2017 Cyber Security Trend Report Checklist
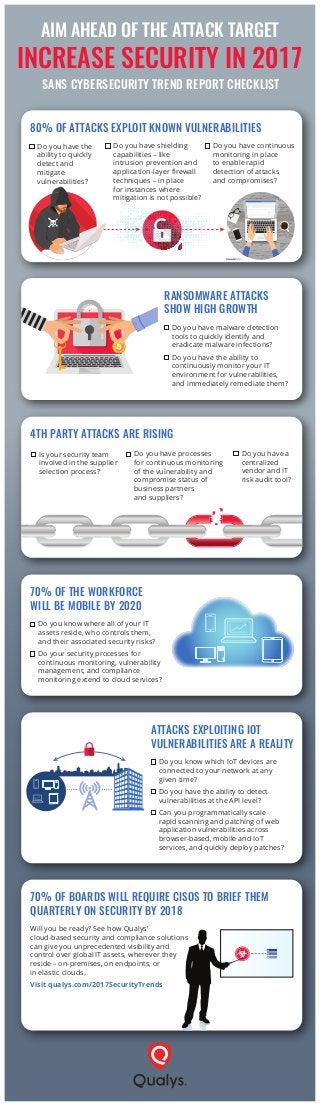
Aim Ahead of the Attack Target to Increase Security in 2017 A new trend report authored by John Pescatore of the SANS Institute focuses on the latest and best security hygiene and common success patterns that will prevent your organization from falling victim to major data breaches. Cyber security trends clearly show that attacks on computer networks will continue, and many will succeed. Additionally, organizations must expand current security measures in order to better protect data in the cloud and to address the security shortcomings of the Internet of Things. The cybersecurity trends that will continue to prevail in 2017 include: - Known vulnerabilities continue to dominate — 80% of cybersecurity attacks exploit known vulnerabilities - Breaches aren’t the entire story — ransomware attacks show high growth - Fourth-party attacks are increasing — attacker trends moving further out in the supply chain to include subcontractors, outsourcers and more Download the report: https://www.qualys.com/2017SecurityTrends Free trial: https://www.qualys.com/forms/trials/suite/ Contact Qualys for more information: 800.745.4355 https://www.qualys.com/company/contacts
Recomendados
Recomendados
Mais conteúdo relacionado
Mais de Qualys
Mais de Qualys (6)
Último
Último (20)
SANS 2017 Cyber Security Trend Report Checklist
- 1. AIM AHEAD OF THE ATTACK TARGET INCREASE SECURITY IN 2017 RANSOMWARE ATTACKS SHOW HIGH GROWTH ■ Do you have malware detection tools to quickly identify and eradicate malware infections? ■ Do you have the ability to continuously monitor your IT environment for vulnerabilities, and immediately remediate them? 70% OF THE WORKFORCE WILL BE MOBILE BY 2020 ■ Do you know where all of your IT assets reside, who controls them, and their associated security risks? ■ Do your security processes for continuous monitoring, vulnerability management, and compliance monitoring extend to cloud services? 70% OF BOARDS WILL REQUIRE CISOS TO BRIEF THEM QUARTERLY ON SECURITY BY 2018 Will you be ready? See how Qualys’ cloud-based security and compliance solutions can give you unprecedented visibility and control over global IT assets, wherever they reside – on-premises, on endpoints, or in elastic clouds. Visit qualys.com/2017SecurityTrends 80% OF ATTACKS EXPLOIT KNOWN VULNERABILITIES ■ Do you have the ability to quickly detect and mitigate vulnerabilities? ■ Do you have shielding capabilities – like intrusion prevention and application-layer firewall techniques – in place for instances where mitigation is not possible? ■ Do you have continuous monitoring in place to enable rapid detection of attacks and compromises? 4TH PARTY ATTACKS ARE RISING ■ Is your security team involved in the supplier selection process? ■ Do you have processes for continuous monitoring of the vulnerability and compromise status of business partners and suppliers? ■ Do you have a centralized vendor and IT risk audit tool? ATTACKS EXPLOITING IOT VULNERABILITIES ARE A REALITY ■ Do you know which IoT devices are connected to your network at any given time? ■ Do you have the ability to detect vulnerabilities at the API level? ■ Can you programmatically scale rapid scanning and patching of web application vulnerabilities across browser-based, mobile and IoT services, and quickly deploy patches? SANS CYBERSECURITY TREND REPORT CHECKLIST
