Complete squid & firewall configuration. plus easy mac binding
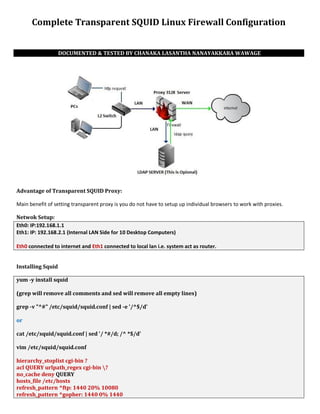
- 1. Complete Transparent SQUID Linux Firewall Configuration DOCUMENTED & TESTED BY CHANAKA LASANTHA NANAYAKKARA WAWAGE Advantage of Transparent SQUID Proxy: Main benefit of setting transparent proxy is you do not have to setup up individual browsers to work with proxies. Netwok Setup: Eth0: IP:192.168.1.1 Eth1: IP: 192.168.2.1 (Internal LAN Side for 10 Desktop Computers) Eth0 connected to internet and Eth1 connected to local lan i.e. system act as router. Installing Squid yum -y install squid (grep will remove all comments and sed will remove all empty lines) grep -v "^#" /etc/squid/squid.conf | sed -e '/^$/d' or cat /etc/squid/squid.conf | sed '/ *#/d; /^ *$/d' vim /etc/squid/squid.conf hierarchy_stoplist cgi-bin ? acl QUERY urlpath_regex cgi-bin ? no_cache deny QUERY hosts_file /etc/hosts refresh_pattern ^ftp: 1440 20% 10080 refresh_pattern ^gopher: 1440 0% 1440
- 2. refresh_pattern . 0 20% 4320 acl all src 0.0.0.0/0.0.0.0 acl manager proto cache_object acl localhost src 127.0.0.1/255.255.255.255 acl to_localhost dst 127.0.0.0/8 acl purge method PURGE acl CONNECT method CONNECT cache_mem 1024 MB http_access allow manager localhost http_access deny manager http_access allow purge localhost http_access deny purge http_access deny !Safe_ports http_access deny CONNECT !SSL_ports acl lan src 192.168.1.1 192.168.2.0/24 http_access allow localhost http_access allow lan http_access deny all http_reply_access allow all icp_access allow all visible_hostname chanaka.server httpd_accel_host virtual httpd_accel_port 80 httpd_accel_with_proxy on httpd_accel_uses_host_header on coredump_dir /var/spool/squid cache_dir ufs /usr/local/squid/var/cache/ 60000 16 256 squid –z /etc/rc.d/init.d/squid start chkconfig squid on 1. httpd_accel_host virtual: Squid as an httpd accelerator 2. httpd_accel_port 80: 80 is port you want to act as a proxy 3. httpd_accel_with_proxy on: Squid act as both a local httpd accelerator and as a proxy. 4. httpd_accel_uses_host_header on: Header is turned on which is the hostname from the URL. 5. acl lan src 192.168.1.1 192.168.2.0/24: Access control list, only allow LAN computers to use squid 6. http_access allow localhost: Squid access to LAN and localhost ACL only 7. http_access allow lan: Forwading IP Settings Vim /etc/sysctl.conf net.ipv4.ip_forward = 1 sysctl -p
- 3. IPTables Firewall Configurations service iptables start iptables -F iptables -X iptables -t nat -F iptables -t nat -X iptables -t mangle -F iptables -t mangle -X modprobe ip_conntrack modprobe ip_conntrack_ftp iptables -P INPUT DROP iptables -P OUTPUT ACCEPT iptables -A INPUT -i lo -j ACCEPT iptables -A OUTPUT -o lo -j ACCEPT iptables -A INPUT -i eth0 -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE iptables --append FORWARD --in-interface eth1 -j ACCEPT iptables -A INPUT -i eth1 -j ACCEPT iptables -A OUTPUT -o eth1 -j ACCEPT iptables -A INPUT -m state --state ESTABLISHED,RELATED -j ACCEPT iptables -A OUTPUT -m state --state NEW,ESTABLISHED,RELATED -j ACCEPT iptables -A INPUT -m state --state INVALID -j DROP iptables -A OUTPUT -m state --state INVALID -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL ALL -j DROP iptables -A INPUT -m state --state NEW -p tcp --tcp-flags ALL NONE -j DROP iptables -A INPUT -p tcp --tcp-flags ALL FIN,URG,PSH -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP iptables -A INPUT -p tcp --tcp-flags SYN,FIN SYN,FIN -j DROP iptables -N SYN_FLOOD iptables -A INPUT -p tcp --syn -j SYN_FLOOD iptables -A SYN_FLOOD -m limit --limit 2/s --limit-burst 6 -j RETURN iptables -A SYN_FLOOD -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type address-mask-request -j DROP iptables -A INPUT -p icmp -m icmp --icmp-type timestamp-request -j DROP iptables -A INPUT -p icmp -m icmp -m limit --limit 1/second -j ACCEPT iptables -A INPUT -p tcp -m tcp --tcp-flags RST RST -m limit --limit 2/second --limit-burst 2 -j ACCEPT iptables -A INPUT -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A FORWARD -m recent --name portscan --rcheck --seconds 86400 -j DROP iptables -A INPUT -m recent --name portscan --remove iptables -A FORWARD -m recent --name portscan –remove iptables -A INPUT -s 0.0.0.0/7 -j DROP iptables -A INPUT -s 2.0.0.0/8 -j DROP iptables -A INPUT -s 5.0.0.0/8 -j DROP iptables -A INPUT -s 7.0.0.0/8 -j DROP iptables -A INPUT -s 10.0.0.0/8 -j DROP iptables -A INPUT -s 23.0.0.0/8 -j DROP iptables -A INPUT -s 27.0.0.0/8 -j DROP
- 4. iptables -A INPUT -s 31.0.0.0/8 -j DROP iptables -A INPUT -s 36.0.0.0/7 -j DROP iptables -A INPUT -s 39.0.0.0/8 -j DROP iptables -A INPUT -s 42.0.0.0/8 -j DROP iptables -A INPUT -s 49.0.0.0/8 -j DROP iptables -A INPUT -s 50.0.0.0/8 -j DROP iptables -A INPUT -s 77.0.0.0/8 -j DROP iptables -A INPUT -s 78.0.0.0/7 -j DROP iptables -A INPUT -s 92.0.0.0/6 -j DROP iptables -A INPUT -s 96.0.0.0/4 -j DROP iptables -A INPUT -s 112.0.0.0/5 -j DROP iptables -A INPUT -s 120.0.0.0/8 -j DROP iptables -A INPUT -s 169.254.0.0/16 -j DROP iptables -A INPUT -s 172.16.0.0/12 -j DROP iptables -A INPUT -s 173.0.0.0/8 -j DROP iptables -A INPUT -s 174.0.0.0/7 -j DROP iptables -A INPUT -s 176.0.0.0/5 -j DROP iptables -A INPUT -s 184.0.0.0/6 -j DROP iptables -A INPUT -s 192.0.2.0/24 -j DROP iptables -A INPUT -s 197.0.0.0/8 -j DROP iptables -A INPUT -s 198.18.0.0/15 -j DROP iptables -A INPUT -s 223.0.0.0/8 -j DROP iptables -A INPUT -s 224.0.0.0/3 -j DROP iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 3310 -j ACCEPT iptables -A INPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 53 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 80 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 443 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 21 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 3306 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 3310 -j ACCEPT iptables -A OUTPUT -p tcp -m state --state NEW -m tcp --dport 1194 -j ACCEPT iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%27%27%3d%27” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+1%3d1” --algo bm -j DROP iptables -I FORWARD -s 0.0.0.0/0 -m string --string “%27+or+%271%27%3d%271” --algo bm -j DROP iptables -t nat -A PREROUTING -i eth1 -p tcp --dport 80 -j DNAT --to 192.168.1.1:3128 iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 3128 iptables -A INPUT -j LOG
