Blind spots in the network.pdf
•
0 gostou•15 visualizações
Primary Network Problems
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันที่ 24 กุมภาพันธ์ 2554Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...

Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...Software Park Thailand
Mais conteúdo relacionado
Mais procurados
Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันที่ 24 กุมภาพันธ์ 2554Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...

Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...Software Park Thailand
Mais procurados (20)
Navigating the Zero Trust Journey for Today's Everywhere Workplace

Navigating the Zero Trust Journey for Today's Everywhere Workplace
Corero Protects Its Customers From 'Apache Killer' DoS Exploit

Corero Protects Its Customers From 'Apache Killer' DoS Exploit
Security as a Service with Microsoft Presented by Razor Technology

Security as a Service with Microsoft Presented by Razor Technology
Devil's Bargain: Sacrificing Strategic Investments to Fund Today's Problems

Devil's Bargain: Sacrificing Strategic Investments to Fund Today's Problems
Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...

Presentation : CIO challenges by AJ.Prinya ในงานสัมมนาผู้บริหารไอที เมื่อวันท...
Semelhante a Blind spots in the network.pdf
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation initiative. Started in June 2012; they work on the space of BYOD security; Their sweet spot is 100% Agentless device discovery, fingerprinting and health-check and then denying infected/malicious devices from connecting to corporate network.i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...

i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...ProductNation/iSPIRT
Semelhante a Blind spots in the network.pdf (20)
2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...

2016 Top 10 Critical Infrastructures and SCADA/ICS Cyber Security Vulnerabili...
12 IoT Cyber Security Threats to Avoid - CyberHive.pdf

12 IoT Cyber Security Threats to Avoid - CyberHive.pdf
How Organizations can Secure Their Database From External Attacks

How Organizations can Secure Their Database From External Attacks
Rublon Multi-Factor Authentication (MFA) - Product Presentation

Rublon Multi-Factor Authentication (MFA) - Product Presentation
i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...

i7 Networks - Presentation at Zensar #TechShowcase - An iSPIRT ProductNation ...
Reveelium Smart Predictive Analytics - Datasheet EN

Reveelium Smart Predictive Analytics - Datasheet EN
3.8 Ways to Establish Secure Protocols in a Digital Organization.pdf

3.8 Ways to Establish Secure Protocols in a Digital Organization.pdf
Último
Call Girl Pune Indira Call Now: 8250077686 Pune Escorts Booking Contact Details WhatsApp Chat: +91-8250077686 Pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertainin. Plus they look fabulously elegant; making an impressionable. Independent Escorts Pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7

(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7Call Girls in Nagpur High Profile Call Girls
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai

Russian Call Girls in %(+971524965298 )# Call Girls in DubaiDubai call girls 971524965298 Call girls in Bur Dubai
Dwarka Sector 26 Call Girls | Delhi | 9999965857 🫦 Vanshika Verma More Our Service Click Here
Booking Contact Details :-
WhatsApp Chat :- [+91-9999965857 ]
The Best Call Girls Delhi At Your Service
Russian Call Girls Delhi Doing anything intimate with can be a wonderful way to unwind from life's stresses, while having some fun. These girls specialize in providing sexual pleasure that will satisfy your fetishes; from tease and seduce their clients to keeping it all confidential - these services are also available both install and outcall, making them great additions for parties or business events alike. Their expert sex skills include deep penetration, oral sex, cum eating and cum eating - always respecting your wishes as part of the experience
(29-April-2024(PSS)
Two shots with one girl: ₹4000/in-call, ₹7000/out-call
Body to body massage with : ₹4500/in-call
Full night for one person: ₹7000/in-call, ₹12000/out-call
Delhi Russian Escorts provide clients with the opportunity to experience an array of activities - everything from dining at upscale restaurants to watching the latest movies. Hotel call girls are available year-round to offer unforgettable experiences and fulfill all of your erotica desires. Escort services go beyond the traditional notion of call girls by providing clients with customized experiences beyond dinner companionship to social events. (29-April-2024(PSS)Dwarka Sector 26 Call Girls | Delhi | 9999965857 🫦 Vanshika Verma More Our Se...

