Symantec Survey: Cybersecurity Threats! Are You Prepared?
•
4 gostaram•3,969 visualizações
According to a recent Symantec study, only 50 percent of organizations surveyed feel they are prepared for targeted attacks. Does your greatest security threat match what others have told us?
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Mais de Symantec
Mais de Symantec (20)
Symantec Webinar | National Cyber Security Awareness Month: Protect IT

Symantec Webinar | National Cyber Security Awareness Month: Protect IT
Symantec Webinar | National Cyber Security Awareness Month: Secure IT

Symantec Webinar | National Cyber Security Awareness Month: Secure IT
Symantec Webinar | National Cyber Security Awareness Month - Own IT

Symantec Webinar | National Cyber Security Awareness Month - Own IT
Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)

Symantec Webinar: Preparing for the California Consumer Privacy Act (CCPA)
Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK

Symantec Webinar | How to Detect Targeted Ransomware with MITRE ATT&CK
Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...

Symantec Webinar | Security Analytics Breached! Next Generation Network Foren...
Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...

Symantec Webinar | Implementing a Zero Trust Framework to Secure Modern Workf...
Symantec Webinar | Tips for Successful CASB Projects

Symantec Webinar | Tips for Successful CASB Projects
Symantec Webinar: What Cyber Threats Are Lurking in Your Network?

Symantec Webinar: What Cyber Threats Are Lurking in Your Network?
Symantec Best Practices for Cloud Security: Insights from the Front Lines

Symantec Best Practices for Cloud Security: Insights from the Front Lines
Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...

Symantec - The Importance of Building Your Zero Trust Program on a Solid Plat...
Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...

Symantec Webinar | Redefining Endpoint Security- How to Better Secure the End...
Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear

Symantec Webinar Using Advanced Detection and MITRE ATT&CK to Cage Fancy Bear
GDPR Breach Notification Demystifying What the Regulators Want

GDPR Breach Notification Demystifying What the Regulators Want
Symantec Internet Security Threat Report (ISTR) 23 Webinar

Symantec Internet Security Threat Report (ISTR) 23 Webinar
Último
Falcon stands out as a top-tier P2P Invoice Discounting platform in India, bridging esteemed blue-chip companies and eager investors. Our goal is to transform the investment landscape in India by establishing a comprehensive destination for borrowers and investors with diverse profiles and needs, all while minimizing risk. What sets Falcon apart is the elimination of intermediaries such as commercial banks and depository institutions, allowing investors to enjoy higher yields.Unveiling Falcon Invoice Discounting: Leading the Way as India's Premier Bill...

Unveiling Falcon Invoice Discounting: Leading the Way as India's Premier Bill...Falcon Invoice Discounting
Último (20)
Ooty Call Gril 80022//12248 Only For Sex And High Profile Best Gril Sex Avail...

Ooty Call Gril 80022//12248 Only For Sex And High Profile Best Gril Sex Avail...
Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar

Al Mizhar Dubai Escorts +971561403006 Escorts Service In Al Mizhar
Falcon Invoice Discounting: Empowering Your Business Growth

Falcon Invoice Discounting: Empowering Your Business Growth
Lundin Gold - Q1 2024 Conference Call Presentation (Revised)

Lundin Gold - Q1 2024 Conference Call Presentation (Revised)
Durg CALL GIRL ❤ 82729*64427❤ CALL GIRLS IN durg ESCORTS

Durg CALL GIRL ❤ 82729*64427❤ CALL GIRLS IN durg ESCORTS
JAJPUR CALL GIRL ❤ 82729*64427❤ CALL GIRLS IN JAJPUR ESCORTS

JAJPUR CALL GIRL ❤ 82729*64427❤ CALL GIRLS IN JAJPUR ESCORTS
Unveiling Falcon Invoice Discounting: Leading the Way as India's Premier Bill...

