Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
•
0 gostou•445 visualizações
In Q3 2013, malicious actors shifted to reflection and amplification (DrDoS) attacks to launch more powerful DDoS attacks with fewer resources. This graphical analysis of attacks against Prolexic’s global client base showed an increase in reflection attacks and UDP floods and a decline in the use of SYN floods.
Denunciar
Compartilhar
Denunciar
Compartilhar
Baixar para ler offline
Recomendados
Recomendados
Mais conteúdo relacionado
Semelhante a Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
Semelhante a Q3 2013 Global DDoS Attacks | DDoS Attack Statistics (14)
Industry Insights & Cloud Skeptics - How Enterprises Use The Cloud And What S...

Industry Insights & Cloud Skeptics - How Enterprises Use The Cloud And What S...
SecurityGen-whitepaper-gtp-firewall- security 5G.pdf

SecurityGen-whitepaper-gtp-firewall- security 5G.pdf
SecurityGen whitepaper GTP vulnerabilities - A cause for concern in 5G and LT...

SecurityGen whitepaper GTP vulnerabilities - A cause for concern in 5G and LT...
SecurityGen Sentinel - Your User-Friendly Guardian in Telecom Security.pdf

SecurityGen Sentinel - Your User-Friendly Guardian in Telecom Security.pdf
Secure Your Network with Confidence Understanding - GTP Protocols by Security...

Secure Your Network with Confidence Understanding - GTP Protocols by Security...
FLOODING ATTACK DETECTION AND MITIGATION IN SDN WITH MODIFIED ADAPTIVE THRESH...

FLOODING ATTACK DETECTION AND MITIGATION IN SDN WITH MODIFIED ADAPTIVE THRESH...
Scaling service provider business with DDoS-mitigation-as-a-service

Scaling service provider business with DDoS-mitigation-as-a-service
DDoS Threats Landscape : Countering Large-scale DDoS attacks

DDoS Threats Landscape : Countering Large-scale DDoS attacks
DDoS Threat Landscape - Challenges faced by Network Operators

DDoS Threat Landscape - Challenges faced by Network Operators
Cloud service providers survey breaking through the cloud adoption barriers- ...

Cloud service providers survey breaking through the cloud adoption barriers- ...
Último
Último (20)
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
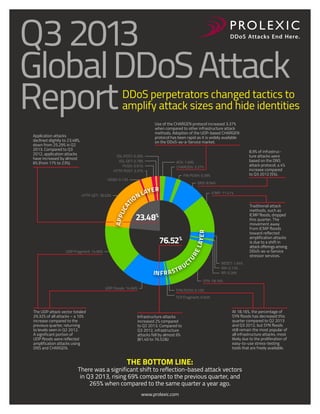
- 1. Q3 2013 Global DDoS Attack Report DDoS perpetrators changed tactics to amplify attack sizes and hide identities Use of the CHARGEN protocol increased 3.37% when compared to other infrastructure attack methods. Adoption of the UDP-based CHARGEN protocol has been rapid as it is widely available on the DDoS-as-a-Service market. Application attacks declined slightly to 23.48%, down from 25.29% in Q2 2013. Compared to Q3 2012, application attacks have increased by almost 6% (from 17% to 23%). SSL POST: 0.26% SSL GET: 0.78% PUSH: 0.91% HTTP POST: 3.37% ACK: 1.69% CHARGEN: 3.37% FIN PUSH: 0.39% HEAD: 0.13% N IO DNS: 8.94% ER LAY ICMP: 11.41% Traditional attack methods, such as ICMP floods, dropped this quarter. The movement away from ICMP floods toward reflected amplification attacks is due to a shift in attack offerings among DDoS-as-a-Service stressor services. 23.48% R APP LIC AT HTTP GET: 18.03% 8.9% of infrastructure attacks were based on the DNS attack protocol, a 4% increase compared to Q3 2012 (5%). L AY E 76.52% TU RE UDP Fragment: 14.66% IN F R A U ST R C RESET: 1.94% RIP: 0.13% RP: 0.39% SYN: 18.16% UDP Floods: 14.66% SYN PUSH: 0.13% TCP Fragment: 0.65% The UDP attack vector totaled 29.32% of all attacks – a 10% increase compared to the previous quarter, returning to levels seen in Q2 2012. A significant portion of UDP floods were reflected amplification attacks using DNS and CHARGEN. Infrastructure attacks increased 2% compared to Q2 2013. Compared to Q3 2012, infrastructure attacks fell by almost 6% (81.40 to 76.52&) THE BOTTOM LINE: At 18.16%, the percentage of SYN floods has decreased this quarter compared to Q2 2013 and Q3 2012, but SYN floods still remain the most popular of all infrastructure attacks, most likely due to the proliferation of easy-to-use stress-testing tools that are freely available. There was a significant shift to reflection-based attack vectors in Q3 2013, rising 69% compared to the previous quarter, and 265% when compared to the same quarter a year ago. www.prolexic.com