Build Cybersecurity Careers for Millennials
•
0 gostou•273 visualizações
Millennials are not being adequately informed about career opportunities in cybersecurity. Only 18% of Millennials say they want a career in cybersecurity, with young men more interested than young women. While many Millennials are taking basic steps to protect themselves online like password protecting devices, many also engage in risky online behaviors like using public WiFi without passwords or sharing passwords with others. There is a need to increase cybersecurity awareness and education programs to help guide more Millennials into cybersecurity careers and promote safer online practices.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...

Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...Massimiliano Mandolini
Recomendados
Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...

Infographic 2014 smart_grid_cybersecurity_survey_smart_modular_technologies_z...Massimiliano Mandolini
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
2018 NBOA Annual Meeting Information Technology Track

2018 NBOA Annual Meeting Information Technology Track
The impact of mobile devices on information security

The impact of mobile devices on information security
“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...

“The Impact of Mobile Devices on Information Security: A Survey of IT and Sec...
How to prevent data leaks with application security testing strategy

How to prevent data leaks with application security testing strategy
The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...

The Stand Against Cyber Criminals Lawyers, Take The Stand Against Cyber Crimi...
Destaque
Destaque (8)
National Strategies against Cyber Attacks - Philip Victor

National Strategies against Cyber Attacks - Philip Victor
In the Line of Fire-the Morphology of Cyber Attacks

In the Line of Fire-the Morphology of Cyber Attacks
How an Attack by a Cyber-espionage Operator Bypassed Security Controls

How an Attack by a Cyber-espionage Operator Bypassed Security Controls
Semelhante a Build Cybersecurity Careers for Millennials
PPT - SIGMA-GIZ Academies - Topic 2 - Spain_CarmenCabanillas

PPT - SIGMA-GIZ Academies - Topic 2 - Spain_CarmenCabanillasSupport for Improvement in Governance and Management SIGMA
Semelhante a Build Cybersecurity Careers for Millennials (20)
PPT - SIGMA-GIZ Academies - Topic 2 - Spain_CarmenCabanillas

PPT - SIGMA-GIZ Academies - Topic 2 - Spain_CarmenCabanillas
Kaspersky lab consumer_security_risks_survey_2015_eng

Kaspersky lab consumer_security_risks_survey_2015_eng
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
Technology and development : Laurent Elder - CRDI | KWS Forum

Technology and development : Laurent Elder - CRDI | KWS Forum
TeleSign Consumer Account Security Report 2015 FINAL

TeleSign Consumer Account Security Report 2015 FINAL
IRJET- A Survey on Social Networking and Awareness About Related Cyber Threat...

IRJET- A Survey on Social Networking and Awareness About Related Cyber Threat...
The Shifting State of Endpoint Risk: Key Strategies to Implement in 2011

The Shifting State of Endpoint Risk: Key Strategies to Implement in 2011
Último
Mitochondrial Fusion Vital for Adult Brain Function and Disease Understanding...

Mitochondrial Fusion Vital for Adult Brain Function and Disease Understanding...The Lifesciences Magazine
Último (12)
Geostrategic significance of South Asian countries.ppt

Geostrategic significance of South Asian countries.ppt
Mitochondrial Fusion Vital for Adult Brain Function and Disease Understanding...

Mitochondrial Fusion Vital for Adult Brain Function and Disease Understanding...
World Economic Forum : The Global Risks Report 2024

World Economic Forum : The Global Risks Report 2024
Build Cybersecurity Careers for Millennials
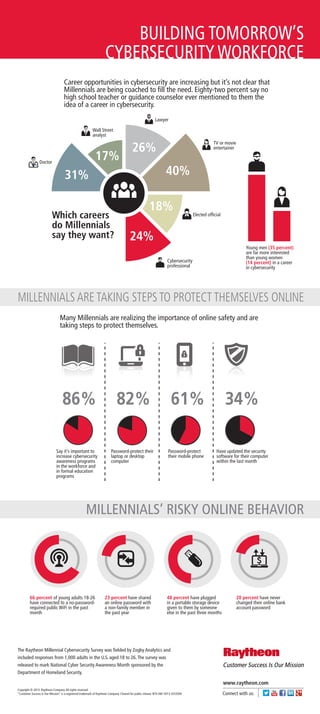
- 1. BUILDING TOMORROW’S CYBERSECURITY WORKFORCE Career opportunities in cybersecurity are increasing but it’s not clear that Millennials are being coached to fill the need. Eighty-two percent say no high school teacher or guidance counselor ever mentioned to them the idea of a career in cybersecurity. Lawyer Wall Street analyst 17% Doctor 26% 40% 31% Which careers do Millennials say they want? TV or movie entertainer 18% Elected official 24% Young men (35 percent) are far more interested than young women (14 percent) in a career in cybersecurity Cybersecurity professional MILLENNIALS ARE TAKING STEPS TO PROTECT THEMSELVES ONLINE Many Millennials are realizing the importance of online safety and are taking steps to protect themselves. 86% Say it’s important to increase cybersecurity awareness programs in the workforce and in formal education programs 82% Password-protect their laptop or desktop computer 61% Password-protect their mobile phone 34% Have updated the security software for their computer within the last month MILLENNIALS’ RISKY ONLINE BEHAVIOR 66 percent of young adults 18-26 have connected to a no-passwordrequired public WiFi in the past month 23 percent have shared an online password with a non-family member in the past year 48 percent have plugged in a portable storage device given to them by someone else in the past three months 20 percent have never changed their online bank account password The Raytheon Millennial Cybersecurity Survey was fielded by Zogby Analytics and included responses from 1,000 adults in the U.S. aged 18 to 26. The survey was released to mark National Cyber Security Awareness Month sponsored by the Department of Homeland Security. www.raytheon.com Copyright © 2013. Raytheon Company. All rights reserved. “Customer Success Is Our Mission" is a registered trademark of Raytheon Company. Cleared for public release. NTX AM 10/13 4333500 Connect with us:
