Bypassing cisco’s sourcefire amp endpoint solution – full demo
•Transferir como DOCX, PDF•
1 gostou•757 visualizações
Bypassing cisco’s sourcefire amp endpoint solution
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Web Application Firewall - Friend of your DevOps Pipeline?

Web Application Firewall - Friend of your DevOps Pipeline?
XSS - Presented at EPiServer Meetup in Oslo 25th May 2011

XSS - Presented at EPiServer Meetup in Oslo 25th May 2011
Automated Penetration Testing With The Metasploit Framework

Automated Penetration Testing With The Metasploit Framework
PuppetCamp Amsterdam 2013 - Automated OS and App deployment using Puppet and ...

PuppetCamp Amsterdam 2013 - Automated OS and App deployment using Puppet and ...
Destaque
DeterminingWhichZincCompoundWillResultinLargestBrassYieldWhenUsedtoPlateCoppe...

DeterminingWhichZincCompoundWillResultinLargestBrassYieldWhenUsedtoPlateCoppe...Alexander Kaunzinger
Destaque (13)
Guida / Tutorial: Come aprire il tuo e-commerce su stylenda.com

Guida / Tutorial: Come aprire il tuo e-commerce su stylenda.com
DeterminingWhichZincCompoundWillResultinLargestBrassYieldWhenUsedtoPlateCoppe...

DeterminingWhichZincCompoundWillResultinLargestBrassYieldWhenUsedtoPlateCoppe...
Leftventricularassistdevice 150525194214-lva1-app6891

Leftventricularassistdevice 150525194214-lva1-app6891
Semelhante a Bypassing cisco’s sourcefire amp endpoint solution – full demo
Semelhante a Bypassing cisco’s sourcefire amp endpoint solution – full demo (20)
DEF CON 27 - workshop ANTHONY ROSE - introduction to amsi bypasses and sandbo...

DEF CON 27 - workshop ANTHONY ROSE - introduction to amsi bypasses and sandbo...
Presentatie McAfee: Optimale Endpoint Protection 26062015

Presentatie McAfee: Optimale Endpoint Protection 26062015
Web application penetration testing lab setup guide

Web application penetration testing lab setup guide
The Seven Most Dangerous New Attack Techniques, and What's Coming Next

The Seven Most Dangerous New Attack Techniques, and What's Coming Next
The Seven Most Dangerous New Attack Techniques, and What's Coming Next

The Seven Most Dangerous New Attack Techniques, and What's Coming Next
8 Ocak 2015 SOME Etkinligi - Cisco Next Generation Security

8 Ocak 2015 SOME Etkinligi - Cisco Next Generation Security
Último
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in Tembisa ● Abortion Pills For Sale in Tembisa ● Tembisa 🏥🚑!! Abortion Clinic Near Me Cost, Price, Women's Clinic Near Me, Abortion Clinic Near, Abortion Doctors Near me, Abortion Services Near Me, Abortion Pills Over The Counter, Abortion Pill Doctors' Offices, Abortion Clinics, Abortion Places Near Me, Cheap Abortion Places Near Me, Medical Abortion & Surgical Abortion, approved cyctotec pills and womb cleaning pills too plus all the instructions needed This Discrete women’s Termination Clinic offers same day services that are safe and pain free, we use approved pills and we clean the womb so that no side effects are present. Our main goal is that of preventing unintended pregnancies and unwanted births every day to enable more women to have children by choice, not chance. We offer Terminations by Pill and The Morning After Pill.” Our Private VIP Abortion Service offers the ultimate in privacy, efficiency and discretion. we do safe and same day termination and we do also womb cleaning as well its done from 1 week up to 28 weeks. We do delivery of our services world wide SAFE ABORTION CLINICS/PILLS ON SALE WE DO DELIVERY OF PILLS ALSO Abortion clinic at very low costs, 100% Guaranteed and it’s safe, pain free and a same day service. It Is A 45 Minutes Procedure, we use tested abortion pills and we do womb cleaning as well. Alternatively the medical abortion pill and womb cleansing !!!Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...Medical / Health Care (+971588192166) Mifepristone and Misoprostol tablets 200mg
Último (20)
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Abortion Pill Prices Tembisa [(+27832195400*)] 🏥 Women's Abortion Clinic in T...
What Goes Wrong with Language Definitions and How to Improve the Situation

What Goes Wrong with Language Definitions and How to Improve the Situation
Love witchcraft +27768521739 Binding love spell in Sandy Springs, GA |psychic...

