Intro to Botnets - Bilal ZIANE
- 1. Introduction to Botnets Introduction to Botnets ZIANE Bilal http://www.ZIANEBilal.com
- 2. 1 www.ZIANEBilal.com 1
- 3. 2 Definition of a Botnet www.ZIANEBilal.com 1- Definition of a Botnet A bot is an abbreviation for a software robot that can be used for malicious or beneficial purposes, but in this post I will focus on the bad manipulation of botnets, I will try to explain that kind of botnets that allow attacker to remotely control the affected computer without the owner knowledge. Indeed, what is a Botnet? Botnet or Drone-Army, designed as a Zombie-Army as well, is an abbreviation for a robot Network. Botnet is a network of compromised computers that can be remotely controlled by an attacker, called the BotMaster or BotHerder and each infected computer by a bot can be referred as a Zombie or as a Drone. Bots are remotely controlled through commands sent via the internet by the Botmaster using the C&C server, which stands for Command and Control server (C&C) a remote control & communication channels, for sending and receiving commands between the Botherder and the Zombies. 2
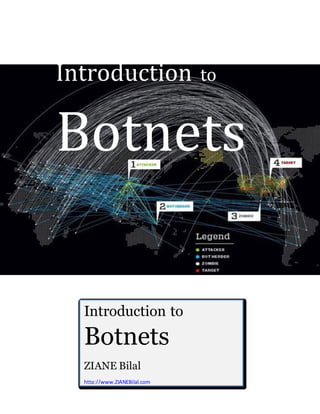
- 4. 3 Attacking Behavior of Botnets www.ZIANEBilal.com Sizes of Botnets Zeus: 3.6 million compromised computers Koobface: 2.9 million TidServ: 1.5 million Trojan.Fakeavalert: 1.4 million TR/Dldr.Agent.JKH: 1.2 million 2- Attacking Behavior of Botnets Distributed Denial-of-Service Attacks Installing Advertisement Addons Spamming Google AdSense abuse Sniffing Traffic Manipulating online polls/games Keylogging Mass identity theft Spreading new malware Phishing attacks Figure representing how botnets are used in DDos attacks. 3
- 5. 4 Types of Botnets www.ZIANEBilal.com 3- Types of Botnets Many types of botnets exist, I will try the explain the most used ones, starting by the HTTP botnet the most commonly used, which exploits vulnerabilities in web browsers, then a I will give short presentation of the IRC Botnet that give the attacker to silently control computers through internet relay chat channel, and at the end the P2P Peer to Peer Botnet that infect files shared on P2P services. A- HTTP Botnets: Used for creation and control of botnets. The zombies sign into an HTTP server at listening mode waiting for commands from the Botmaster, or they will visit pre-designated sites to get commands that are coded into the site’s files. Many HTTP bots have their own servers for downloading malware, phishing, etc. B- IRC Botnets: The most botnets rely on the IRC protocol. This is because the IRC protocol has been around the longest, and that is where earlier botnets operated before HTTP came along. IRC is used by a wide variety of applications to allow users to have simple text based chatting environments. Infected IRC clients log into a specific IRC server and wait for specially formatted text messages that contain commands. Commands can also be encoded into the title or name of the chat channel, so that every bot entering can be given commands. IRC Botnets are generally the most complex and the hardest to detect. C- P2P Botnets: Many P2P applications are utilized by bot herders to share files that have bots and malware attached. In most cases, these bots are pre- programmed to perform specific functions when a file is opened, or when a container application like a game or desktop application is installed. The main reason why IRC is so popular is: A- Easiness - setting up private servers or use existing ones are easy B- Interactivity - full two-way communication between the server and client. C- Control – all the needed functionalities already exist in the IRC protocol (credentials such as usernames, passwords and channels) D- Redundancy possibilities – by linking several servers together, one server can go down while the botnet is still functioning by connecting to other IRC servers. 4
- 6. 5 Botnet topologies www.ZIANEBilal.com 4- Botnet topologies Botnets come in all kinds of shapes and sizes. As a result, they employ a range of C&C topologies and each have relative strengths and weaknesses. C&C topologies encountered in the wild typically match one of the following types: A- Star typology [+] Strengths: Speed of control, due to the direct communicationbetween the bot and C&C server instructions are transferred rapidly. [-] Weaknesses: If the C&C server is down the botnet will be useless. 5
- 7. 6 Botnet topologies www.ZIANEBilal.com A- Multi-server [+] Strengths: Geographic optimissation, Multiple geographically distributed C&C servers speed up communications between botnet elements. And if one single C&C goes down, the botnet operator still maintain control over all bot agents. [-] Weaknesses: Require multiple C&C server infrastructures. B- Hierarchical [+] Strengths: Interception or hijacking of bot agents will not enumerate all numbers of the botnet and is likely to reveal the C&C server. [-] Weaknesses: slow communication among bots breaches, causing a high degree of latency and that makes attacks and malicious operations difficult. 6
