Nxll14 cut through-proxy on asa
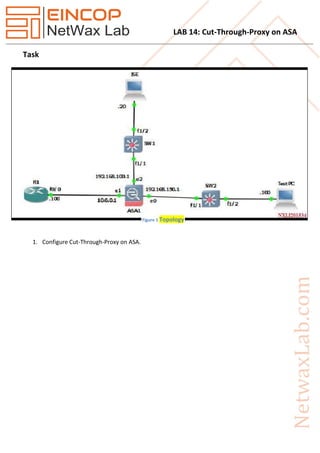
- 1. LAB 14: Cut-Through-Proxy on ASA Task 1. Configure Cut-Through-Proxy on ASA. Figure 1 Topology
- 2. LAB 14: Cut-Through-Proxy on ASA Solution R1 Int f0/0 Ip add 10.0.0.100 No shut Exit Ip route 0.0.0.0 0.0.0.0 10.0.0.1 ASA Int g0 Nameif outside Ip add 192.168.150.1 255.255.255.0 No shut Exit Int g1 Nameif inside Ip add 10.0.0.1 255.255.255.0 No shut Exit Int g2 Nameif dmz Ip add 192.168.100.1 255.255.255.0 No shut Exit Access-list OUT permit icmp any any Access-group OUT in interface outside Access-group OUT in interface dmz (Note: Ping R1 to ISE, R1 to TestPC successfully after above commands.)
- 3. LAB 14: Cut-Through-Proxy on ASA ISE configuration on ASA Aaa-server ISE protocol radius Exit Aaa-server ISE (dmz) host 192.168.100.20 Key cisco Exit Virtual telnet 172.16.1.100 access-list OUT extended permit tcp any host 172.16.1.100 eq telnet access-list CUT extended permit tcp any host 172.16.1.100 eq telnet aaa authentication match CUT dmz ISE access-group OUT in interface dmz per-user-override Verification 1. Telnet 10.0.0.100 from TestPC, It will show failed connection. 2. Telnet 172.16.1.100 from TestPC, It will show successfully connection. ISE Configuration Steps: 1. Login to authentication on TestPC using browser. Go to 1. Administrator > Network Resource > Network Device > Add. Add a Network Device use Name = ASA IP Address = 192.168.100.1/32 Location = All Location Device Type = All Device Types Authentication Settings: Protocol = RADIUS *Shared Secret = cisco Submit/Save 2. Administrator > Identity Management > Group > User Identity Group > Add Name = CTP Submit
- 4. LAB 14: Cut-Through-Proxy on ASA 3. Administrator > Identity Management > Identities > Users > Add Name = test Password = Cisco@123 Re-Enter Password = Cisco@123 User Groups = CTP Submit/Save After this go on Firewall and test your Configuration Ciscoasa# test aaa-server authentication ISE host 192.168.100.20 username test password Cisco@123 INFO: Attempting Authentication test to IP address <192.168.100.20> (timeout: 12 seconds) INFO: Authentication Successful Create Authorization Profile on ISE 1. Policy > Policy Elements > Results > Authorization > Authorization profile > Add. Name = CTP Access Type = ACCESS_ACCEPT Advanced Attributes Settings: Cisco:cisco-av-pair = ip:inacl#1=permit tcp any any eq 23 Save 2. Policy > Authorization Click on Edit and then, Click Insert Rules Below Then name rule as CTP and in ,if column call user from User Identity Group <CTP>, permission column call Authorization Profile created before which is to be found in Standard list <CTP>. Now initiate Telnet Connection from TestPC to Virtual IP 172.16.1.100 Username = test Password = Cisco@123 It will authenticate Successfully. Now Check the dynamic access-list on ASA. It will download after successfully connect with virtual ip. Now again Telnet from TestPC to R1 host. It will authenticate successfully and you will connect with R1. Necessary Commands 1. Sh uauth 2. Clear uauth
