MBM Security Products Matrix
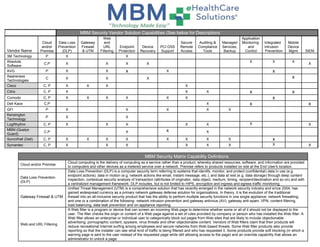
- 1. MBM Security Vendor Solution Capabilities (See below for Descriptions) Vendor Name Cloud and/or Premise Data Loss Prevention (DLP) Gateway Firewall & UTM Web and URL Filtering Endpoint Protection Device Recovery PCI DSS Support Secure Remote Access Auditing & Compliance Tools Managed Services, Backup Application Monitoring and Control Integrated Intrusion Prevention Mobile Device Mgmt SIEM 3M Technology P X X Absolute Software C,P X X X X X X X X AVG P X X x X x Awareness Technologies C X X X x Cisco C, P X X X X Citrix C, P X X X x x Comodo C, P X X X X X X x Dell Kace C,P X x x GFI P X X X X X Kensington Technology P X X LogRhythm C, P X X X X X X X MBM (Qualys Guard) C,P X x X SonicWall (Dell) C, P X X X X X X X X x Symantec C, P X X X X X X X X MBM Security Matrix Capability Definitions Cloud and/or Premise Cloud computing is the delivery of computing as a service rather than a product, whereby shared resources, software, and information are provided to computers and other devices as a metered service over a network. Premise refers to products installed on site at the End User's location. Data Loss Prevention (DLP) Data Loss Prevention (DLP) is a computer security term referring to systems that identify, monitor, and protect (confidential) data in use (e.g. endpoint actions), data in motion (e.g. network actions like email, instant message, etc.), and data at rest (e.g. data storage) through deep content inspection, contextual security analysis of transaction (attributes of originator, data object, medium, timing, recipient/destination and so on) and with a centralized management framework. DLP includes, but is not limited to HIPS, encryption and ingress and egress traffic monitoring. Gateway Firewall & UTM Unified Threat Management (UTM) is a comprehensive solution that has recently emerged in the network security industry and since 2004, has gained widespread currency as a primary network gateway defense solution for organizations. In theory, it is the evolution of the traditional firewall into an all-inclusive security product that has the ability to perform multiple security functions in one single appliance: network firewalling, and one or a combination of the following- network intrusion prevention and gateway antivirus (AV), gateway anti-spam, VPN, content filtering, load balancing, data leak prevention and on-appliance reporting. Web and URL Filtering A Web filter is a program or device that can screen an incoming Web page to determine whether some or all of it should not be displayed to the user. The filter checks the origin or content of a Web page against a set of rules provided by company or person who has installed the Web filter. A Web filter allows an enterprise or individual user to categorically block out pages from Web sites that are likely to include objectionable advertising, pornographic content, spyware, virus threats and other objectionable content. Vendors of Web filters claim that their products will reduce recreational Internet surfing among employees and secure networks from Web-based threats. Some Web filter products also provide reporting so that the installer can see what kind of traffic is being filtered and who has requested it. Some products provide soft blocking (in which a warning page is sent to the user instead of the requested page while still allowing access to the page) and an override capability that allows an administrator to unlock a page.
- 2. Endpoint Protection In network security, endpoint security refers to a methodology of protecting the corporate network when accessed via remote devices such as laptops or other wireless and mobile devices. Each device with a remote connecting to the network creates a potential entry point for security threats. Endpoint security is designed to secure each endpoint on the network created by these devices. Usually, endpoint security is a security system that consists of security software, located on a centrally managed and accessible server or gateway within the network, in addition to client software being installed on each of the endpoints (or devices). The server authenticates logins from the endpoints and also updates the device software when needed. While endpoint security software differs by vendor, you can expect most software offerings to provide antivirus, antispyware, firewall and also a host intrusion prevention system (HIPS). Device Recovery Locate and lock mobile devices. Selectively wipe files and other data on devices to protect company data while preserving employees’ personal data. Wipe devices completely if necessary. PCI DSS Support The Payment Card Industry Data Security Standard (PCI DSS) is a widely accepted set of policies and procedures intended to optimize the security of credit, debit and cash card transactions and protect cardholders against misuse of their personal information. The PCI DSS was created jointly in 2004 by four major credit-card companies: Visa, MasterCard, Discover and American Express. Secure Remote Access The ability to SECURELY log onto a network from a remote location usually involving an encrypted session. Generally, this implies a computer, a modem or network connection, and some remote access software to connect to the network. Auditing/Compliance Tools HIPAA states that a security management process must exist in order to protect against "attempted or successful unauthorized access, use, disclosure, modification, or interference with system operations". In other words being able to monitor, report and alert on attempted or successful access to systems and applications that contain sensitive patient information. Managed Services, Backup Managed services providers can offer services such as alerts, security, patch management, data backup and recovery for different client devices: desktops, notebooks, servers, storage systems, networks and applications Application Monitoring and Control Application monitoring can be time-consuming and tedious, but utilities that automate monitoring and management can reduce the workload substantially. A comprehensive application monitoring solution will automatically identify the systems on a network and the applications they are running and create concise summaries for the administrator. Application monitoring solutions allow an administrator to effectively manage very large IT infrastructures. SIEM Security Information and Event Management (SIEM) is a term for software and products services combining security information management (SIM) and security event manager (SEM). SIEM technology provides real-time analysis of security alerts generated by network hardware and applications. SIEM is sold as software, appliances or managed services, and are also used to log security data and generate reports for compliance purposes. Integrated Intrusion Prevention Multi-Threat security and content protection - blended threats, intrusion attempts, viruses, Trojans, worms, spyware, grayware, adware and denials of service Mobile Device Management (MDM) Mobile Device Management (MDM) software secures, monitors, manages and supports mobile devices deployed across mobile operators, service providers and enterprises. MDM functionality typically includes over-the-air distribution of applications, data and configuration settings for all types of mobile devices, including mobile phones, smartphones, tablet computers, ruggedized mobile computers, mobile printers, mobile POS devices, etc