I Left My iPhone in a Cab. Guess Where It Ended Up? Hint: AsiaIphone
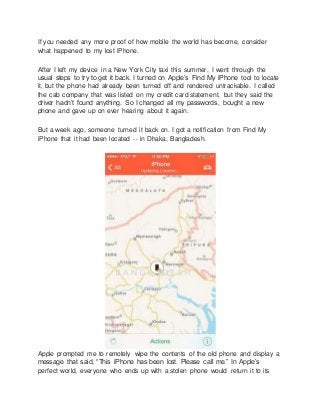
- 1. If you needed any more proof of how mobile the world has become, consider what happened to my lost iPhone. After I left my device in a New York City taxi this summer, I went through the usual steps to try to get it back. I turned on Apple’s Find My iPhone tool to locate it, but the phone had already been turned off and rendered untrackable. I called the cab company that was listed on my credit card statement, but they said the driver hadn’t found anything. So I changed all my passwords, bought a new phone and gave up on ever hearing about it again. But a week ago, someone turned it back on. I got a notification from Find My iPhone that it had been located -- in Dhaka, Bangladesh. Apple prompted me to remotely wipe the contents of the old phone and display a message that said, “This iPhone has been lost. Please call me.” In Apple’s perfect world, everyone who ends up with a stolen phone would return it to its
- 2. rightful owner. But that's wishful thinking when you consider how pervasive the problem is. A report by Lookout, a security firm based in San Francisco, found that one in 10 U.S. smartphone owners have been victims of phone theft. Almost 70 percent of them weren't able to recover their device. "Naturally, criminals resell phones wherever they can get the highest value on the black market," said Samir Gupte, senior product manager at Lookout. "Often times, this ends up being overseas in dodgy marketplaces in regions like Asia, Eastern Europe and Latin America where the resale value is much higher and there's likely limited scrutiny on the illegal transaction." A stolen iPhone is "as good as cash’’ because of the booming secondary market for the devices, according to Kyle Wiens, chief executive officer of iFixit, which repairs old phones. But for the new owner, "It’s worthless if you can’t unlock it." While my phone can still connect to WiFi, it no longer works on AT&T's network after I told the carrier it was lost, and that's probably another reason it ended up overseas, Wiens said. A used iPhone 5S in Bangladesh sells for about 35,000 taka, or $450, according to ads posted on resale sites. Last month, Bloomberg News found resellers in Hong Kong hawking the gold iPhone 6 for $3,600 before they were available in the area. Some obtained their stock from those who stood in line at U.S. stores, solely for the purpose of reselling them in another part of the world where it would be worth more. For those peddling stolen phones, new kill switch technologies that can render the devices useless will make this business more difficult. That's a big deal given that phone theft accounts for 40 percent of larcenies in major cities, according to Lookout. But Gupte said "we won't see a drastic decrease in phone theft overnight. You have to factor in the time it takes for these new phones to hit the market and consumers to upgrade to these newer handset models." Until then, beware of your phone getting stolen and ending up across the globe. After I shared my experience on Twitter, others told me their stories. One person’s phone ended up in Ho Chi Minh City in Vietnam in two weeks and one found its way from Israel to Ukraine in 24 hours.
- 3. As for my phone, the new owner never called me. The device went back offline. Maybe it's back on the market. Wherever it ends up, I just hope it's back online long enough for me to wipe the data.
