Enhancing Computer Security via End-to-End Communication Visualization
•Transferir como PPT, PDF•
2 gostaram•819 visualizações
Enhancing Computer Security via End-to-End Communication Visualization
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Recomendados
Mais conteúdo relacionado
Semelhante a Enhancing Computer Security via End-to-End Communication Visualization
Semelhante a Enhancing Computer Security via End-to-End Communication Visualization (20)
Home automation using IoT and AWS Cloud technology

Home automation using IoT and AWS Cloud technology
Leveraging the strength of OSGi to deliver a convergent IoT Ecosystem - O Log...

Leveraging the strength of OSGi to deliver a convergent IoT Ecosystem - O Log...
Edge optimized architecture for fabric defect detection in real-time

Edge optimized architecture for fabric defect detection in real-time
IoT ( M2M) - Big Data - Analytics: Emulation and Demonstration

IoT ( M2M) - Big Data - Analytics: Emulation and Demonstration
Final ProjectFinal Project Details Description Given a spec.docx

Final ProjectFinal Project Details Description Given a spec.docx
A modern approach to safeguarding your ICS and SCADA systems

A modern approach to safeguarding your ICS and SCADA systems
Toolkit Titans - Crafting a Cutting-Edge, Open-Source Security Operations Too...

Toolkit Titans - Crafting a Cutting-Edge, Open-Source Security Operations Too...
Introduction to SDN and Network Programmability - BRKRST-1014 | 2017/Las Vegas

Introduction to SDN and Network Programmability - BRKRST-1014 | 2017/Las Vegas
GDG Cloud Southlake #9 Secure Cloud Networking - Beyond Cloud Boundaries

GDG Cloud Southlake #9 Secure Cloud Networking - Beyond Cloud Boundaries
D-STREAMON - NFV-capable distributed framework for network monitoring

D-STREAMON - NFV-capable distributed framework for network monitoring
Mais de amiable_indian
Mais de amiable_indian (20)
Insecure Implementation of Security Best Practices: of hashing, CAPTCHA's and...

Insecure Implementation of Security Best Practices: of hashing, CAPTCHA's and...
AntiSpam - Understanding the good, the bad and the ugly

AntiSpam - Understanding the good, the bad and the ugly
Network Vulnerability Assessments: Lessons Learned

Network Vulnerability Assessments: Lessons Learned
Economic offenses through Credit Card Frauds Dissected

Economic offenses through Credit Card Frauds Dissected
No Substitute for Ongoing Data, Quantification, Visualization, and Story-Telling

No Substitute for Ongoing Data, Quantification, Visualization, and Story-Telling
Último
Call Girl Mumbai Indira Call Now: 8250077686 Mumbai Escorts Booking Contact Details WhatsApp Chat: +91-8250077686 Mumbai Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertainin. Plus they look fabulously elegant; making an impressionable. Independent Escorts Mumbai understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7

(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7Call Girls in Nagpur High Profile Call Girls
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai Escorts
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Today call girl service available 24X7*▬█⓿▀█▀ 𝐈𝐍𝐃𝐄𝐏𝐄𝐍𝐃𝐄𝐍𝐓 CALL 𝐆𝐈𝐑𝐋 𝐕𝐈𝐏 𝐄𝐒𝐂𝐎𝐑𝐓 SERVICE ✅
⭐➡️HOT & SEXY MODELS // COLLEGE GIRLS
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
★ SAFE AND SECURE HIGH CLASS SERVICE AFFORDABLE RATE
★ 100% SATISFACTION,UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL 24x7 :: #S07 3 * 5 *7 *Star Hotel Service .In Call & Out call SeRvIcEs :
★ A-Level (5 star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob)Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
100% SAFE AND SECURE 24 HOURS SERVICE AVAILABLE HOME AND HOTEL SERVICES
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...roshnidevijkn ( Why You Choose Us? ) Escorts
VIP Independent Call Girls in Mumbai 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S030524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-9920725232
VIP Independent Call Girls in Mumbai 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Mumbai 🌹 9920725232 ( Call Me ) Mumbai Escorts ...dipikadinghjn ( Why You Choose Us? ) Escorts
Top Rated Pune Call Girls Shikrapur ⟟ 6297143586 ⟟ Call Me For Genuine Sex Service At Affordable Rate
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Top Rated Pune Call Girls Shikrapur ⟟ 6297143586 ⟟ Call Me For Genuine Sex S...