Unveiling Falcon Invoice Discounting: Leading the Way as India's Premier Bill...
Nashik Call Girl Just Call 7091819311 Top Class Call Girl Service Available

Nashik Call Girl Just Call 7091819311 Top Class Call Girl Service Available
PARK STREET 💋 Call Girl 9827461493 Call Girls in Escort service book now

PARK STREET 💋 Call Girl 9827461493 Call Girls in Escort service book now
Kalyan Call Girl 98350*37198 Call Girls in Escort service book now

Kalyan Call Girl 98350*37198 Call Girls in Escort service book now
SEO Case Study: How I Increased SEO Traffic & Ranking by 50-60% in 6 Months

SEO Case Study: How I Increased SEO Traffic & Ranking by 50-60% in 6 Months
Lucknow Housewife Escorts by Sexy Bhabhi Service 8250092165

Lucknow Housewife Escorts by Sexy Bhabhi Service 8250092165
Getting Real with AI - Columbus DAW - May 2024 - Nick Woo from AlignAI

Getting Real with AI - Columbus DAW - May 2024 - Nick Woo from AlignAI
Symantec Survey: Cybersecurity Threats! Are You Prepared?
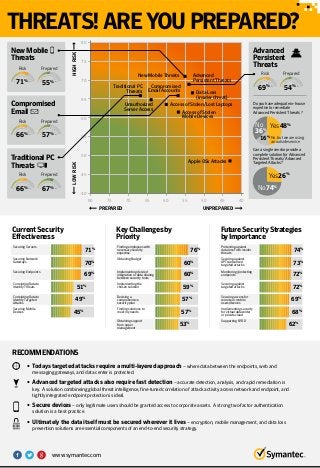
- 1. THREATS!AREYOUPREPARED? TraditionalPC Threats 100 80 60 20 40 0 10 30 50 70 90 66% Risk NewMobile Threats Risk 100 80 60 20 40 0 10 30 50 70 90 71% Compromised Email Risk 100 80 60 20 40 0 10 30 50 70 90 66% 80 75 70 65 60 55 50 45 40 40 45 50 55 60 65 70 75 80 UNPREPAREDPREPARED HIGHRISKLOWRISK RECOMMENDATIONS 100 80 60 20 40 0 10 30 50 70 90 67% Prepared Advanced Persistent Threats Doyouhaveadequatein-house expertisetoremediate AdvancedPersistentThreats? 100 80 60 20 40 0 10 30 50 70 90 69% Risk Canasinglevendorprovidea completesolutionforAdvanced PersistentThreats/Advanced TargetedAttacks? Prepared 100 80 60 20 40 0 10 30 50 70 90 54% Prepared 100 80 60 20 40 0 10 30 50 70 90 55% Prepared 100 80 60 20 40 0 10 30 50 70 90 57% • Todays targeted attacks require a multi-layered approach– where data between the endpoints, web and messaging gateways, and data center is protected. • Advanced targeted attacks also require fast detection– accurate detection, analysis, and rapid remediation is key. A solution combineing global threat intelligence, fine-tuned correlation of attack activity across network and endpoint, and tightly integrated endpoint protection is ideal. • Secure devices– only legitimate users should be granted access to corporate assets. A strong two-factor authentication solution is a best practice. • Ultimately the data itself must be secured wherever it lives– encryption, mobile management, and data loss prevention solutions are essential components of an end-to-end security strategy. Securing Servers Securing Network Gateways 71% 70% Securing Mobile Devices 45% Securing Endpoints Correlating Data to Identify Threats Correlating Data to Identify Targeted Attacks 69% 51% 49% CurrentSecurity Effectiveness Finding employees with necessary security expertise Obtaining support from upper management Obtaining Budget 76% 60% Finding solutions to meet my needs 57% 53% Implementing desired integration or data sharing between security tools Implementing the chosen solution Devising a comprehensive security plan 60% 59% 57% KeyChallengesby Priority Protecting against data loss from insider threats Supporting BYOD Securing against APTs/advanced targeted attacks Securing access for remote or mobile users/devices 74% 73% Implementing security for virtual datacenter or private cloud 68% 62% Monitoring/protecting endpoints Securing against targeted attacks 72% 72% 69% FutureSecurityStrategies byImportance Yes48%No 36% No74% Yes26% No,butweareusing anoutsideservice 16% New Mobile Threats Access of Stolen/Lost Laptops Access of Stolen Mobile Devices Apple OSs Attacks Unauthorized Server Access Data Loss (insider threat) Traditional PC Threats Compromised Email Accounts Advanced Persistent Threats www.symantec.com
