Actionable IAM
•
0 likes•461 views
E
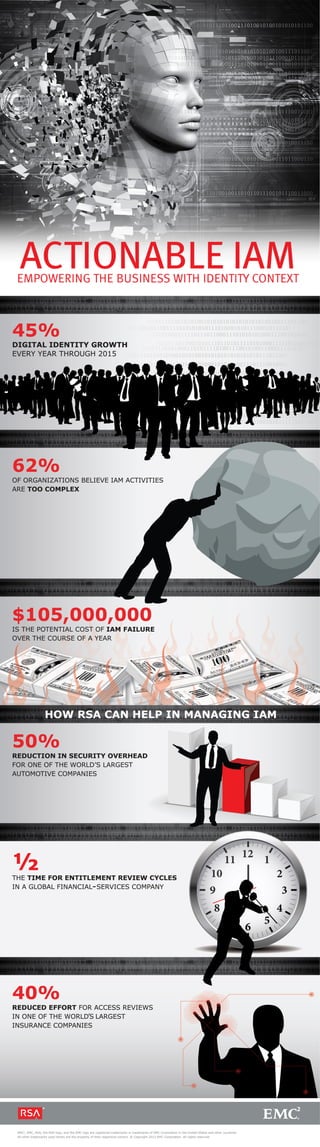
EMCThis infographic contains valuable industry statistics and guidance for determining and implementing an identity access management (IAM) strategy.
Report
Share
Report
Share
Download to read offline
Recommended
DATALOGIC Magellan 9800i - Multi-Plane Imaging Scanner and Scales

DATALOGIC Magellan 9800i - Multi-Plane Imaging Scanner and ScalesRadiant Global ADC Vietnam Co., Ltd.
Recommended
DATALOGIC Magellan 9800i - Multi-Plane Imaging Scanner and Scales

DATALOGIC Magellan 9800i - Multi-Plane Imaging Scanner and ScalesRadiant Global ADC Vietnam Co., Ltd.
More Related Content
Viewers also liked
Viewers also liked (20)
Windows 8 Client Part 1 "The OS internals for IT-Pro's"

Windows 8 Client Part 1 "The OS internals for IT-Pro's"
White Paper: EMC Security Design Principles for Multi-Tenant As-a-Service Env...

White Paper: EMC Security Design Principles for Multi-Tenant As-a-Service Env...
4 Ms of Big Data: Make Me More Money – Infographic

4 Ms of Big Data: Make Me More Money – Infographic
EMC Big Data | Hadoop Starter Kit | EMC Forum 2014

EMC Big Data | Hadoop Starter Kit | EMC Forum 2014
More from EMC
More from EMC (20)
INDUSTRY-LEADING TECHNOLOGY FOR LONG TERM RETENTION OF BACKUPS IN THE CLOUD

INDUSTRY-LEADING TECHNOLOGY FOR LONG TERM RETENTION OF BACKUPS IN THE CLOUD
Transforming Desktop Virtualization with Citrix XenDesktop and EMC XtremIO

Transforming Desktop Virtualization with Citrix XenDesktop and EMC XtremIO
EMC FORUM RESEARCH GLOBAL RESULTS - 10,451 RESPONSES ACROSS 33 COUNTRIES 

EMC FORUM RESEARCH GLOBAL RESULTS - 10,451 RESPONSES ACROSS 33 COUNTRIES
The Trust Paradox: Access Management and Trust in an Insecure Age

The Trust Paradox: Access Management and Trust in an Insecure Age
Data Science and Big Data Analytics Book from EMC Education Services

Data Science and Big Data Analytics Book from EMC Education Services
Using EMC Symmetrix Storage in VMware vSphere Environments

Using EMC Symmetrix Storage in VMware vSphere Environments