Top Rated Pune Call Girls Shikrapur ⟟ 6297143586 ⟟ Call Me For Genuine Sex S...Call Girls in Nagpur High Profile
Booking open Available Pune Call Girls Talegaon Dabhade 6297143586 Call Hot Indian Girls Waiting For You To Fuck
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Booking open Available Pune Call Girls Talegaon Dabhade 6297143586 Call Hot ...

Booking open Available Pune Call Girls Talegaon Dabhade 6297143586 Call Hot ...Call Girls in Nagpur High Profile
Top Rated Pune Call Girls Dighi ⟟ 6297143586 ⟟ Call Me For Genuine Sex Service At Affordable Rate
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Top Rated Pune Call Girls Dighi ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...

Top Rated Pune Call Girls Dighi ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...Call Girls in Nagpur High Profile
Model Call Girl Services in Delhi reach out to us at 🔝 9953056974 🔝✔️✔️
Our agency presents a selection of young, charming call girls available for bookings at Oyo Hotels. Experience high-class escort services at pocket-friendly rates, with our female escorts exuding both beauty and a delightful personality, ready to meet your desires. Whether it's Housewives, College girls, Russian girls, Muslim girls, or any other preference, we offer a diverse range of options to cater to your tastes.
We provide both in-call and out-call services for your convenience. Our in-call location in Delhi ensures cleanliness, hygiene, and 100% safety, while our out-call services offer doorstep delivery for added ease.
We value your time and money, hence we kindly request pic collectors, time-passers, and bargain hunters to refrain from contacting us.
Our services feature various packages at competitive rates:
One shot: ₹2000/in-call, ₹5000/out-call
Two shots with one girl: ₹3500/in-call, ₹6000/out-call
Body to body massage with sex: ₹3000/in-call
Full night for one person: ₹7000/in-call, ₹10000/out-call
Full night for more than 1 person: Contact us at 🔝 9953056974 🔝. for details
Operating 24/7, we serve various locations in Delhi, including Green Park, Lajpat Nagar, Saket, and Hauz Khas near metro stations.
For premium call girl services in Delhi 🔝 9953056974 🔝. Thank you for considering us!call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️

call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️9953056974 Low Rate Call Girls In Saket, Delhi NCR
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S040524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-9920725232
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...dipikadinghjn ( Why You Choose Us? ) Escorts
Low Rate Call Girls Pune Vedika Call Now: 8250077686 Pune Escorts Booking Contact Details WhatsApp Chat: +91-8250077686 Pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertainin. Plus they look fabulously elegant; making an impressionable. Independent Escorts Pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together. We provide –(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7

(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7Call Girls in Nagpur High Profile Call Girls
From Luxury Escort Service Kamathipura : 9352852248 Make on-demand Arrangements Near You
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9352852248
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 🌐 beautieservice.com 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9352852248
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S020524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-9352852248
From Luxury Escort Service Kamathipura : 9352852248 Make on-demand Arrangemen...