- 5. iptables -A INPUT -j DROP Save & Execute service iptables save service iptables restart service network restart chkconfig iptables on Start or Restart the squid /etc/init.d/squid restart chkconfig squid on Testing tail -f /var/log/squid/access.log netstat –tuplen /sbin/iptables -L iptables -L -t nat –n iptables -vnL tcpdump Bind MAC with IP in SQUID MAC with IP to restrict users in your network to change their IP’s to bypass filtering. To ease the setup i will create small scripts to simplify our work. Here i will not describe how to config squid and how to run it. I assume you have already configure it. Grep MAC Addresses Let suppose we have 10 machines with IPs range 192.168.2.2 – 192.168.0.12, you have to get mac address for them using following command. Besure your machines are up and pingable, else you will get empty lines and you have to remove them manually. for i in `seq 2 12`; do ping -c 1 192.168.2.$i; arp -n 192.168.2.$i | grep -v Address | grep -v incomplete | awk ‘{print $1 ” “ $3}’ >> ip-mac.txt; done This command will get required mac address with IP in a file named ip-mac.txt cat ip-mac.txt 192.168.0.1 00:1D:09:6B:3C:28 192.168.0.2 00:1D:09:6A:EA:02 192.168.0.3 00:1D:09:71:2C:34 192.168.0.4 00:1D:09:6A:CB:85 192.168.0.5 00:1D:09:6A:C3:15 192.168.0.6 00:1D:09:6A:CA:8B
- 6. 192.168.0.7 00:1D:09:6A:CB:DA 192.168.0.8 00:1D:09:6A:CC:34 192.168.0.9 00:1D:09:6B:11:76 192.168.0.10 00:1D:09:6B:36:6F Create ACL For SQUID Bash script to easy to get acl for mac i=1 cat ip-mac.txt | while read a; do b=`echo $a | cut -f 2 -d ” “`; echo “acl mac$i arp $b” >> squid-mac-filter.txt; i=`expr $i + 1`; done cat squid-mac-filter.txt acl mac1 arp 00:1D:09:6B:3C:28 acl mac2 arp 00:1D:09:6A:EA:02 acl mac3 arp 00:1D:09:71:2C:34 acl mac4 arp 00:1D:09:6A:CB:85 acl mac5 arp 00:1D:09:6A:C3:15 acl mac6 arp 00:1D:09:6A:CA:8B acl mac7 arp 00:1D:09:6A:CB:DA acl mac8 arp 00:1D:09:6A:CC:34 acl mac9 arp 00:1D:09:6B:11:76 acl mac10 arp 00:1D:09:6B:36:6F To get acl for ip i=1 cat ip-mac.txt | while read a; do b=`echo $a | cut -f 1 -d ” “`; echo “acl ip$i src $b” >> squid-ip-filter.txt; i=`expr $i + 1`; done cat squid-ip-filter.txt acl ip1 src 192.168.0.1 acl ip2 src 192.168.0.2 acl ip3 src 192.168.0.3 acl ip4 src 192.168.0.4 acl ip5 src 192.168.0.5 acl ip6 src 192.168.0.6 acl ip7 src 192.168.0.7 acl ip8 src 192.168.0.8 acl ip9 src 192.168.0.9 acl ip10 src 192.168.0.10 To generate http_access allow lines, you have to get the max number of your list of IP’s and MAC’s. Here i have is 10. for i in `seq 1 10`; do echo “http_access allow mac$i ip$i” >> http-access-squid.txt; done cat http-access-squid.txt http_access allow mac1 ip1
- 7. http_access allow mac2 ip2 http_access allow mac3 ip3 http_access allow mac4 ip4 http_access allow mac5 ip5 http_access allow mac6 ip6 http_access allow mac7 ip7 http_access allow mac8 ip8 http_access allow mac9 ip9 http_access allow mac10 ip10 Now concatinate three files i.e squid-ip-filter.txt, squid-mac-filter.txt and http_access_squid.txt cat squid-mac-filter.txt squid-ip-filter.txt http-access-squid.txt >> acl-final.txt and copy from acl-final.txt to paste on appropriate location in squid.conf, dont forget to put http_access deny all on the last. NOTE: You have to copy paste the entire acl-final.txt file in squid.conf. Best is to paste at end of file. ඔබ නිපදලාගත් "acl-final.txt" ෆයිල් එකෙහි ඇතුත් සියල් "squid.conf" ෆයිල් එකෙහි අලසාන කෙොටකසහි කෙොපි කේස්ට් ෙරන්න ..! එය ලඩාත් සුදුසු ක්රමය් ලුයක ඔබට පසුල එය පහසුකලන් එඩිට් ෙර හැකි නිසාම යි . අමතර කදය් : DHCP Server එෙද කලනම ස්ථාපිත ෙර අලයන් පමක් එහි ීසස් ටයි් එෙ ස්ිරරල එකේ කෙනකුට කදන කස හදන්න ..! නමුත් .ඔබකේ ආයතනක කෙකනකු / ැේකටොේ භාවිතා ෙරන කෙකනකු ඉලත්ල ගියකහොත් එම එන්ටරි එෙ තිකබන නිසා ..පසුල DHCP Server එකෙන් එය ඉලත් ෙර අලුකතන් පැමිකකන කෙනාකේ " acl-final.txt" එකෙඉ නල පිටපතට අුයල රී-කෙොන්ෆිේ ෙ හැකි අබල මතෙ තබාගන්න .! Add Dag RPM Repository for yum wget http://dag.wieers.com/rpm/packages/RPM-GPG-KEY.dag.txt rpm --import RPM-GPG-KEY.dag.txt rm -f RPM-GPG-KEY.dag.txt vi /etc/yum.repos.d/dag.repo [dag] name=Dag RPM Repository for Red Hat Enterprise Linux baseurl=http://apt.sw.be/redhat/el5/en/$basearch/dag/ gpgcheck=1 enabled=0 Install Anti-Virus, Clamav yum --enablerepo=dag -y install clamav # install from DAG vi /etc/freshclam.conf # line 96: make it comment #NotifyClamd /etc/clamd.conf
