Computer Apps 1 Slide Show
•Transferir como PPTX, PDF•
0 gostou•231 visualizações
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defender

Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defenderRemmy Nweke, mNGE, mNUJ, mGOCOP
Mais conteúdo relacionado
Mais procurados
Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defender

Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defenderRemmy Nweke, mNGE, mNUJ, mGOCOP
Mais procurados (20)
The latest development in network and communication

The latest development in network and communication
Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defender

Using a VPN or and TOR by remmy nweke, fellow, cyber security policy defender
Semelhante a Computer Apps 1 Slide Show
Semelhante a Computer Apps 1 Slide Show (20)
Último
Último (20)
TeamStation AI System Report LATAM IT Salaries 2024

TeamStation AI System Report LATAM IT Salaries 2024
Hyperautomation and AI/ML: A Strategy for Digital Transformation Success.pdf

Hyperautomation and AI/ML: A Strategy for Digital Transformation Success.pdf
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx

Merck Moving Beyond Passwords: FIDO Paris Seminar.pptx
New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
DSPy a system for AI to Write Prompts and Do Fine Tuning

DSPy a system for AI to Write Prompts and Do Fine Tuning
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024

New from BookNet Canada for 2024: Loan Stars - Tech Forum 2024
The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx

The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
Computer Apps 1 Slide Show
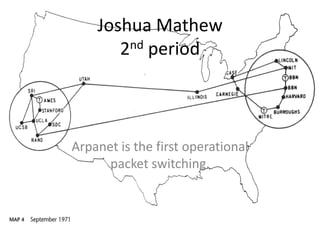
- 1. Joshua Mathew 2nd period Arpanet is the first operational packet switching.
- 2. Hard and Soft Bounce • The difference between them is that hard is undeliverable mail, and soft is when it gets as far as the recipient.
- 3. Computer Spam • It is junk mail, that usually advertises products.
- 4. Internet and Intranet • The difference between them is that intranet is a personal network, that uses internet.
- 5. POP • Is postal office protocol, this is a way to receive e-mail over TCP/IP connection.
- 6. Phishing • This is a security system that protects from identity theft.
- 7. Encryption and Decryption • Encryption is transferring information, decryption is the opposite.
- 8. Netiquette
- 9. Router • A router is a way for you to connect more than one computer to a network.
