W4 profinet frame analysis handout, peter thomas
•
0 gostou•1,051 visualizações
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
IAB-5039 : MQTT: A Protocol for the Internet of Things (InterConnect 2015)

IAB-5039 : MQTT: A Protocol for the Internet of Things (InterConnect 2015)
EC 6802 WIRELESS NETWORK_ BABU M_ unit 3 ,4 & 5 PPT

EC 6802 WIRELESS NETWORK_ BABU M_ unit 3 ,4 & 5 PPT
4. Internet of Things - Reference Model and Architecture

4. Internet of Things - Reference Model and Architecture
Destaque
To gain an understanding of the way in which
PROFINET devices communicate with one
another over Ethernet.
• To learn how to capture the PROFINET
Frames using Wireshark®.
• To see how Wireshark® can be used to analyse
the captured frames to gain an understanding
of the various protocols.
• This is a topic covered in more detail in the
Certified PROFINET Engineers CoursePROFIBUS frame analysis - Peter Thomas of Control Specialists

PROFIBUS frame analysis - Peter Thomas of Control SpecialistsPROFIBUS and PROFINET InternationaI - PI UK
Destaque (9)
Introduction to Profibus & Profinet - Mark Freeman

Introduction to Profibus & Profinet - Mark Freeman
Industrial Ethernet Facts - The 5 major technologies

Industrial Ethernet Facts - The 5 major technologies
PROFIsafe and IT security - Peter Brown of Siemens A&D

PROFIsafe and IT security - Peter Brown of Siemens A&D
PROFIBUS frame analysis - Peter Thomas of Control Specialists

PROFIBUS frame analysis - Peter Thomas of Control Specialists
Semelhante a W4 profinet frame analysis handout, peter thomas
IJRET : International Journal of Research in Engineering and Technology is an international peer reviewed, online journal published by eSAT Publishing House for the enhancement of research in various disciplines of Engineering and Technology. The aim and scope of the journal is to provide an academic medium and an important reference for the advancement and dissemination of research results that support high-level learning, teaching and research in the fields of Engineering and Technology. We bring together Scientists, Academician, Field Engineers, Scholars and Students of related fields of Engineering and Technology.Design and implementation of an ancrchitecture of embedded web server for wir...

Design and implementation of an ancrchitecture of embedded web server for wir...eSAT Publishing House
Semelhante a W4 profinet frame analysis handout, peter thomas (20)
The pattern and realization of zigbee wi-fi wireless pathway

The pattern and realization of zigbee wi-fi wireless pathway
Opnet based simulation and investigation of wimax network using different qo s

Opnet based simulation and investigation of wimax network using different qo s
Design and implementation of an ancrchitecture of embedded web server for wir...

Design and implementation of an ancrchitecture of embedded web server for wir...
Design and implementation of an ancrchitecture of embedded web server for wir...

Design and implementation of an ancrchitecture of embedded web server for wir...
Advancing VLSI Design Reliability: A Comprehensive Examination of Embedded De...

Advancing VLSI Design Reliability: A Comprehensive Examination of Embedded De...
Multi port network ethernet performance improvement techniques

Multi port network ethernet performance improvement techniques
Connected Vehicles, Zonal In Vehicle Network Architecture

Connected Vehicles, Zonal In Vehicle Network Architecture
Mais de PROFIBUS and PROFINET InternationaI - PI UK
New for 2022 - You will now be able to study remotely to gain international accrediation in PROFIBUS and PROFINETPI UK Seminar (Nov 2021) - Online Certified Training Courses

PI UK Seminar (Nov 2021) - Online Certified Training CoursesPROFIBUS and PROFINET InternationaI - PI UK
Auditing a PROFINET NetworkPI UK Seminar (Nov 2021) - PROFINET Implementation and Testing

PI UK Seminar (Nov 2021) - PROFINET Implementation and TestingPROFIBUS and PROFINET InternationaI - PI UK
How to configure the run time parameters of PROFIBUS and PROFINET devices.PI UK Seminar (Nov 2021) - PROFIBUS and PROFINET Device Configuration

PI UK Seminar (Nov 2021) - PROFIBUS and PROFINET Device ConfigurationPROFIBUS and PROFINET InternationaI - PI UK
For people responsible for the design, commissioning and support of PROFINET networks, explaining how to integrate existing PROFIBUS DP and PROFIBUS PA devices into that network. The webinar took the form of a presentation with demonstrations to aid understanding.PROFINET to PROFIBUS gateways - Peter Thomas - 03 june 2020

