Instruction to remove the antivirus action rogue virus from the computer
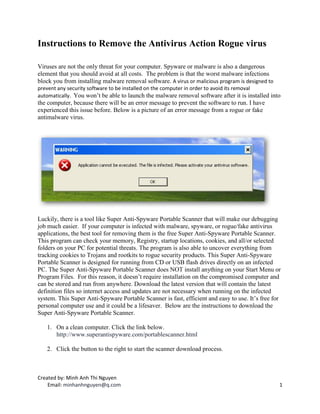
- 1. Instructions to Remove the Antivirus Action Rogue virus Viruses are not the only threat for your computer. Spyware or malware is also a dangerous element that you should avoid at all costs. The problem is that the worst malware infections block you from installing malware removal software. A virus or malicious program is designed to prevent any security software to be installed on the computer in order to avoid its removal automatically. You won’t be able to launch the malware removal software after it is installed into the computer, because there will be an error message to prevent the software to run. I have experienced this issue before. Below is a picture of an error message from a rogue or fake antimalware virus. Luckily, there is a tool like Super Anti-Spyware Portable Scanner that will make our debugging job much easier. If your computer is infected with malware, spyware, or rogue/fake antivirus applications, the best tool for removing them is the free Super Anti-Spyware Portable Scanner. This program can check your memory, Registry, startup locations, cookies, and all/or selected folders on your PC for potential threats. The program is also able to uncover everything from tracking cookies to Trojans and rootkits to rogue security products. This Super Anti-Spyware Portable Scanner is designed for running from CD or USB flash drives directly on an infected PC. The Super Anti-Spyware Portable Scanner does NOT install anything on your Start Menu or Program Files. For this reason, it doesn’t require installation on the compromised computer and can be stored and run from anywhere. Download the latest version that will contain the latest definition files so internet access and updates are not necessary when running on the infected system. This Super Anti-Spyware Portable Scanner is fast, efficient and easy to use. It’s free for personal computer use and it could be a lifesaver. Below are the instructions to download the Super Anti-Spyware Portable Scanner. 1. On a clean computer. Click the link below. http://www.superantispyware.com/portablescanner.html 2. Click the button to the right to start the scanner download process. Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 1
- 2. 3. When prompted, click on the SAVE button and select the desired location on your computer. Please be advised that the SAS Portable Scanner will be saved under a random file name so that malware infections won't block the scanner. If you are using a browser other than Internet Explorer then the prompt may be different. 4. Wait for the Scanner to Download. It may take some time to download, depending on the speed of your Internet connection. 5. Copy the downloaded file to a USB flash drive, CD or any preferred media to use on the infected system. Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 2
- 3. 6. Used the copied executable file to scan an infected computer. Remove and delete all detected files. Now, all you have to do is double click the executable file and select the area you want to scan such as drives, memory, registry, etc. Super Anti-Spyware Portable Scanner looks for any suspicious elements such as Trojans, dialers and adware, and lets you choose between putting them into quarantine and deleting them straight away. Below are the instructions to run or execute the Super Anti-Spyware Portable Scanner. 1. Click on the executable file and the welcome screen will display. Click the “Click here to start” button to start it up. 2. Pick your language… Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 3
- 4. 3. Click the Scan your Computer button. 4. Select the locations to scan, and choose “Perform Complete Scan”. There’s no point in a quick scan on an infected machine. The scan may take some time to finish, especially when you perform a full scan so please be patient. Click “next” to execute it. Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 4
- 5. 5. The application will scan through the system and find anything bad on it, and then let you remove it all easily. The picture below is a screenshot from an infected machine that I successfully cleaned using Super Anti-Spyware Portable Scanner. Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 5
- 6. 6. Remove what it found and reboot your computer. Super Anti-Spyware Portable Scanner has a couple of annoying features. It doesn't have real- time protection and doesn't support scheduled scans. Super Anti-Spyware is not an anti-virus software; it is meant for removing spyware and rogue applications that hold your PC for ransom. You still need Microsoft Security Essentials for your real-time protection. Personally, I have used Super Anti-Spyware Portable Scanner to clean at least two machines infected with really terrible rogue/fake antimalware applications. I have applied the above instructions to remove a nasty Antivirus Action Rogue antimalware from both Window XP and Vista operating systems. . Created by: Minh Anh Thi Nguyen Email: minhanhnguyen@q.com 6