Dwarka Sector 26 Call Girls | Delhi | 9999965857 🫦 Vanshika Verma More Our Se...Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶
Delhi Russian Escorts provide clients with the opportunity to experience an array of activities - everything from dining at upscale restaurants to watching the latest movies. Hotel call girls are available year-round to offer unforgettable experiences and fulfill all of your erotica desires. Escort services go beyond the traditional notion of call girls by providing clients with customized experiences beyond dinner companionship to social events. (27-April-2024(PSS)
Mahipalpur | Majnu Ka Tilla | Aerocity | Delhi,Noida | Gurgaon | Paharganj | GTB Nagar | Sarita Vihar | Chattarpur | Dwarka | Rajouri Garden | Connaught Place | Janakpuri
▂▃▄▅▆▇█▓▒░░▒▓█▇▆▅▄▃▂📢N-C-R⭐VIP⭐GENUINE🅰️█▬█⓿▀█▀💋 𝐆𝐈𝐑𝐋 💥ANAL SEX💥 BDSM💥69 POSE💥LIP KISS💥 DEEP SUCKING WITHOUT CONDOM💥 CUM ON FACE💥 NUDE DANCE💥 BOOBS RUBBING💥 LICKING💥HAND JOB 💏GIRLFRIEND EXPERIENCE💏 ❣️College girls, ❣️Russian girls, ❣️Working girls, ❣️North-east girls, ❣️ Punjabi girls, etc........................
EROTIC MASSAGE💥@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶

@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶Call Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance
Booking Contact Details :-
WhatsApp Chat :- [+91-9999965857 ]
The Best Call Girls Delhi At Your Service
Russian Call Girls Delhi Doing anything intimate with can be a wonderful way to unwind from life's stresses, while having some fun. These girls specialize in providing sexual pleasure that will satisfy your fetishes; from tease and seduce their clients to keeping it all confidential - these services are also available both install and outcall, making them great additions for parties or business events alike. Their expert sex skills include deep penetration, oral sex, cum eating and cum eating - always respecting your wishes as part of the experience
(27-April-2024(PSS)
Two shots with one girl: ₹4000/in-call, ₹7000/out-call
Body to body massage with : ₹4500/in-call
Full night for one person: ₹7000/in-call, ₹12000/out-call
Delhi Russian Escorts provide clients with the opportunity to experience an array of activities - everything from dining at upscale restaurants to watching the latest movies. Hotel call girls are available year-round to offer unforgettable experiences and fulfill all of your erotica desires. Escort services go beyond the traditional notion of call girls by providing clients with customized experiences beyond dinner companionship to social events. (27-April-2024(PSS)
Mahipalpur | Majnu Ka Tilla | Aerocity | Delhi,Noida | Gurgaon | Paharganj | GTB Nagar | Sarita Vihar | Chattarpur | Dwarka | Rajouri Garden | Connaught Place | Janakpuri
▂▃▄▅▆▇█▓▒░░▒▓█▇▆▅▄▃▂📢N-C-R⭐VIP⭐GENUINE🅰️█▬█⓿▀█▀💋 𝐆𝐈𝐑𝐋 💥ANAL SEX💥 BDSM💥69 POSE💥LIP KISS💥 DEEP SUCKING WITHOUT CONDOM💥 CUM ON FACE💥 NUDE DANCE💥 BOOBS RUBBING💥 LICKING💥HAND JOB 💏GIRLFRIEND EXPERIENCE💏 ❣️College girls, ❣️Russian girls, ❣️Working girls, ❣️North-east girls, ❣️ Punjabi girls, etc........................
EROTIC MASSAGE💥Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance

Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No AdvanceCall Girls In Delhi Whatsup 9873940964 Enjoy Unlimited Pleasure
Último (20)
On Starlink, presented by Geoff Huston at NZNOG 2024

On Starlink, presented by Geoff Huston at NZNOG 2024
(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7

(INDIRA) Call Girl Pune Call Now 8250077686 Pune Escorts 24x7
Russian Call Girls in %(+971524965298 )# Call Girls in Dubai

Russian Call Girls in %(+971524965298 )# Call Girls in Dubai
Dwarka Sector 26 Call Girls | Delhi | 9999965857 🫦 Vanshika Verma More Our Se...

Dwarka Sector 26 Call Girls | Delhi | 9999965857 🫦 Vanshika Verma More Our Se...
𓀤Call On 7877925207 𓀤 Ahmedguda Call Girls Hot Model With Sexy Bhabi Ready Fo...

𓀤Call On 7877925207 𓀤 Ahmedguda Call Girls Hot Model With Sexy Bhabi Ready Fo...
WhatsApp 📞 8448380779 ✅Call Girls In Mamura Sector 66 ( Noida)

WhatsApp 📞 8448380779 ✅Call Girls In Mamura Sector 66 ( Noida)
Call Now ☎ 8264348440 !! Call Girls in Shahpur Jat Escort Service Delhi N.C.R.

