Denunciar
Compartilhar
Baixar para ler offline
Recomendados
The FAIR principles have been introduced as a guideline for good scientific data stewardship. They have gained momentum at a management level and are now for example part of the project template for EU Horizon 2020 projects. This raises the question what research groups and projects can do to implement them. Hugo Besemer will introduce the ideas behind the FAIR principles.Webinar@AIMS_FAIR Principles and Data Management Planning

Webinar@AIMS_FAIR Principles and Data Management PlanningAIMS (Agricultural Information Management Standards)
Recomendados
The FAIR principles have been introduced as a guideline for good scientific data stewardship. They have gained momentum at a management level and are now for example part of the project template for EU Horizon 2020 projects. This raises the question what research groups and projects can do to implement them. Hugo Besemer will introduce the ideas behind the FAIR principles.Webinar@AIMS_FAIR Principles and Data Management Planning

Webinar@AIMS_FAIR Principles and Data Management PlanningAIMS (Agricultural Information Management Standards)
Presentation of the article at Workshop of Learning Analytics & Knowledge 2016 in April 25, 2016.
Note: full paper is available on http://www.laceproject.eu/wp-content/uploads/2015/12/ep4la2016_paper_4.pdfMapping a Privacy Framework to a Reference Model of Learning Analytics

Mapping a Privacy Framework to a Reference Model of Learning AnalyticsOpen Cyber University of Korea
Mais conteúdo relacionado
Mais procurados
Presentation of the article at Workshop of Learning Analytics & Knowledge 2016 in April 25, 2016.
Note: full paper is available on http://www.laceproject.eu/wp-content/uploads/2015/12/ep4la2016_paper_4.pdfMapping a Privacy Framework to a Reference Model of Learning Analytics

Mapping a Privacy Framework to a Reference Model of Learning AnalyticsOpen Cyber University of Korea
Mais procurados (20)
[AIIM17] Data Categorization You Can Live With - Monica Crocker ![[AIIM17] Data Categorization You Can Live With - Monica Crocker](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[AIIM17] Data Categorization You Can Live With - Monica Crocker](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[AIIM17] Data Categorization You Can Live With - Monica Crocker
Data Mining: Application and trends in data mining

Data Mining: Application and trends in data mining
Making Data FAIR (Findable, Accessible, Interoperable, Reusable)

Making Data FAIR (Findable, Accessible, Interoperable, Reusable)
Ben Analytics Introduction to Predictive Analytics

Ben Analytics Introduction to Predictive Analytics
Efficient instant fuzzy search with proximity ranking

Efficient instant fuzzy search with proximity ranking
Mapping a Privacy Framework to a Reference Model of Learning Analytics

Mapping a Privacy Framework to a Reference Model of Learning Analytics
Data Mining with big data total ieee project and entire files.

Data Mining with big data total ieee project and entire files.
Semelhante a Ict journal layout
Semelhante a Ict journal layout (20)
Exercise 3You work as a forensic investigator. A recent inquiry .docx

Exercise 3You work as a forensic investigator. A recent inquiry .docx
INTRODUCTIONOne of the most critical factors in customer relat.docx

INTRODUCTIONOne of the most critical factors in customer relat.docx
Term Paper The Rookie Chief Information Security Officer.docx

Term Paper The Rookie Chief Information Security Officer.docx
Research Ethics and Integrity | Ethical Standards | Data Mining | Mixed Metho...

Research Ethics and Integrity | Ethical Standards | Data Mining | Mixed Metho...
Assignment 4 Data-Hiding TechniquesDue Week 8 and worth 100 p.docx

Assignment 4 Data-Hiding TechniquesDue Week 8 and worth 100 p.docx
Ethical dilemma Identity TheftStakeholdersConfidentiality.docx

Ethical dilemma Identity TheftStakeholdersConfidentiality.docx
Technical Documentation 101 for Data Engineers.pdf

Technical Documentation 101 for Data Engineers.pdf
Practical and Actionable Threat Intelligence Collection

Practical and Actionable Threat Intelligence Collection
Unit_8_Data_processing,_analysis_and_presentation_and_Application (1).pptx

Unit_8_Data_processing,_analysis_and_presentation_and_Application (1).pptx
Challenges in implementing effective data security practices

Challenges in implementing effective data security practices
1. Discussion (Chapter 3) Why are the originalraw data not readily.docx

1. Discussion (Chapter 3) Why are the originalraw data not readily.docx
The GDPR Most Wanted: The Marketer and Analyst's Role in Compliance

The GDPR Most Wanted: The Marketer and Analyst's Role in Compliance
Bowling Green State University Digital Forensics Challenges Project.docx

Bowling Green State University Digital Forensics Challenges Project.docx
Responses needed, a paragraph per bullet question (7-8 sentences).docx

Responses needed, a paragraph per bullet question (7-8 sentences).docx
Mais de FifeCollege
Mais de FifeCollege (13)
Fife College, French Toast Mafia, Apps for Good Presentation

Fife College, French Toast Mafia, Apps for Good Presentation
Fife College - The Cats Meow - Apps for Good presentation 

Fife College - The Cats Meow - Apps for Good presentation
Ict journal layout
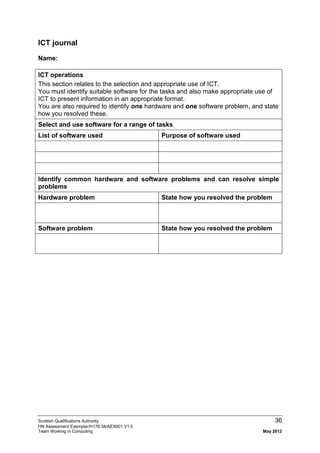
- 1. Scottish Qualifications Authority 36 HN Assessment Exemplar/H178 34/AEX001 V1.0 Team Working in Computing May 2012 ICT journal Name: ICT operations This section relates to the selection and appropriate use of ICT. You must identify suitable software for the tasks and also make appropriate use of ICT to present information in an appropriate format. You are also required to identify one hardware and one software problem, and state how you resolved these. Select and use software for a range of tasks List of software used Purpose of software used Identify common hardware and software problems and can resolve simple problems Hardware problem State how you resolved the problem Software problem State how you resolved the problem
- 2. Scottish Qualifications Authority 37 HN Assessment Exemplar/H178 34/AEX001 V1.0 Team Working in Computing May 2012 Name: Accessing information using ICT You are required to carry out searching for and locating information in different formats. You will apply complex search strategies and carry out evaluation of information found and the effectiveness of the search strategy. Define search topic and complex search strategy What topic are you searching for information on? You are required to search in at least three locations. Provide details of the sources, eg Internet, CD-ROM, intranet, own computer. Source 1 Source 2 Source 3 Provide an outline of the search strategy that you will use to search for information. Include choice of sources, keywords, order and logic. How will you evaluate the information? Identify the criteria used, eg how up-to- date is the information, is the information at a level you understand, is it reliable, biased, relevant and in an appropriate format? How well did your search strategy meet the criteria? Did it produce information that matched the chosen criteria, was it effective in terms of time and cost, did it successfully filter out irrelevant information? Keeping information safe How will you ensure that your data is secure and well managed?(eg keeping own login and password secure, virus protection, backing up data, maintaining personal file area) Provide details of how you ensured that your data was secure. Provide details of how you maintained/organised your own personal file area.