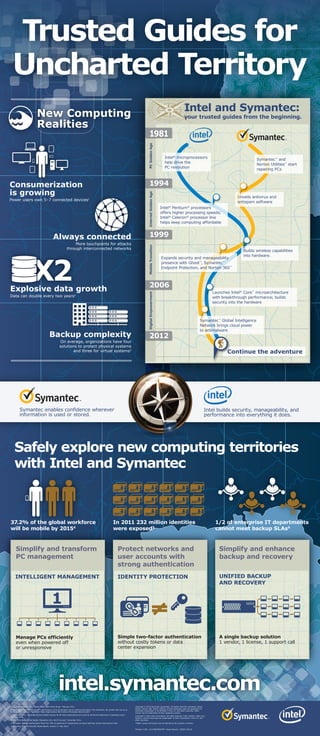
Intel Symantec Alliance Infographic
- 1. 1 Apple devices only. IDC, "Media Tablet Multi-Client Study." February 2011. 2 According to Gartner, the growth rate of data is 40 to 60 percent; but for unstructured data in the enterprise, the growth rate can be up to 80 percent. Cited by “Symantec Helps Organizations Get Control of Runaway Data Growth.” 3 Symantec Corp, "Symantec Declares Better Backup for All Sizes Organizations and Calls for 80 Percent Reduction in Operating Costs." February 2012. 4 IDC, "Worldwide Mobile Worker Population 2011-2015 Forecast." December 2011. 5 Symantec. Backup and Recovery Flash Poll. 49% of enterprise IT departments surveyed said they cannot meet backup SLAs 6 Symantec. Internet Security Threat Report, Volume 17. May 2012. Safely explore new computing territories with Intel and Symantec intel.symantec.com Copyright © 2012 Symantec Corporation. All rights reserved. Symantec, Ghost, Norton, Norton 360, Norton Utilities, and the Symantec logo are trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. Copyright © 2012 Intel Corporation. All rights reserved. Intel, Celeron, Intel Core, Pentium, and the Intel logo are trademarks of Intel Corporation in the U.S. and other countries. *Other names and brands may be claimed as the property of others. Printed in USA 1212/MS/PRW/PDF Please Recycle 328307-001US Simplify and transform PC management Protect networks and user accounts with strong authentication Intel builds security, manageability, and performance into everything it does. Symantec enables confidence wherever information is used or stored. PCGoldenAgeInternetGoldenAgeMobileTransitionDigitalEmpowerment Intel® microprocessors help drive the PC revolution Intel® Pentium® processors offers higher processing speeds; Intel® Celeron® processor line helps keep computing affordable Builds wireless capabilities into hardware. Launches Intel® Core™ microarchitecture with breakthrough performance; builds security into the hardware Expands security and manageability presence with Ghost™ , Symantec™ Endpoint Protection, and Norton 360™ Symantec™ and Norton Utilities™ start repairing PCs Unveils antivirus and antispam software Symantec™ Global Intelligence Network brings cloud power to antimalware 1994 1999 2006 2012 1981 Intel and Symantec: your trusted guides from the beginning. Consumerization is growing Power users own 5–7 connected devices1 Always connected More touchpoints for attacks through interconnected networks Explosive data growth Data can double every two years2 Backup complexity On average, organizations have four solutions to protect physical systems and three for virtual systems3 37.2% of the global workforce will be mobile by 20154 1/2 of enterprise IT departments cannot meet backup SLAs6 INTELLIGENT MANAGEMENT Manage PCs efficiently even when powered off or unresponsive Simple two-factor authentication without costly tokens or data center expansion IDENTITY PROTECTION A single backup solution 1 vendor, 1 license, 1 support call UNIFIED BACKUP AND RECOVERY In 2011 232 million identities were exposed5 Simplify and enhance backup and recovery Trusted Guides for Uncharted Territory Continue the adventure New Computing Realities