Call Now ☎ 8264348440 !! Call Girls in Shahpur Jat Escort Service Delhi N.C.R.
Pune Airport ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready...

Pune Airport ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready...
Call Now ☎ 8264348440 !! Call Girls in Green Park Escort Service Delhi N.C.R.

Call Now ☎ 8264348440 !! Call Girls in Green Park Escort Service Delhi N.C.R.
Lucknow ❤CALL GIRL 88759*99948 ❤CALL GIRLS IN Lucknow ESCORT SERVICE❤CALL GIRL

Lucknow ❤CALL GIRL 88759*99948 ❤CALL GIRLS IN Lucknow ESCORT SERVICE❤CALL GIRL
@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶

@9999965857 🫦 Sexy Desi Call Girls Laxmi Nagar 💓 High Profile Escorts Delhi 🫶
Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance

Rohini Sector 22 Call Girls Delhi 9999965857 @Sabina Saikh No Advance
All Time Service Available Call Girls Mg Road 👌 ⏭️ 6378878445

All Time Service Available Call Girls Mg Road 👌 ⏭️ 6378878445
Call Now ☎ 8264348440 !! Call Girls in Sarai Rohilla Escort Service Delhi N.C.R.

Call Now ☎ 8264348440 !! Call Girls in Sarai Rohilla Escort Service Delhi N.C.R.
Low Rate Young Call Girls in Sector 63 Mamura Noida ✔️☆9289244007✔️☆ Female E...

Low Rate Young Call Girls in Sector 63 Mamura Noida ✔️☆9289244007✔️☆ Female E...
(+971568250507 ))# Young Call Girls in Ajman By Pakistani Call Girls in ...

(+971568250507 ))# Young Call Girls in Ajman By Pakistani Call Girls in ...
Nanded City ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready ...

Nanded City ( Call Girls ) Pune 6297143586 Hot Model With Sexy Bhabi Ready ...
Call Girls In Ashram Chowk Delhi 💯Call Us 🔝8264348440🔝

Call Girls In Ashram Chowk Delhi 💯Call Us 🔝8264348440🔝
Call Girls Ludhiana Just Call 98765-12871 Top Class Call Girl Service Available

Call Girls Ludhiana Just Call 98765-12871 Top Class Call Girl Service Available
Enjoy Night⚡Call Girls Dlf City Phase 3 Gurgaon >༒8448380779 Escort Service

Enjoy Night⚡Call Girls Dlf City Phase 3 Gurgaon >༒8448380779 Escort Service
Blind spots in the network.pdf
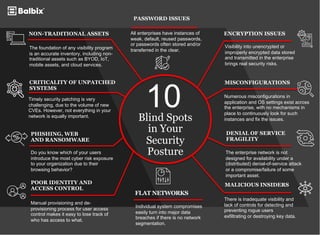
- 1. 10 Blind Spots in Your Security Posture NON-TRADITIONAL ASSETS The foundation of any visibility program is an accurate inventory, including non- traditional assets such as BYOD, IoT, mobile assets, and cloud services. PASSWORD ISSUES All enterprises have instances of weak, default, reused passwords, or passwords often stored and/or transferred in the clear. CRITICALITY OF UNPATCHED SYSTEMS Timely security patching is very challenging, due to the volume of new CVEs. However, not everything in your network is equally important. PHISHING, WEB AND RANSOMWARE Do you know which of your users introduce the most cyber risk exposure to your organization due to their browsing behavior? ENCRYPTION ISSUES Visibility into unencrypted or improperly encrypted data stored and transmitted in the enterprise brings real security risks. MISCONFIGURATIONS Numerous misconfigurations in application and OS settings exist across the enterprise, with no mechanisms in place to continuously look for such instances and fix the issues. DENIAL OF SERVICE FRAGILITY The enterprise network is not designed for availability under a (distributed) denial-of-service attack or a compromise/failure of some important asset. POOR IDENTITY AND ACCESS CONTROL Manual provisioning and de- provisioning process for user access control makes it easy to lose track of who has access to what. FLAT NETWORKS Individual system compromises easily turn into major data breaches if there is no network segmentation. MALICIOUS INSIDERS There is inadequate visibility and lack of controls for detecting and preventing rogue users exfiltrating or destroying key data.