Is your enterprise ready for WYOD?
•
0 gostou•952 visualizações
Is your enterprise ready for WYOD? Wearable devices are marching into the Enterprise, creating security concerns for IT. This infographic highlights the growing importance of considering the mobile information security of wearable devices.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Security from sensor to sunset. “How to approach the security in the IoT ecos...

Security from sensor to sunset. “How to approach the security in the IoT ecos...Data Driven Innovation
Mais conteúdo relacionado
Mais procurados
Security from sensor to sunset. “How to approach the security in the IoT ecos...

Security from sensor to sunset. “How to approach the security in the IoT ecos...Data Driven Innovation
Mais procurados (20)
Mobile security mobile malware countermeasure academic csirt

Mobile security mobile malware countermeasure academic csirt
I.G.N. Mantra - Mobile Security, Mobile Malware,and Countermeasure

I.G.N. Mantra - Mobile Security, Mobile Malware,and Countermeasure
Lookout Mobile Endpoint Security Datasheet (US - v2.5)

Lookout Mobile Endpoint Security Datasheet (US - v2.5)
Security from sensor to sunset. “How to approach the security in the IoT ecos...

Security from sensor to sunset. “How to approach the security in the IoT ecos...
GWAVACon 2015: GWAVAC - The Case for Mobile Archiving

GWAVACon 2015: GWAVAC - The Case for Mobile Archiving
Semelhante a Is your enterprise ready for WYOD?
Semelhante a Is your enterprise ready for WYOD? (20)
kaspersky presentation for palette business solution June 2016 v1.0.

kaspersky presentation for palette business solution June 2016 v1.0.
Mbs t17 o'neil-mbs-t17 rsa-realizing-mobile-enterprise

Mbs t17 o'neil-mbs-t17 rsa-realizing-mobile-enterprise
Mobile World Congress 2015: What we learned at MWC and what brands have to kn...

Mobile World Congress 2015: What we learned at MWC and what brands have to kn...
Infographic: Cloud Security & SMBs - What You Need to Know in 2015

Infographic: Cloud Security & SMBs - What You Need to Know in 2015
Preparing for the Future of Enterprise Mobility -- Insights Not to Miss

Preparing for the Future of Enterprise Mobility -- Insights Not to Miss
How to ensure data security in a hybrid workplace?

How to ensure data security in a hybrid workplace?
Mais de Proofpoint
Mais de Proofpoint (20)
Law Firms: Making the Case for Secure Mobile Productivity

Law Firms: Making the Case for Secure Mobile Productivity
The London Borough of Camden- Making BYOD a Secure Reality

The London Borough of Camden- Making BYOD a Secure Reality
Accellion Infographic: The Effects of Mobile on the Enterprise

Accellion Infographic: The Effects of Mobile on the Enterprise
(ISC)2 Secure Seattle 2013: Enable Secure and Mobile Cloud Collaboration

(ISC)2 Secure Seattle 2013: Enable Secure and Mobile Cloud Collaboration
Do you Know Where Your Data Is? - Accellion InfoSec World 2013 Conference pre...

Do you Know Where Your Data Is? - Accellion InfoSec World 2013 Conference pre...
Executive Alliance Dallas - Accellion Presentation

Executive Alliance Dallas - Accellion Presentation
Mind the gap: Navigating the Security Challenges of BYOD

Mind the gap: Navigating the Security Challenges of BYOD
Último
Último (20)
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
Nell’iperspazio con Rocket: il Framework Web di Rust!

Nell’iperspazio con Rocket: il Framework Web di Rust!
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
"Subclassing and Composition – A Pythonic Tour of Trade-Offs", Hynek Schlawack

"Subclassing and Composition – A Pythonic Tour of Trade-Offs", Hynek Schlawack
Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost

Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
Designing IA for AI - Information Architecture Conference 2024

Designing IA for AI - Information Architecture Conference 2024
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Vector Databases 101 - An introduction to the world of Vector Databases

Vector Databases 101 - An introduction to the world of Vector Databases
Powerpoint exploring the locations used in television show Time Clash

Powerpoint exploring the locations used in television show Time Clash
What's New in Teams Calling, Meetings and Devices March 2024

What's New in Teams Calling, Meetings and Devices March 2024
Is your enterprise ready for WYOD?
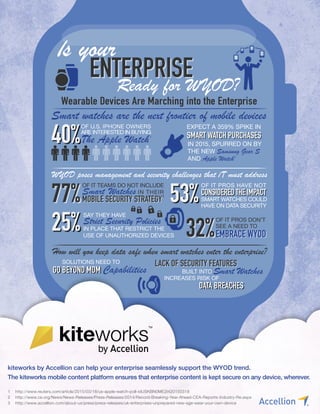
- 1. How will you keep data safe when smart watches enter the enterprise? SOLUTIONS NEED TO GO BEYOND MDMGO BEYOND MDM Capabilities LACK OF SECURITY FEATURESLACK OF SECURITY FEATURES BUILT INTO Smart Watches INCREASES RISK OF DATA BREACHESDATA BREACHES Smart watches are the next frontier of mobile devices WYOD poses management and security challenges that ⅠΤ must address OF U.S. IPHONE OWNERS ARE INTERESTED IN BUYING Τhe Apple Watch1 40%40% EXPECT A 359% SPIKE IN IN 2015, SPURRED ON BY THE NEW Samsung Gear S AND Apple Watch2 SMART WATCH PURCHASESSMART WATCH PURCHASES OF IT TEAMS DO NOT INCLUDE Smart Watches IN THEIR MOBILE SECURITY STRATEGYMOBILE SECURITY STRATEGY 3 OF IT PROS HAVE NOT SMART WATCHES COULD HAVE ON DATA SECURITY CONSIDEREDTHEIMPACTCONSIDEREDTHEIMPACT SAY THEY HAVE Strict Security Policies IN PLACE THAT RESTRICT THE USE OF UNAUTHORIZED DEVICES 77%77% 25%25% OF IT PROS DON’T SEE A NEED TO EMBRACE WYODEMBRACE WYOD32%32% 53%53% kiteworks by Accellion can help your enterprise seamlessly support the WYOD trend. The kiteworks mobile content platform ensures that enterprise content is kept secure on any device, wherever. 1 http://www.reuters.com/article/2015/03/18/us-apple-watch-poll-idUSKBN0ME2I420150318 2 http://www.ce.org/News/News-Releases/Press-Releases/2014/Record-Breaking-Year-Ahead-CEA-Reports-Industry-Re.aspx 3 http://www.accellion.com/about-us/press/press-releases/uk-enterprises-unprepared-new-age-wear-your-own-device ENTERPRISEENTERPRISE Ⅰs your Ready for WYOD? W Y O D Wearable Devices Are Marching into the Enterprise
