(Spring 2013) Analysis of Damaged Barcodes
•
0 gostou•274 visualizações
A study on the assessment of two-dimensional barcodes on soil sample bags was conducted by former graduate student Jodi M. Gessner. We used the data she collected to further investigate what is the best bar code label to be used on soil samples so it is still able to be read through different damaging environments. The data that has been previously presented on correction levels 4,5 and 6 and was analyzed on 765 samples.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Detection and quantification of mutant alleles in tumor tissue is important to cancer research. Testing for the presence of mutations in circulating free DNA (cfDNA) is one of the less invasive research methods available at this time. Digital PCR presents a research tool for mutation detection in cfDNA at a sensitivity level of 1% and below. Challenges associated with digital PCR experiments for rare allele detection include understanding the limit of detection of the assay and platform. This work compares false positive assessment strategies using the signal levels of the no-amplification cluster. Once the false positive call rate is established, this work outlines a method to determine the limit of detection of the assay and platform, at a given level of confidence. Given the number of partitions, the interrogated volume and the false call rate, the tradeoffs between sample load and sensitivity are also discussed.
The mathematics outlined to calculate the theoretical limit of detection is applied on a set of assays from Thermo Fisher Scientific covering the KRAS codon mutations commonly found in tumor tissues. Experimental results showing a detection of at least 0.1% mutation rate are presented as examples. Test samples were created using both mutant plasmid and mutant genomic DNA mixed with wild-type genomic DNA at a predefined percentage.Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031

Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031Thermo Fisher Scientific
"Quantifiler® Trio kit and forensic samples management: a matter of degradation
Stefano Vernarecci
Forensic Genetics Laboratory
Scientific Police Service
Department of Ministry of Interior
Rome, Italy
Human Identification Solutions Conference – Madrid, Spain
March 4, 2015
Quantifiler® Trio DNA Quantification Kit
* Evaluate the reliability of the Quantifiler® Trio kit in providing information
on the level of degradation in a sample.
* Study the opportunity to use this information in predicting the quality of
the profile obtained after genotyping.
* Define operative implications, taking into account the DI, to apply to our
routine analysis in order to choose the best PCR strategy when dealing with
degraded samples
Please see also:
http://www.fsigenetics.com/article/S1872-4973(14)00280-4/abstract"Quantifiler® Trio kit and forensic samples management: a matter of degradation

Quantifiler® Trio kit and forensic samples management: a matter of degradationThermo Fisher Scientific
This study aims to analyze the effect of the population size, crossover probability, mutation probability, and the number of iterations on the distribution mileage of Indonesian largest logistics service provider in the Central Jakarta area with 43 distribution locations.
The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...

The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...Muhammad Irfan Kemal
Mais conteúdo relacionado
Semelhante a (Spring 2013) Analysis of Damaged Barcodes
Detection and quantification of mutant alleles in tumor tissue is important to cancer research. Testing for the presence of mutations in circulating free DNA (cfDNA) is one of the less invasive research methods available at this time. Digital PCR presents a research tool for mutation detection in cfDNA at a sensitivity level of 1% and below. Challenges associated with digital PCR experiments for rare allele detection include understanding the limit of detection of the assay and platform. This work compares false positive assessment strategies using the signal levels of the no-amplification cluster. Once the false positive call rate is established, this work outlines a method to determine the limit of detection of the assay and platform, at a given level of confidence. Given the number of partitions, the interrogated volume and the false call rate, the tradeoffs between sample load and sensitivity are also discussed.
The mathematics outlined to calculate the theoretical limit of detection is applied on a set of assays from Thermo Fisher Scientific covering the KRAS codon mutations commonly found in tumor tissues. Experimental results showing a detection of at least 0.1% mutation rate are presented as examples. Test samples were created using both mutant plasmid and mutant genomic DNA mixed with wild-type genomic DNA at a predefined percentage.Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031

Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031Thermo Fisher Scientific
"Quantifiler® Trio kit and forensic samples management: a matter of degradation
Stefano Vernarecci
Forensic Genetics Laboratory
Scientific Police Service
Department of Ministry of Interior
Rome, Italy
Human Identification Solutions Conference – Madrid, Spain
March 4, 2015
Quantifiler® Trio DNA Quantification Kit
* Evaluate the reliability of the Quantifiler® Trio kit in providing information
on the level of degradation in a sample.
* Study the opportunity to use this information in predicting the quality of
the profile obtained after genotyping.
* Define operative implications, taking into account the DI, to apply to our
routine analysis in order to choose the best PCR strategy when dealing with
degraded samples
Please see also:
http://www.fsigenetics.com/article/S1872-4973(14)00280-4/abstract"Quantifiler® Trio kit and forensic samples management: a matter of degradation

Quantifiler® Trio kit and forensic samples management: a matter of degradationThermo Fisher Scientific
This study aims to analyze the effect of the population size, crossover probability, mutation probability, and the number of iterations on the distribution mileage of Indonesian largest logistics service provider in the Central Jakarta area with 43 distribution locations.
The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...