From Luxury Escort Service Kamathipura : 9352852248 Make on-demand Arrangemen...From Luxury Escort : 9352852248 Make on-demand Arrangements Near yOU
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Escorts * Ruhi Singh *
FOR BOOKING ★ A-Level (5-star Escort) (Akanksha): ☎️ +91-9920725232
AVAILABLE FOR COMPLETE ENJOYMENT WITH HIGH PROFILE INDIAN MODEL AVAILABLE HOTEL & HOME
Visit Our Site For More Pleasure in your City 👉 ☎️ +91-9920725232 👈
★ SAFE AND SECURE HIGH-CLASS SERVICE AFFORDABLE RATE
★
SATISFACTION, UNLIMITED ENJOYMENT.
★ All Meetings are confidential and no information is provided to any one at any cost.
★ EXCLUSIVE PROFILes Are Safe and Consensual with Most Limits Respected
★ Service Available In: - HOME & HOTEL Star Hotel Service. In Call & Out call
SeRvIcEs :
★ A-Level (star escort)
★ Strip-tease
★ BBBJ (Bareback Blowjob) Receive advanced sexual techniques in different mode make their life more pleasurable.
★ Spending time in hotel rooms
★ BJ (Blowjob Without a Condom)
★ Completion (Oral to completion)
★ Covered (Covered blowjob Without condom
★ANAL SERVICES.
Contact me
TELEPHONE
WHATSAPP
Looking for Enjoy all Day(Akanksha) : ☎️ +91-9920725232
Mumbai, Andheri, Navi Mumbai, Thane, Mumbai Airport, Mumbai Central, South Mumbai, Juhu, Bandra, Colaba, Nariman point, Malad, Powai, Mira Road, Dahisar, Mira Bhayandar, Worli, Santacruz, Vile Parle, Lower Parel, Chembur, Dadar, Ghatkopar, Kurla, Mulund, Goregaon, Kandivali, Borivali, Jogeshwari, Kalyan, Vashi , Nerul, Panvel, Dombivli, Lokhandwala, Four Bungalows, Versova, NRI Complex, Kharghar, Belapur, Taloja, Marine Drive, Hiranandani Gardens, Churchgate, Marine lines, Oshiwara, DN Nagar, Jb Nagar, Marol Naka, Saki Naka, Andheri East, Andheri West, Bandra West, Bandra East , Thane West, Ghodbundar Road,
There is a lot of talk about it in the media and news, so you might be wondering if this particular service is really worth the effort. A call girl service is exactly what it sounds like – a service where a woman offers sexual services over the phone. This type of service has been around for a long time and has become increasingly popular over the years. In most cases, call girl services are legal and regulated in many countries. There are a few things to keep in mind when considering the choice of whether to use a call girl service. First and foremost, make sure that you are comfortable with the particular person you are using the service from. Second, research accordingly before choosing a call girl. Don't just go with the first provider that comes up in your search; get opinions from others as well. Finally, be sure to have fun while using a call girl service; it's not just about sex. S040524N
★OUR BEST SERVICES: - FOR BOOKING ★ A-Level (5-star escort) ★ Strip-tease ★ BBBJ (Bareback Blowjob) ★ Spending time in my rooms ★ BJ (Blowjob Without a Condom) ★ COF (Come on Face) ★ Completion ★ (Oral to completion) noncovered ★ Special Massage ★ O-Level (Oral) ★ Blow Job; ★ Oral fun uncovered) ★ COB (Come on Body) ★. Extra ball (Have ride many times) ☛ ☛ ☛ ✔✔ secure✔✔ 100% safe WHATSAPP CALL ME +91-992072523VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...dipikadinghjn ( Why You Choose Us? ) Escorts
Último (20)
(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7

(INDIRA) Call Girl Mumbai Call Now 8250077686 Mumbai Escorts 24x7
VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...

VIP Kalyan Call Girls 🌐 9920725232 🌐 Make Your Dreams Come True With Mumbai E...
VIP Independent Call Girls in Mumbai 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Mumbai 🌹 9920725232 ( Call Me ) Mumbai Escorts ...
8377087607, Door Step Call Girls In Kalkaji (Locanto) 24/7 Available

8377087607, Door Step Call Girls In Kalkaji (Locanto) 24/7 Available
Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...

Navi Mumbai Cooperetive Housewife Call Girls-9833754194-Natural Panvel Enjoye...
Top Rated Pune Call Girls Shikrapur ⟟ 6297143586 ⟟ Call Me For Genuine Sex S...

