World of Mobile Threats: UK
•
1 gostou•2,607 visualizações
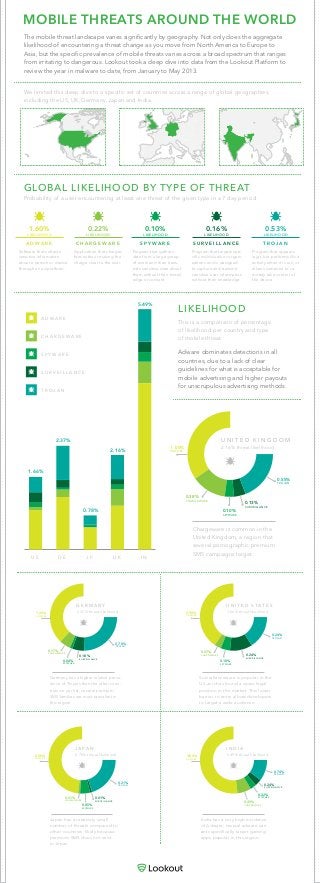
The mobile threat landscape varies significantly by geography. Not only does the aggregate likelihood of encountering a threat change as you move from North America to Europe to Asia, but the specific prevalence of mobile threats varies across a broad spectrum that ranges from irritating to dangerous. Lookout took a deep dive into data from the Lookout Platform to review the year in malware to date, from January to May 2013.
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Mais de Lookout
Mais de Lookout (20)
Último
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Último (20)
WSO2's API Vision: Unifying Control, Empowering Developers

WSO2's API Vision: Unifying Control, Empowering Developers
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Introduction to Multilingual Retrieval Augmented Generation (RAG)

Introduction to Multilingual Retrieval Augmented Generation (RAG)
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf

Rising Above_ Dubai Floods and the Fortitude of Dubai International Airport.pdf
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...

Biography Of Angeliki Cooney | Senior Vice President Life Sciences | Albany, ...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
"I see eyes in my soup": How Delivery Hero implemented the safety system for ...

"I see eyes in my soup": How Delivery Hero implemented the safety system for ...
World of Mobile Threats: UK
- 1. MOBILE THREATS AROUND THE WORLD The mobile threat landscape varies significantly by geography. Not only does the aggregate likelihood of encountering a threat change as you move from North America to Europe to Asia, but the specific prevalence of mobile threats varies across a broad spectrum that ranges from irritating to dangerous. Lookout took a deep dive into data from the Lookout Platform to review the year in malware to date, from January to May 2013. Adware dominates detections in all countries, due to a lack of clear guidelines for what is acceptable for mobile advertising and higher payouts for unscrupulous advertising methods. A D W A R E C H A R G E W A R E S P Y W A R E S U R V E I L L A N C E T R O J A N U S 1.66% D E 2.37% J P 0.78% U K 2.16% I N 5.49% LIKELIHOOD Chargeware is common in the United Kingdom, a region that several pornographic premium SMS campaigns target. This is a comparison of percentage of likelihood per country and type of mobile threat. GLOBAL LIKELIHOOD BY TYPE OF THREAT Probability of a user encountering at least one threat of the given type in a 7 day period. We limited this deep dive to a specific set of countries across a range of global geographies, including the US, UK, Germany, Japan and India. Germany has a higher relative preva- lence of Trojans than the other coun- tries on our list; several premium SMS families are most prevalent in this region. Surveillanceware is popular in the US as it has found a quasi-legal position in the market. This lower barrier to entry allows developers to target a wide audience. Japan has a relatively small number of threats compared to other countries, likely because premium SMS does not exist in Japan. India has a very high incidence of Adware; several adware vari- ants specifically target gaming apps popular in this region. A D W A R E LIKELIHOOD 1.60% Software that collects sensitive information about a person or device through an ad platform. C H A R G E W A R E LIKELIHOOD 0.22% Application that charges fees without making the charge clear to the user. S P Y W A R E LIKELIHOOD 0.10% Program that gathers data from a large group of users and then trans- mits sensitive data about them without their knowl- edge or consent. S U R V E I L L A N C E LIKELIHOOD 0.16% Program that targets spe- cific individuals or organi- zations and is designed to capture and transmit sensitive user information without their knowledge. T R O J A N LIKELIHOOD 0.53% Program that appears legit, but performs illicit activity when it is run, or allows someone to re- motely take control of the device. 1.20% ADWARE 0.17% CHARGEWARE 0.18% SURVEILLANCE 0.78% TROJAN 0.04% SPYWARE G E R M A N Y 2.37% threat likelihood 0.50% ADWARE 0.01% CHARGEWARE 0.01% SURVEILLANCE 0.21% TROJAN 0.05% SPYWARE J A P A N 0.78% threat likelihood 3.80% ADWARE 0.49% CHARGEWARE 0.24% SURVEILLANCE 0.74% TROJAN 0.22% SPYWARE I N D I A 5.49% threat likelihood 1 .00% ADWARE 0.38% CHARGEWARE 0.13% SURVEILLANCE 0.55% TROJAN 0.10% SPYWARE U N I T E D K I N G D O M 2.16% threat likelihood 0.90% ADWARE 0.07% CHARGEWARE 0.24% SURVEILLANCE 0.24% TROJAN 0.10% SPYWARE U N I T E D S T A T E S 1.66% threat likelihood