The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...Muhammad Irfan Kemal
Semelhante a (Spring 2013) Analysis of Damaged Barcodes (20)
6-23-2015 AACC Poster HIV Incidence Assay - Stengelin_Final

6-23-2015 AACC Poster HIV Incidence Assay - Stengelin_Final
An evaluation of computer based color vision deficiency test egypt as a stu...

An evaluation of computer based color vision deficiency test egypt as a stu...
Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031

Limit of Detection of Rare Targets Using Digital PCR | ESHG 2015 Poster PS14.031
Deep learning methods applied to physicochemical and toxicological endpoints

Deep learning methods applied to physicochemical and toxicological endpoints
Quantifiler® Trio kit and forensic samples management: a matter of degradation

Quantifiler® Trio kit and forensic samples management: a matter of degradation
High Sensitivity Sanger Sequencing for Minor Variant Detection

High Sensitivity Sanger Sequencing for Minor Variant Detection
Part 5 of RNA-seq for DE analysis: Detecting differential expression

Part 5 of RNA-seq for DE analysis: Detecting differential expression
Cytoscan_Copy_Number_Confirmation_with_SYBR_Green_qPCR_white_paper

Cytoscan_Copy_Number_Confirmation_with_SYBR_Green_qPCR_white_paper
FUNCTION OF RIVAL SIMILARITY IN A COGNITIVE DATA ANALYSIS

FUNCTION OF RIVAL SIMILARITY IN A COGNITIVE DATA ANALYSIS
The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...

The Effect of Genetic Algorithm Parameters Tuning for Route Optimization in T...
uses of statistics in experimental plant pathology

uses of statistics in experimental plant pathology
Mais de International Center for Biometric Research
The human signature provides a natural and publically-accepted legally-admissible method for providing authentication to a process. Automatic biometric signature systems assess both the drawn image and the temporal aspects of signature construction, providing enhanced verification rates over and above conventional outcome assessment. To enable the capture of these constructional data requires the use of specialist ‘tablet’ devices. In this paper we explore the enrolment performance using a range of common signature capture devices and investigate the reasons behind user preference. The results show that writing feedback and familiarity with conventional ‘paper and pen’ donation configurations are the primary motivation for user preference. These results inform the choice of signature device from both technical performance and user acceptance viewpoints.An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...International Center for Biometric Research
This is the presentation given at the Biometrics 2014 conference in London on October 21st, 2014Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...International Center for Biometric Research
According to a report by Frost and Sullivan in 2007, revenues for non-AFIS fingerprint devices in notebook PC's and wireless devices is anticipated to grow from $148.5 million to $1588.0 million by 2014, a compound annual growth rate of 40.3% [1]. The AFIS market has a compound annual growth rate of 15.2% with revenues of $445.0 million in 2007. With the development of mobile applications in a number of different market segments, such as healthcare, retail, and law enforcement, this paper analyzed the performance of fingerprints of different sizes, from different sensors...(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applicationsInternational Center for Biometric Research
Mais de International Center for Biometric Research (20)
An Investigation into Biometric Signature Capture Device Performance and User...

An Investigation into Biometric Signature Capture Device Performance and User...
Best Practices in Reporting Time Duration in Biometrics

Best Practices in Reporting Time Duration in Biometrics
Advances in testing and evaluation using Human-Biometric sensor interaction m...

Advances in testing and evaluation using Human-Biometric sensor interaction m...
(2010) Fingerprint recognition performance evaluation for mobile ID applications

(2010) Fingerprint recognition performance evaluation for mobile ID applications
Último
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Último (20)
What Are The Drone Anti-jamming Systems Technology?