Top Rated Pune Call Girls Shikrapur ⟟ 6297143586 ⟟ Call Me For Genuine Sex S...
Best VIP Call Girls Morni Hills Just Click Me 6367492432

Best VIP Call Girls Morni Hills Just Click Me 6367492432
Call Girls Rajgurunagar Call Me 7737669865 Budget Friendly No Advance Booking

Call Girls Rajgurunagar Call Me 7737669865 Budget Friendly No Advance Booking
Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai

Vasai-Virar Fantastic Call Girls-9833754194-Call Girls MUmbai
falcon-invoice-discounting-unlocking-prime-investment-opportunities

falcon-invoice-discounting-unlocking-prime-investment-opportunities
Booking open Available Pune Call Girls Talegaon Dabhade 6297143586 Call Hot ...

Booking open Available Pune Call Girls Talegaon Dabhade 6297143586 Call Hot ...
20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...

20240419-SMC-submission-Annual-Superannuation-Performance-Test-–-design-optio...
Top Rated Pune Call Girls Dighi ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...

Top Rated Pune Call Girls Dighi ⟟ 6297143586 ⟟ Call Me For Genuine Sex Servi...
call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️

call girls in Sant Nagar (DELHI) 🔝 >༒9953056974 🔝 genuine Escort Service 🔝✔️✔️
VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...

VIP Independent Call Girls in Taloja 🌹 9920725232 ( Call Me ) Mumbai Escorts ...
Call Girls Banaswadi Just Call 👗 7737669865 👗 Top Class Call Girl Service Ban...

Call Girls Banaswadi Just Call 👗 7737669865 👗 Top Class Call Girl Service Ban...
(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7

(Vedika) Low Rate Call Girls in Pune Call Now 8250077686 Pune Escorts 24x7
From Luxury Escort Service Kamathipura : 9352852248 Make on-demand Arrangemen...

From Luxury Escort Service Kamathipura : 9352852248 Make on-demand Arrangemen...
VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...

