2015 Annual Security Report Infographic
•
2 gostaram•12,501 visualizações
Download your copy of the Cisco Annual Security Report here >> http://cs.co/ASR15SS
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Destaque
Destaque (16)
Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...

Identify Zero-Day Breaches with Cognitive Threat Analytics on Cisco Web Secur...
Cisco ISE Reduces the Attack Surface by Controlling Access

Cisco ISE Reduces the Attack Surface by Controlling Access
Small Business Owner Report Infographic - Spring 2014 Bank of America

Small Business Owner Report Infographic - Spring 2014 Bank of America
Mais de Cisco Security
Mais de Cisco Security (15)
Incident Response Services Template - Cisco Security

Incident Response Services Template - Cisco Security
Infonetics Network and Content Security Vendor Scorecard

Infonetics Network and Content Security Vendor Scorecard
Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...

Gartner Newsletter: Cisco TrustSec Deployed Across Enterprise Campus, Branch ...
The Evolution of and Need for Secure Network Access

The Evolution of and Need for Secure Network Access
City of Tomorrow Builds in Next-Generation Security

City of Tomorrow Builds in Next-Generation Security
Laser Pioneer Secures Network End-to-End to Protect Assets

Laser Pioneer Secures Network End-to-End to Protect Assets
Leveraging Context-Aware Security to Safeguard Patient Data

Leveraging Context-Aware Security to Safeguard Patient Data
Último
Último (20)
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Boost Fertility New Invention Ups Success Rates.pdf

Boost Fertility New Invention Ups Success Rates.pdf
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
2015 Annual Security Report Infographic
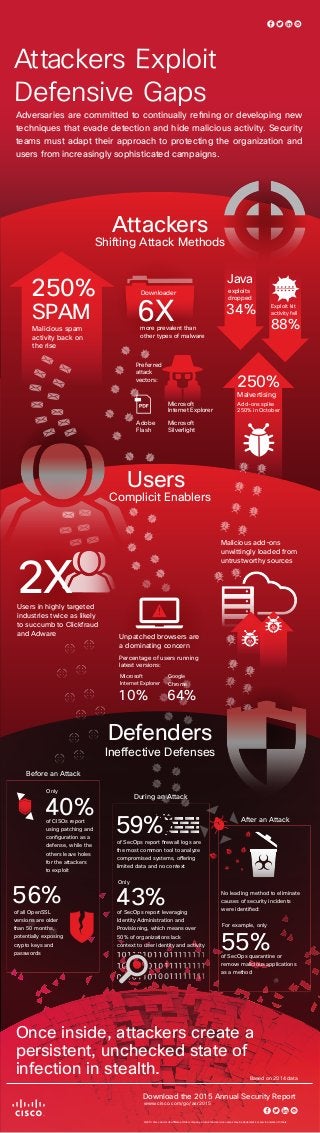
- 1. Ineffective Defenses 55%of SecOps quarantine or remove malicious applications as a method of CISOs report using patching and configuration as a defense, while the others leave holes for the attackers to exploit 40% of all OpenSSL versions are older than 50 months, potentially exposing crypto keys and passwords 56% of SecOps report firewall logs are the most common tool to analyze compromised systems, offering limited data and no context For example, only No leading method to eliminate causes of security incidents were identified: Download the 2015 Annual Security Report Before an Attack During an Attack 59% After an Attack Only of SecOps report leveraging Identity Administration and Provisioning, which means over 50% of organizations lack context to user identity and activity 43% Only Defenders Malicious add-ons unwittingly loaded from untrustworthy sources Users in highly targeted industries twice as likely to succumb to Clickfraud and Adware Users Complicit Enablers Unpatched browsers are a dominating concern Percentage of users running latest versions: 64% Google Chrome 10% Microsoft Internet Explorer 2X Exploit kit activity fell exploits dropped 34% 88% Preferred attack vectors: Attackers Shifting Attack Methods more prevalent than other types of malware Malvertising Add-ons spike 250% in October 250% Downloader 6XSPAM 250% Malicious spam activity back on the rise Java Microsoft Internet Explorer Microsoft Silverlight Adobe Flash ©2015 Cisco and or its affiliates. Other company, product and service names may be trademarks or service marks of others. Once inside, attackers create a persistent, unchecked state of infection in stealth. Attackers Exploit Defensive Gaps Adversaries are committed to continually refining or developing new techniques that evade detection and hide malicious activity. Security teams must adapt their approach to protecting the organization and users from increasingly sophisticated campaigns. Based on 2014 data www.cisco.com/go/asr2015
