ISACA State of Cyber Security 2017
•
2 gostaram•1,831 visualizações
A look at the state of the cyber security workforce.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Estudio de Russell Reynolds Associates sobre ciberseguridad que explora la importancia de la relación entre el Chief Information Security Officer y el Consejo de Administración. Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Recomendados
Estudio de Russell Reynolds Associates sobre ciberseguridad que explora la importancia de la relación entre el Chief Information Security Officer y el Consejo de Administración. Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Reinforcing the Revolution: The Promise and Perils of Digital Transformation

Reinforcing the Revolution: The Promise and Perils of Digital Transformation
Cyber-risk Oversight Handbook for Corporate Boards

Cyber-risk Oversight Handbook for Corporate Boards
Infographic - Three steps to stopping advanced email threats

Infographic - Three steps to stopping advanced email threats
Cybersecurity: Cyber Risk Management for Banks & Financial Institutions

Cybersecurity: Cyber Risk Management for Banks & Financial Institutions
Cybersecurity in the Cognitive Era: Priming Your Digital Immune System

Cybersecurity in the Cognitive Era: Priming Your Digital Immune System
Adapted from an ESG report - Outnumbered, Outgunned. 

Adapted from an ESG report - Outnumbered, Outgunned.
Destaque
Destaque (20)
COBIT 5 Infographic: Extracting Value From Information Chaos

COBIT 5 Infographic: Extracting Value From Information Chaos
The difference between Cybersecurity and Information Security

The difference between Cybersecurity and Information Security
Symantec Internet Security Threat Report 2014 - Volume 19

Symantec Internet Security Threat Report 2014 - Volume 19
Industrial Control System Cyber Security and the Employment of Industrial Fir...

Industrial Control System Cyber Security and the Employment of Industrial Fir...
Semelhante a ISACA State of Cyber Security 2017
Russell Reynolds Associates aborda cinco cuestiones de liderazgo en materia de ciberseguridad que los Consejos de Administración y los ejecutivos deben preguntarse. Estas cuestiones abarcan diversos aspectos, desde el nivel de preparación del Consejo hasta la gestión del talento para proteger el negocio de una forma integral.Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attentionRamón Gómez de Olea y Bustinza
Semelhante a ISACA State of Cyber Security 2017 (20)
Cybersecurity Talent : The Big Gap in Cyber Protection

Cybersecurity Talent : The Big Gap in Cyber Protection
Achieving Holistic Cybersecurity: 2016 Progress Report

Achieving Holistic Cybersecurity: 2016 Progress Report
ISACA and RSA CSX Presentation from the RSA 2015 Conference 

ISACA and RSA CSX Presentation from the RSA 2015 Conference
2013-ISC2-Global-Information-Security-Workforce-Study

2013-ISC2-Global-Information-Security-Workforce-Study
Prof m01-2013 global information security workforce study - final

Prof m01-2013 global information security workforce study - final
State-of-Cybersecurity-2022_WHPSC22_res_eng_0322.pdf

State-of-Cybersecurity-2022_WHPSC22_res_eng_0322.pdf
Study master of cyber security at australia with scholarship

Study master of cyber security at australia with scholarship
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attention
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
08448380779 Call Girls In Civil Lines Women Seeking Men

08448380779 Call Girls In Civil Lines Women Seeking Men
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...

Raspberry Pi 5: Challenges and Solutions in Bringing up an OpenGL/Vulkan Driv...
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
ISACA State of Cyber Security 2017
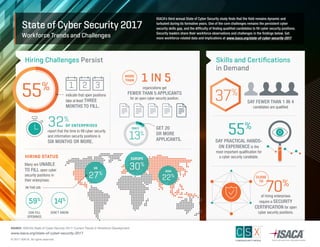
- 1. State of Cyber Security 2017 Workforce Trends and Challenges ISACA’s third annual State of Cyber Security study finds that the field remains dynamic and turbulent during its formative years. One of the core challenges remains the persistent cyber security skills gap, and the difficulty of finding qualified candidates to fill cyber security positions. Security leaders share their workforce observations and challenges in the findings below. Get more workforce-related data and implications at www.isaca.org/state-of-cyber-security-2017. Skills and Certifications in Demand Hiring Challenges Persist organizations get FEWER THAN 5 APPLICANTS for an open cyber security position. indicate that open positions take at least THREE MONTHS TO FILL. report that the time to fill cyber security and information security positions is SIX MONTHS OR MORE. 55% IN THE US: EUROPE 30% ASIA 22% HIRING STATUS US 27% Many are UNABLE TO FILL open cyber security positions in their enterprises: 1 IN 5 55% SAY PRACTICAL HANDS- ON EXPERIENCE is the most important qualification for a cyber security candidate. 59% DON’T KNOW 14% CAN FILL OPENINGS SOURCE: ISACA’s State of Cyber Security 2017: Current Trends in Workforce Development www.isaca.org/state-of-cyber-security-2017 © 2017 ISACA. All rights reserved. MORE THAN 32% OF ENTERPRISES GET 20 OR MORE APPLICANTS.13% ONLY 70% of hiring enterprises require a SECURITY CERTIFICATION for open cyber security positions. CLOSE TO 1 2 3 SAY FEWER THAN 1 IN 4 candidates are qualified 37%
