Ten Tools for Security Professionals
•
2 likes•1,154 views
A short lecture that I gave to the Information and Computer Security class at Mississippi State University this semester
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
What's hot
What's hot (20)
Lab Meeting - 20140902 - Root Guard-Protecting Rooted Android Phones

Lab Meeting - 20140902 - Root Guard-Protecting Rooted Android Phones
Machine Learning for Malware Classification and Clustering

Machine Learning for Malware Classification and Clustering
Continuous security testing - sharing responsibility

Continuous security testing - sharing responsibility
Security evaluation of pattern classifiers under attack 

Security evaluation of pattern classifiers under attack
Building & Leveraging White Database for Antivirus Testing

Building & Leveraging White Database for Antivirus Testing
Security evaluation of pattern classifiers under attack

Security evaluation of pattern classifiers under attack
AlienVault Brute Force Attacks- Keeping the Bots at Bay with AlienVault USM +...

AlienVault Brute Force Attacks- Keeping the Bots at Bay with AlienVault USM +...
Engineering Security Vulnerability Prevention, Detection, and Response

Engineering Security Vulnerability Prevention, Detection, and Response
Assessment and Threats: Protecting Your Company from Cyber Attacks

Assessment and Threats: Protecting Your Company from Cyber Attacks
Similar to Ten Tools for Security Professionals
Similar to Ten Tools for Security Professionals (20)
Best Practices, Types, and Tools for Security Testing in 2023.docx

Best Practices, Types, and Tools for Security Testing in 2023.docx
IRJET- Penetration Testing using Metasploit Framework: An Ethical Approach

IRJET- Penetration Testing using Metasploit Framework: An Ethical Approach
A Comparison Study of Open Source Penetration Testing Tools

A Comparison Study of Open Source Penetration Testing Tools
Break it while you make it: writing (more) secure software

Break it while you make it: writing (more) secure software
What are DevSecOps Tools and Why Do You Need Them?

What are DevSecOps Tools and Why Do You Need Them?
Current Topics paper A4 submission 4.30.2015 Master Copy

Current Topics paper A4 submission 4.30.2015 Master Copy
The Basics of Hacking and Penetration Testing Tools

The Basics of Hacking and Penetration Testing Tools
Recently uploaded
Recently uploaded (20)
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
The Future of Software Development - Devin AI Innovative Approach.pdf

The Future of Software Development - Devin AI Innovative Approach.pdf
Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics

Kotlin Multiplatform & Compose Multiplatform - Starter kit for pragmatics
Ensuring Technical Readiness For Copilot in Microsoft 365

Ensuring Technical Readiness For Copilot in Microsoft 365
WordPress Websites for Engineers: Elevate Your Brand

WordPress Websites for Engineers: Elevate Your Brand
DevoxxFR 2024 Reproducible Builds with Apache Maven

DevoxxFR 2024 Reproducible Builds with Apache Maven
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
Developer Data Modeling Mistakes: From Postgres to NoSQL

Developer Data Modeling Mistakes: From Postgres to NoSQL
"Debugging python applications inside k8s environment", Andrii Soldatenko

"Debugging python applications inside k8s environment", Andrii Soldatenko
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...

"LLMs for Python Engineers: Advanced Data Analysis and Semantic Kernel",Oleks...
Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost

Leverage Zilliz Serverless - Up to 50X Saving for Your Vector Storage Cost
Ten Tools for Security Professionals
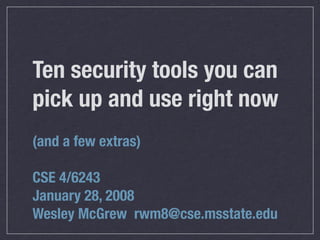
- 1. Ten security tools you can pick up and use right now (and a few extras) CSE 4/6243 January 28, 2008 Wesley McGrew rwm8@cse.msstate.edu
- 2. Introduction Focus is on “everyday” kinds of tools. Many security tools are double-edged swords The same tool that can be used to test your defenses can be used in an attack Use these tools in the lab! Never attack a network or system without explicit and specific permission!
- 3. Introduction This list is inspired by previous “tool” lectures given by Russ Ward and myself http://sectools.org/ also a great resource Focus is on free tools, unless otherwise stated also plenty of good commercial tools out there, such as Core Impact