What Are The Drone Anti-jamming Systems Technology?
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
(Spring 2013) Analysis of Damaged Barcodes
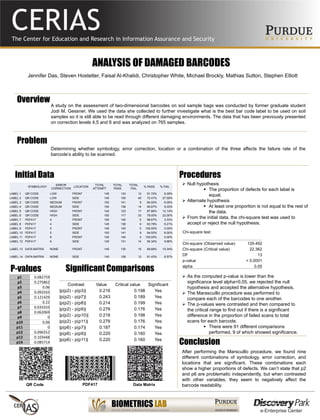
- 1. ANALYSIS OF DAMAGED BARCODES Jennifer Das, Steven Hostetler, Faisal Al-Khalidi, Christopher White, Michael Brockly, Mathias Sutton, Stephen Elliott Overview A study on the assessment of two-dimensional barcodes on soil sample bags was conducted by former graduate student Jodi M. Gessner. We used the data she collected to further investigate what is the best bar code label to be used on soil samples so it is still able to be read through different damaging environments. The data that has been previously presented on correction levels 4,5 and 6 and was analyzed on 765 samples. Problem Determining whether symbology, error correction, location or a combination of the three affects the failure rate of the barcode’s ability to be scanned. Initial Data SYMBOLOGY ERROR CORRECTION LOCATION TOTAL ATTEMPT TOTAL PASS TOTAL FAIL % PASS % FAIL LABEL 1 QR CODE LOW FRONT 145 133 12 91.72% 8.28% LABEL 2 QR CODE LOW SIDE 145 105 40 72.41% 27.59% LABEL 3 QR CODE MEDIUM FRONT 150 141 9 94.00% 6.00% LABEL 4 QR CODE MEDIUM SIDE 150 136 14 90.67% 9.33% LABEL 5 QR CODE HIGH FRONT 140 123 17 87.86% 12.14% LABEL 6 QR CODE HIGH SIDE 150 117 33 78.00% 22.00% LABEL 7 PDF417 4 FRONT 150 145 5 96.67% 3.33% LABEL 8 PDF417 4 SIDE 145 136 9 93.79% 6.21% LABEL 9 PDF417 5 FRONT 145 145 0 100.00% 0.00% LABEL 10 PDF417 5 SIDE 150 141 9 94.00% 6.00% LABEL 11 PDF417 6 FRONT 140 140 0 100.00% 0.00% LABEL 12 PDF417 6 SIDE 145 131 14 90.34% 9.66% LABEL 13 DATA MATRIX NONE FRONT 145 130 15 89.66% 10.34% LABEL 14 DATA MATRIX NONE SIDE 140 128 12 91.43% 8.57% Procedures Null hypothesis The proportion of defects for each label is equal. Alternate hypothesis At least one proportion is not equal to the rest of the data. From the initial data, the chi-square test was used to accept or reject the null hypothesis. Chi-square test: Chi-square (Observed value) 129.492 Chi-square (Critical value) 22.362 DF 13 p-value < 0.0001 alpha 0.05 As the computed p-value is lower than the significance level alpha=0.05, we rejected the null hypothesis and accepted the alternative hypothesis. The Marascuillo procedure was performed to compare each of the barcodes to one another. The p-values were contrasted and then compared to the critical range to find out if there is a significant difference in the proportion of failed scans to total scans for each barcode. There were 91 different comparisons performed, 9 of which showed significance. p1 0.082759 p2 0.275862 p3 0.06 p4 0.093333 p5 0.121429 p6 0.22 p7 0.033333 p8 0.062069 p9 0 p10 0.06 p11 0 p12 0.096552 p13 0.103448 p14 0.085714 P-values Conclusion After performing the Marscuillo procedure, we found nine different combinations of symbology, error correction, and locations that are significant. These combinations each show a higher proportions of defects. We can’t state that p2 and p6 are problematic independently, but when contrasted with other variables, they seem to negatively affect the barcode readability. Contrast Value Critical value Significant |p(p2) - p(p3)| 0.216 0.198 Yes |p(p2) - p(p7)| 0.243 0.189 Yes |p(p2) - p(p8)| 0.214 0.199 Yes |p(p2) - p(p9)| 0.276 0.176 Yes |p(p2) - p(p10)| 0.216 0.198 Yes |p(p2) - p(p11)| 0.276 0.176 Yes |p(p6) - p(p7)| 0.187 0.174 Yes |p(p6) - p(p9)| 0.220 0.160 Yes |p(p6) - p(p11)| 0.220 0.160 Yes Significant Comparisons QR Code PDF417 Data Matrix
