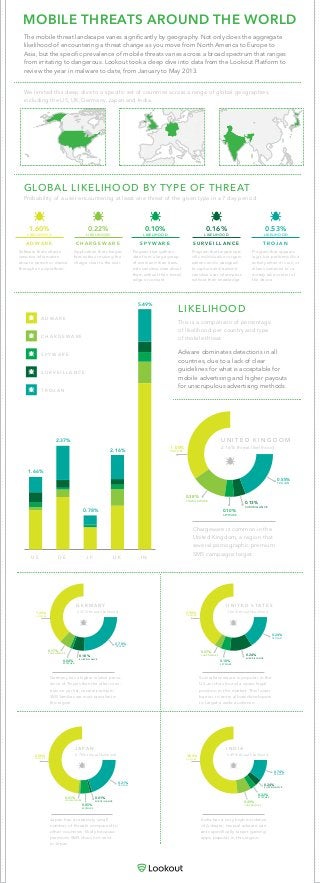
World of Mobile Threats: UK
- 1. MOBILE THREATS AROUND THE WORLD The mobile threat landscape varies significantly by geography. Not only does the aggregate likelihood of encountering a threat change as you move from North America to Europe to Asia, but the specific prevalence of mobile threats varies across a broad spectrum that ranges from irritating to dangerous. Lookout took a deep dive into data from the Lookout Platform to review the year in malware to date, from January to May 2013. Adware dominates detections in all countries, due to a lack of clear guidelines for what is acceptable for mobile advertising and higher payouts for unscrupulous advertising methods. A D W A R E C H A R G E W A R E S P Y W A R E S U R V E I L L A N C E T R O J A N U S 1.66% D E 2.37% J P 0.78% U K 2.16% I N 5.49% LIKELIHOOD Chargeware is common in the United Kingdom, a region that several pornographic premium SMS campaigns target. This is a comparison of percentage of likelihood per country and type of mobile threat. GLOBAL LIKELIHOOD BY TYPE OF THREAT Probability of a user encountering at least one threat of the given type in a 7 day period. We limited this deep dive to a specific set of countries across a range of global geographies, including the US, UK, Germany, Japan and India. Germany has a higher relative preva- lence of Trojans than the other coun- tries on our list; several premium SMS families are most prevalent in this region. Surveillanceware is popular in the US as it has found a quasi-legal position in the market. This lower barrier to entry allows developers to target a wide audience. Japan has a relatively small number of threats compared to other countries, likely because premium SMS does not exist in Japan. India has a very high incidence of Adware; several adware vari- ants specifically target gaming apps popular in this region. A D W A R E LIKELIHOOD 1.60% Software that collects sensitive information about a person or device through an ad platform. C H A R G E W A R E LIKELIHOOD 0.22% Application that charges fees without making the charge clear to the user. S P Y W A R E LIKELIHOOD 0.10% Program that gathers data from a large group of users and then trans- mits sensitive data about them without their knowl- edge or consent. S U R V E I L L A N C E LIKELIHOOD 0.16% Program that targets spe- cific individuals or organi- zations and is designed to capture and transmit sensitive user information without their knowledge. T R O J A N LIKELIHOOD 0.53% Program that appears legit, but performs illicit activity when it is run, or allows someone to re- motely take control of the device. 1.20% ADWARE 0.17% CHARGEWARE 0.18% SURVEILLANCE 0.78% TROJAN 0.04% SPYWARE G E R M A N Y 2.37% threat likelihood 0.50% ADWARE 0.01% CHARGEWARE 0.01% SURVEILLANCE 0.21% TROJAN 0.05% SPYWARE J A P A N 0.78% threat likelihood 3.80% ADWARE 0.49% CHARGEWARE 0.24% SURVEILLANCE 0.74% TROJAN 0.22% SPYWARE I N D I A 5.49% threat likelihood 1 .00% ADWARE 0.38% CHARGEWARE 0.13% SURVEILLANCE 0.55% TROJAN 0.10% SPYWARE U N I T E D K I N G D O M 2.16% threat likelihood 0.90% ADWARE 0.07% CHARGEWARE 0.24% SURVEILLANCE 0.24% TROJAN 0.10% SPYWARE U N I T E D S T A T E S 1.66% threat likelihood