VIP Independent Call Girls in Bandra West 🌹 9920725232 ( Call Me ) Mumbai Esc...
Enhancing Computer Security via End-to-End Communication Visualization
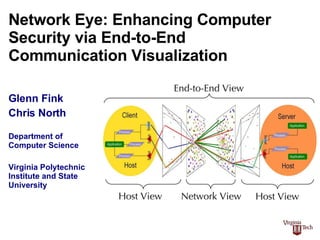
- 1. Network Eye: Enhancing Computer Security via End-to-End Communication Visualization Glenn Fink Chris North Department of Computer Science Virginia Polytechnic Institute and State University
- 2. This presentation focuses on a novel computer security visualization technology: Network Eye End-to-End communication visualization concept Network Eye’s place as a tool for computer security visualization Partnership opportunities involving Network Eye
- 3. Network Eye occupies new territory in the computer security tool landscape Charts & Graphs Narrow Broad C OMMUNICATION C ONTEXT Linear Spatial P RESENTATION M ODE Internal Host View Text-Based Dashboards Visualizations Log scanners, Antivirus, ps, top, Tripwire HIDS Networked Host View netstat, lsof, tcpview, host firewalls, vulner-ability checkers, HIDS Spectrum, Orcallator End-to-End View Network View tcpdump, Ethereal, Network Firewalls, NIDS S-Net, NVisionIP ( small multiple and machine views ), AutoFocus, MRTG VisFlowConnect, NVisionIP ( Galaxy View ), EtherApe, RumInt, Rivet (Visible Computer) Big Brother, Nagios NVisionCC? Sguil The Visible Computer applet NETWORK EYE
- 4. Network Eye provides End-to-End visualization by correlating network and host activities Source & Destination Port Maps Source & Destination Network Maps Client Host View Server Host View Network View End-to-End View 23:04:22.813882 10.0.1.2.50128 > 239.255.255.253.svrloc: udp 49 23:04:22.988068 10.0.1.2.50130 > 10.0.1.1.osu-nms: udp 4 23:04:22.989256 10.0.1.1.osu-nms > 10.0.1.2.50130: udp 108 23:04:23.038353 10.0.1.2.50128 > 239.255.255.253.svrloc: udp 49 23:04:23.084775 10.0.1.3.52750 > 10.0.1.1.osu-nms: udp 4 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:27.988076 10.0.1.2.50131 > 10.0.1.1.osu-nms: udp 4 23:04:27.989258 10.0.1.1.osu-nms > 10.0.1.2.50131: udp 108 23:04:29.656096 10.0.1.1.domain > 10.0.1.3.60857: 6852 NXDomain* 0/0/0 (39) 23:04:35.614864 10.0.1.3.52754 > 10.0.1.1.osu-nms: udp 4 23:04:35.617335 10.0.1.1.osu-nms > 10.0.1.3.52754: udp 108 23:04:37.142782 10.0.1.3.ipp > 10.0.1.255.ipp: udp 100 Text-only Packet Traces PID TT STAT TIME COMMAND 1 ?? Ss 0:00.03 /sbin/init 2 ?? Ss 0:28.26 /sbin/mach_init 51 ?? Ss 0:02.39 kextd 77 ?? Ss 0:56.27 update 81 ?? Ss 0:00.00 dynamic_pager -H 40000000 -L 160000000 -S 80000000 -F 112 ?? Ss 20:43.98 configd 135 ?? Ss 0:01.26 /System/Library/CoreServices/SecurityServer -X 187 ?? Ss 0:02.39 /sbin/autodiskmount -va 280 ?? Ss 0:01.61 syslogd 291 ?? Ss 0:00.01 /usr/libexec/crashreporterd 522 ?? S 0:00.71 /usr/sbin/httpd 635 ?? S 0:00.59 /usr/sbin/httpd 750 ?? S 0:01.48 /System/Library/CoreServices/SecurityAgent.app/Conten 1437 ?? Ss 0:07.20 slpd -f /etc/slpsa.conf 1477 ?? Ss 0:05.56 /usr/sbin/lookupd 1588 ?? S 0:02.51 /Applications/Library/BBEdit Lite 6.1/Bee bee Edit /A 1579 std Ss 0:00.45 login -pf glenn 1580 std S 0:00.06 -tcsh (tcsh) Text-only Process Listings
- 5. Portall is a prototype of Network Eye’s “networked host view” Portall shows clients and servers It shows each process’s network connections Portall can display packet dumps
- 6. Network Eye GL is a “Network View” prototype written in OpenGL Each dot represents a host machine On the left are clients, on the right are servers Most trusted hosts appear near the center Lines of various colors illustrate connections
- 7. Network Eye presents mutually beneficial opportunities for research partnership Business partnership provides relevance and experience for academics Partnership is a win-win proposition Academic partnership provides business with cutting-edge research
Notas do Editor
- Who I am: * Ph.D. student in Computer Security Visualization at VT * Experience: (Army Officer 12yrs. and Naval Civilian Engineer 15yrs.) * Computer security projects and interests * MS in Software Engineering * finkga@vt.edu, <http://csgrad.cs.vt.edu/~finkga> Who Dr. North is: * Assistant Professor of CS at VT and my advisor * Many projects in information visualization, and usability, including $345K gigapixel display project. * Ph.D. in Information Visualization from UMD. * <http://people.cs.vt.edu/~north/> Computer security landscape: * Legislative compliance is becoming a key CIO/CISO function (similar to safety & environmental) * Gramm-Leach-Bliley, Sarbanes-Oxley (Section 404) * Double jeopardy: being attacked and then being sued for the results. Negligence and due-diligence. * Rising requirement for online systems coupled with the rising risk of attack and the decreasing window of effective patching time * Exponentially increasing cybercrime since the inception of the Internet. * Phishing attacks Brief explanation of Network Eye and end-to-end communication visualization.