- 8. 7 Example of well-known Botnets www.ZIANEBilal.com B- Random [+] Strengths: Lack of a centralized C&C infrastructure and the many-to-many communication links between bot agents make it very resilient to shutdown. [-] Weaknesses: Command latency and botnet enumeration. 5- Example of well-known Botnets • Agobot/Phatbot/Forbot/XtremBot. • SDBot/RBot/UrBot/UrXBot. • mIRC-based Bots - GT-Bots. • DSNX Bots. • Q8 Bots. • Kaiten. 7
- 9. 8 Botnet Detection www.ZIANEBilal.com 6- Botnet Detection A- Static analysis The static method analysis for botnet detection is based on detecting malicious activities in the network, including URLs, IP addresses and executable binaries, process of identifying bad items. In such methods of botnet detection, the items are checked against the familiar dangerous and malicious items. These include IP addresses, URLs, executable binaries. The entire procedure can be quite fast if the list of the items is up to date and accurate. This process of identifying the bad items is relatively risk free. However, when it comes to practice, performing only static analysis is not a helpful way of maintaining a botnet free network. This is due to the fact that the developers of malware are continuously creating threats that are completely undetected. The developers use different types of techniques in order to avoid getting detected by the security researchers and antivirus tools. These techniques are: Methods of URL obfuscation Polymorphism Changing the IP addresses at a fast rate Using lots of URLs which ultimately connect to a particular resource. Serving various web pages or downloads B- Behavioral analysis This is really a powerful method of botnet detection. However, it requires a suitable environment for observing the behavior of the computer and there is a risk of the false positives that can make the process of diagnosis more difficult. The procedure can get more complicated if certain malware do not run. Once it was often seen bots attempting connection in every port of the target computers in a sequence. This helped the target computer in easily recognizing an attacker. Now most of the bots spread by using targeted attacks. Some parts are examined by them. This generally involves the ports which are used by another service. There are several preventive measures that you can take for getting rid of a botnet. 8
- 10. 9 Botnet Detection www.ZIANEBilal.com C- OURMON and Botnet Detection Ourmon is an open source, UNIX based tool, Designed for network packet sniffing and port monitoring. Ourmon has two parts: 1. The FRONT-END for sniffing packets. 2. The BACK-END for log entries and ASCII reports. How can be used to detect Botnet? By collecting IRC information using its IRC module and the TCP report to figure out if the IRC channel is a botnet. http://sourceforge.net/projects/ourmon/ http://ourmon.sourceforge.net/ How to ensure the computer is safe from the botnet attacks? Install a firewall and keep it ON. Install good quality AV software, with a regular update. Install some kind of intrusion detection software in the computer that will informe you if you are under any attack from other networks. Install Botnet removal software, many of them available for free out there. 9
- 11. 10 Resources www.ZIANEBilal.com 7- Resources • Know your Enemy: Tracking Botnets: http://www.honeynet.org/book/export/html/50 • The history of the botnet: http://countermeasures.trendmicro.eu/the-history-of- the-botnet-part-i/ • Attack of the Bots: http://www.wired.com/wired/archive/14.11/botnet_pr.html • Storm botnet: http://en.wikipedia.org/wiki/Storm_botnet • Good botnets to take on the bad boys: http://www.pcpro.co.uk/news/191040/good-botnets-to-take-on-the-bad-boys • America's 10 most wanted botnets: http://www.networkworld.com/news/2009/072209-botnets.htm • Anomaly-Based Botnet server detection: http://web.cecs.pdx.edu/~jrb/jrb.papers/flocon/flocon.pdf 10
- 12. 11 Resources www.ZIANEBilal.com Contents 1- Definition of a Botnet ..................................................................................................................2 2- Attacking Behavior of Botnets ......................................................................................................3 3- Types of Botnets .........................................................................................................................4 4- Botnet topologies........................................................................................................................5 5- Example of well-known Botnets ...................................................................................................7 6- Botnet Detection.........................................................................................................................8 7- Resources ................................................................................................................................. 10 11