PROFINET to PROFIBUS gateways - Peter Thomas - 03 june 2020PROFIBUS and PROFINET InternationaI - PI UK
For people responsible for the commissioning and support of PROFIBUS networks. The webinar took the form of a presentation with demonstrations to aid understanding.PROFIBUS lightning surge protection - Peter Thomas, CSL - 10 june 2020 

PROFIBUS lightning surge protection - Peter Thomas, CSL - 10 june 2020 PROFIBUS and PROFINET InternationaI - PI UK
This 40-minute long webinar follows on from the PROFINET Network Design Webinar but is this time intended for people responsible for the commissioning and support of PROFINET networks. The webinar took the form of a presentation with demonstrations to aid understanding. PROFINET network diagnostics and support - May 2020 - Peter Thomas

PROFINET network diagnostics and support - May 2020 - Peter ThomasPROFIBUS and PROFINET InternationaI - PI UK
Mais de PROFIBUS and PROFINET InternationaI - PI UK (20)
PI UK Seminar (Nov 2021) - Online Certified Training Courses

PI UK Seminar (Nov 2021) - Online Certified Training Courses
PI UK Seminar (Nov 2021) - PROFINET Implementation and Testing

PI UK Seminar (Nov 2021) - PROFINET Implementation and Testing
PI UK Seminar (Nov 2021) - PROFIBUS and PROFINET Device Configuration

PI UK Seminar (Nov 2021) - PROFIBUS and PROFINET Device Configuration
PROFINET to PROFIBUS gateways - Peter Thomas - 03 june 2020

PROFINET to PROFIBUS gateways - Peter Thomas - 03 june 2020
PROFIBUS lightning surge protection - Peter Thomas, CSL - 10 june 2020 

PROFIBUS lightning surge protection - Peter Thomas, CSL - 10 june 2020
PROFINET network diagnostics and support - May 2020 - Peter Thomas

PROFINET network diagnostics and support - May 2020 - Peter Thomas
Último
Último (20)
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Tech Trends Report 2024 Future Today Institute.pdf