- 8. freshclam # update policy file ClamAV update process started at Mon Apr 23 00:52:58 2007 main.cvd is up to date (version: 43, sigs: 104500, f-level: 14, builder: sven) Downloading daily-3147.cdiff [100%] Downloading daily-3147.cdiff [100%] daily.cvd updated (version: 3147, sigs: 6671, f-level: 15, builder: sven) Database updated (111171 signatures) from db.jp.clamav.net (IP: 61.205.61.201) # try to scan clamscan --infected --remove --recursive /home ----------- SCAN SUMMARY ----------- Known viruses: 111194 Engine version: 0.90.2 Scanned directories: 23 Scanned files: 33 Infected files: 0 Data scanned: 0.16 MB Time: 2.721 sec (0 m 2 s) # download trial virus wget http://www.eicar.org/download/eicar.com Resolving www.eicar.org... 88.198.38.136 Connecting to www.eicar.org|88.198.38.136|:80... connected. HTTP request sent, awaiting response... 200 OK Length: 68 [application/x-msdos-program] Saving to: `eicar.com' 100%[=======================================>] 68 --.-K/s in 0s 19:26:23 (5.90 MB/s) - `eicar.com' saved [68/68] # try to scan clamscan --infected --remove --recursive . ./eicar.com: Eicar-Test-Signature FOUND ./eicar.com: Removed# just removed ----------- SCAN SUMMARY ----------- Known viruses: 111194 Engine version: 0.90.2 Scanned directories: 5 Scanned files: 12 Infected files: 1 Data scanned: 0.02 MB Time: 2.599 sec (0 m 2 s)
- 9. Configure Proxy server in order to scan download files to protect from virus. Install Clamd yum --enablerepo=dag -y install clamd # install from DAG /etc/rc.d/init.d/clamd start Starting Clam AntiVirus Daemon: Bytecode: Security mode set to "TrustSigned". [ OK ] chkconfig clamd on Install squidclamav Download squidclamav 5.x from the link below. 6.x needs Squid 3.x, so use 5.x. http://sourceforge.net/projects/squidclamav/files/squidclamav/ yum -y install curl-devel wget http://ftp.jaist.ac.jp/pub/sourceforge/s/project/sq/squidclamav/squidclamav/5.7/squidclamav- 5.7.tar.gz tar zxvf squidclamav-5.7.tar.gz cd squidclamav-5.7 ./configure make make install cd vi /usr/local/etc/squidclamav.conf squid_ip 127.0.0.1 squid_port 3128 logfile /var/log/squid/squidclamav.log maxsize 5000000 # change ( reditected URL ) redirect http://192.168.2.1/error.html #squidguard /usr/local/squidGuard/bin/squidGuard debug 0 stat 0 maxredir 30 # change ( same with clamd's one ) clamd_local /var/run/clamav/clamd.sock # uncomment and change clamd_ip 127.0.0.1 # uncomment
- 10. clamd_port 3310 timeout 60 Configure Squid vi /etc/squid/squid.conf # add at the bottom url_rewrite_access deny localhost redirect_program /usr/local/bin/squidclamav redirect_children 15 touch /var/log/squid/squidclamav.log chown squid. /var/log/squid/squidclamav.log vi /etc/logrotate.d/squid # add at the bottom /var/log/squid/squidclamav.log { weekly rotate 5 copytruncate compress notifempty missingok } /etc/rc.d/init.d/squid restart Stopping squid: ................[ OK ] Starting squid: .[ OK ]
