JVM.pptx
•Transferir como PPTX, PDF•
0 gostou•123 visualizações
java
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Semelhante a JVM.pptx
Semelhante a JVM.pptx (20)
Último
Making communications land - Are they received and understood as intended? webinar
Thursday 2 May 2024
A joint webinar created by the APM Enabling Change and APM People Interest Networks, this is the third of our three part series on Making Communications Land.
presented by
Ian Cribbes, Director, IMC&T Ltd
@cribbesheet
The link to the write up page and resources of this webinar:
https://www.apm.org.uk/news/making-communications-land-are-they-received-and-understood-as-intended-webinar/
Content description:
How do we ensure that what we have communicated was received and understood as we intended and how do we course correct if it has not.Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...Association for Project Management
https://app.box.com/s/7hlvjxjalkrik7fb082xx3jk7xd7liz3TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...

TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...Nguyen Thanh Tu Collection
Último (20)
Fostering Friendships - Enhancing Social Bonds in the Classroom

Fostering Friendships - Enhancing Social Bonds in the Classroom
Basic Civil Engineering first year Notes- Chapter 4 Building.pptx

Basic Civil Engineering first year Notes- Chapter 4 Building.pptx
ICT Role in 21st Century Education & its Challenges.pptx

ICT Role in 21st Century Education & its Challenges.pptx
Python Notes for mca i year students osmania university.docx

Python Notes for mca i year students osmania university.docx
Making communications land - Are they received and understood as intended? we...

Making communications land - Are they received and understood as intended? we...
Vishram Singh - Textbook of Anatomy Upper Limb and Thorax.. Volume 1 (1).pdf

Vishram Singh - Textbook of Anatomy Upper Limb and Thorax.. Volume 1 (1).pdf
This PowerPoint helps students to consider the concept of infinity.

This PowerPoint helps students to consider the concept of infinity.
TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...

TỔNG ÔN TẬP THI VÀO LỚP 10 MÔN TIẾNG ANH NĂM HỌC 2023 - 2024 CÓ ĐÁP ÁN (NGỮ Â...
General Principles of Intellectual Property: Concepts of Intellectual Proper...

General Principles of Intellectual Property: Concepts of Intellectual Proper...
JVM.pptx
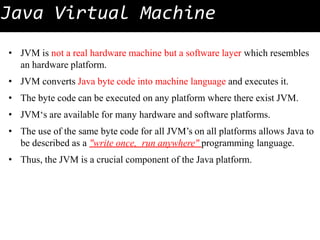
- 1. Java Virtual Machine • JVM is not a real hardware machine but a software layer which resembles an hardware platform. • JVM converts Java byte code into machine language and executes it. • The byte code can be executed on any platform where there exist JVM. • JVM‘s are available for many hardware and software platforms. • The use of the same byte code for all JVM’s on all platforms allows Java to be described as a "write once, run anywhere" programming language. • Thus, the JVM is a crucial component of the Java platform.
- 2. Diagram Of JVM Java Source Code(.java) Java Object Code(.class) Java Compiler (javac) Computer Operating System Java Interpreter Java Virtual Machine Object Code is loaded into Java Virtual Machine
- 3. Components Of JVM Class Loader Execution Engine Run-time data areas Java Virtual Machine .class file
- 4. Components Of JVM 1. Byte code verifier 2. Class loader 3. Execution engine 4. Garbage collector 5. Security Manager
- 5. 1. Byte code Verifier: • Byte code verifier is used to verify the byte code. • Also checks for unusual code. • So it is a crucial component for security. 2. Class loader: • Class loader loads java classes into java virtual machine and creates the instance of java.lang.class. • The main feature is that JVM doesn’t need to have any knowledge about the classes that will be loaded at runtime. • It performs three main functions of JVM, namely: loading, linking and initialization
- 6. 3. Execution Engine: • The execution engine helps JVM to convert bytecode into machine code. • It has two parts: a) Interpreter b) Just-in-time-interpreter • Execution engine is responsible for executing the instructions contained in the methods of loaded classes. 4. Garbage Collector: • Garbage collection is the process of automatically freeing objects that are no longer referenced by the program. • It periodically check for the object on heap , whose link is broken so it can collect garbage from heap. • Garbage collection relieves java programmer from memory management.
- 7. 5. Security Manager: • Security manager constantly monitors the code. • It is a special java object that is responsible for guarding security policies for java applications. • It is always consulted before any potentially dangerous operation is requested by a java application.