Tech Trends Report 2024 Future Today Institute.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
W4 profinet frame analysis handout, peter thomas
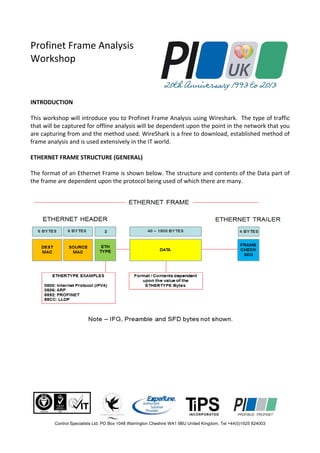
- 1. Control Specialists Ltd. PO Box 1048 Warrington Cheshire WA1 9BU United Kingdom. Tel +44(0)1925 824003 Profinet Frame Analysis Workshop INTRODUCTION This workshop will introduce you to Profinet Frame Analysis using Wireshark. The type of traffic that will be captured for offline analysis will be dependent upon the point in the network that you are capturing from and the method used. WireShark is a free to download, established method of frame analysis and is used extensively in the IT world. ETHERNET FRAME STRUCTURE (GENERAL) The format of an Ethernet Frame is shown below. The structure and contents of the Data part of the frame are dependent upon the protocol being used of which there are many.
- 2. Profinet Frame Analysis using Wireshark Version 1.0 ____________________________________________________________________________ ________________________________________________________________________________ www.controlspecialists.co.uk 2 ETHERNET FRAME STRUCTURE (WIRESHARK ‐ PNIO) COMMON PROTOCOLS For each frame, Wireshark will identify the protocol that the frame conforms to. For Profinet networks, the most common are:‐ ARP (Address Resolution Protocol) This is a protocol that is used to associate the hardware (MAC) address of a device with an IP address. Initially, a request is made using the format “who has this IP address? Send answer to me”. The response from the device with the given IP address is “I have the requested IP address and my MAC address is as follows”. By definition, ARP’s are sent to broadcast addresses so that every device has the opportunity of responding. LLDP (Link Layer Discovery Protocol) A protocol used by devices to announce their presence on the network and their capabilities. This Protocol can be used by a Profinet System to determine who is connected to who and for automatic assignment of a device name to a device when a replacement is added to the network.
- 3. Profinet Frame Analysis using Wireshark Version 1.0 ____________________________________________________________________________ ________________________________________________________________________________ www.controlspecialists.co.uk 3 PN‐DCP (Discovery and Configuration Protocol) This is a Profinet‐specific protocol that has two main functions: 1. Used by the Supervisor (PC) to assign a unique name (Siemens Primary Setup Tool / Procentec Netilities). 2. Used by the IO Controller (CPU) to assign a unique IP address (as defined in the hardware config) in conjunction with ARP above. PNIO‐CM (Profinet IO Context Manager) This is a Profinet‐specific protocol that is used to configure the AR (Application Relations) and CR (Communication Relations) between a controller and an IO device. This process will ultimately determine the amount and type of data that will be transmitted between the pair. There are several stages of the start‐up procedure using the Context Manager with the flow usually being as follows:‐ CONNECT request from IO Controller followed by a CONNECT response from IO Device WRITE request from IO Controller followed by a WRITE response from IO Device DCONTROL request from IO Controller followed by a DCONTROL response from IO Device CCONTROL request from IO Controller followed by a CCONTROL response from IO Device PN‐PTCP (Precision Transparent Clock Protocol) This is a layer 2 Profinet‐specific protocol used to ensure time synchronisation on the network. PNIO Profinet Data Exchange Traffic PNIO‐AL Profinet Alarm Events
- 4. Profinet Frame Analysis using Wireshark Version 1.0 ____________________________________________________________________________ ________________________________________________________________________________ www.controlspecialists.co.uk 4 NETWORK 1 EX01 Start‐Up, Data Exchange, Loss of Module EX01 ‐ FRAME CAPTURE Put the CPU into STOP Mode and remove power from it. Launch WireShark. Select the Interface that Wireshark will capture frames from. Start the Capturing process. Apply power to the CPU. After approx. 15s, put the CPU into RUN mode. After a further 15s, remove an IO module. Insert the module back into its slot shortly after. Stop the capture process after approx. 30s.
- 5. Profinet Frame Analysis using Wireshark Version 1.0 ____________________________________________________________________________ ________________________________________________________________________________ www.controlspecialists.co.uk 5 EX01 Start‐Up, Data Exchange, Loss of Module (Continued) EX01 ‐ FRAME ANALYSIS Click on the “Profinet DCP” Filter Expression Button and observe to CPU setting the IP addresses of the Profinet devices. Click on the “ARP” Filter Expression Button and observe the CPU looking for devices with specific IP addresses. Click on the “Profinet CM” Filter Expression Button and look for PNIO‐CM entries that show the CONNECT – WRITE – APP READY start‐up procedure. Click on the “Profinet Data (Good)” Filter Expression Button and look for PNIO entries that show data exchange. Click on the “Profinet Data (Bad)” Filter Expression Button and look for PNIO entries that show data exchange. Click on the “Profinet Alarms” Filter Expression Button and look for PNIO‐AL entries that show alarm events. EX02 Duplicate Device Name EX02 ‐ FRAME CAPTURE Put the CPU into STOP Mode. Make a direct Ethernet connection from the laptop to the IM153‐3. Use the Primary Setup Tool to rename the device to “wago‐750‐370” – without the quotes. Connect the IM153‐3 onto the original network. Put the CPU into RUN Mode. Note the status of the IM153‐3: _______________________________________ Note the status of the WAGO 750‐370 _______________________________________ Remove power from the CPU for a few seconds and then reapply. Wait a few seconds for the PLC to go into RUN mode. Note the status of the IM153‐3: _______________________________________ Note the status of the WAGO 750‐370: _______________________________________
- 6. Profinet Frame Analysis using Wireshark Version 1.0 ____________________________________________________________________________ ________________________________________________________________________________ www.controlspecialists.co.uk 6 Launch WireShark. Select the Interface that Wireshark will capture frames from. Start the Capturing process. Stop the capture process after approx. 30s. EX02 Duplicate Device Name (Continued) EX02 ‐ FRAME ANALYSIS Click on the “Profinet DCP” Filter Expression Button and observe attempts by the CPU to find the Profinet devices. __________________________________________________________________