Love witchcraft +27768521739 Binding love spell in Sandy Springs, GA |psychic...
%in kaalfontein+277-882-255-28 abortion pills for sale in kaalfontein

%in kaalfontein+277-882-255-28 abortion pills for sale in kaalfontein
%in tembisa+277-882-255-28 abortion pills for sale in tembisa

%in tembisa+277-882-255-28 abortion pills for sale in tembisa
%+27788225528 love spells in Colorado Springs Psychic Readings, Attraction sp...

%+27788225528 love spells in Colorado Springs Psychic Readings, Attraction sp...
Devoxx UK 2024 - Going serverless with Quarkus, GraalVM native images and AWS...

Devoxx UK 2024 - Going serverless with Quarkus, GraalVM native images and AWS...
%in Soweto+277-882-255-28 abortion pills for sale in soweto

%in Soweto+277-882-255-28 abortion pills for sale in soweto
%in Rustenburg+277-882-255-28 abortion pills for sale in Rustenburg

%in Rustenburg+277-882-255-28 abortion pills for sale in Rustenburg
W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...

W01_panagenda_Navigating-the-Future-with-The-Hitchhikers-Guide-to-Notes-and-D...
%+27788225528 love spells in Knoxville Psychic Readings, Attraction spells,Br...

%+27788225528 love spells in Knoxville Psychic Readings, Attraction spells,Br...
%in Harare+277-882-255-28 abortion pills for sale in Harare

%in Harare+277-882-255-28 abortion pills for sale in Harare
%in Midrand+277-882-255-28 abortion pills for sale in midrand

%in Midrand+277-882-255-28 abortion pills for sale in midrand
%in kempton park+277-882-255-28 abortion pills for sale in kempton park 

%in kempton park+277-882-255-28 abortion pills for sale in kempton park
%in tembisa+277-882-255-28 abortion pills for sale in tembisa

%in tembisa+277-882-255-28 abortion pills for sale in tembisa
8257 interfacing 2 in microprocessor for btech students

8257 interfacing 2 in microprocessor for btech students
WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation

WSO2Con2024 - WSO2's IAM Vision: Identity-Led Digital Transformation
Bypassing cisco’s sourcefire amp endpoint solution – full demo
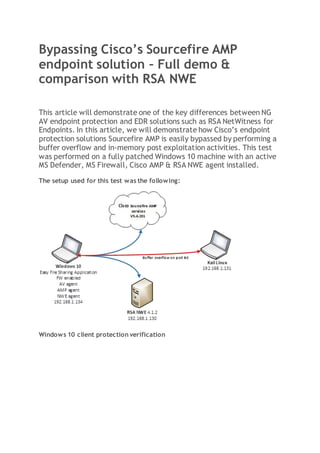
- 1. Bypassing Cisco’s Sourcefire AMP endpoint solution – Full demo & comparison with RSA NWE This article will demonstrate one of the key differences between NG AV endpoint protection and EDR solutions such as RSA NetWitness for Endpoints. In this article, we will demonstrate how Cisco’s endpoint protection solutions Sourcefire AMP is easily bypassed by performing a buffer overflow and in-memory post exploitation activities. This test was performed on a fully patched Windows 10 machine with an active MS Defender, MS Firewall, Cisco AMP & RSA NWE agent installed. The setup used for this test was the following: Windows 10 client protection verification
- 2. Vulnerable application is installed and running Cisco SourceFire AMP does not find any issues on the clean machine
- 3. AMP tracking information does not highlight any suspicious activities RSA NWE does not find any suspicious activities on the clean machine
- 4. Attacker – KALI setting up exploit & payload module
- 5. Running remote buffer overflow exploit No alerting from either Cisco AMP or MS Defender…
- 6. Attacker runs additional post exploitation activities such as a keylogger Attacker searches and downloads password.txt & creates a screenshot
- 7. Attacker performs a ARP network scan Attacker start an interactive SHELL and runs WHOAMI & IPCONFIG commands
- 8. Still no alerting from either Cisco AMP or MS Defender… Cisco AMP does not detect or notifies on exploit and post exploit activities….
- 9. Now let’s look at RSA NWE
