Report
Share
Download to read offline
Recommended
JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"

JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"PAPN (Pôle d'Accompagnement à la Pédagogie Numérique)
Livre blanc mobile-learning by IL&DI http://il-di.com

Livre blanc mobile-learning by IL&DI http://il-di.comIL-DI - International Learning and Development Institute
E-learning pour la formation des formateurs. De la conception à l’implémentat...

E-learning pour la formation des formateurs. De la conception à l’implémentat...eraser Juan José Calderón
Recommended
JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"

JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"PAPN (Pôle d'Accompagnement à la Pédagogie Numérique)
Livre blanc mobile-learning by IL&DI http://il-di.com

Livre blanc mobile-learning by IL&DI http://il-di.comIL-DI - International Learning and Development Institute
E-learning pour la formation des formateurs. De la conception à l’implémentat...

E-learning pour la formation des formateurs. De la conception à l’implémentat...eraser Juan José Calderón
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
More Related Content
More from State of the Internet
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
More from State of the Internet (8)
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation
Q3 2013 Global DDoS Attacks | DDoS Attack Statistics

Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
Recently uploaded
Recently uploaded (20)
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi

FULL ENJOY 🔝 8264348440 🔝 Call Girls in Diplomatic Enclave | Delhi
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Enhancing Worker Digital Experience: A Hands-on Workshop for Partners

Enhancing Worker Digital Experience: A Hands-on Workshop for Partners
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...

Neo4j - How KGs are shaping the future of Generative AI at AWS Summit London ...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation

Beyond Boundaries: Leveraging No-Code Solutions for Industry Innovation
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
The Codex of Business Writing Software for Real-World Solutions 2.pptx

The Codex of Business Writing Software for Real-World Solutions 2.pptx
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
Fingerprinting a DDoS Attack
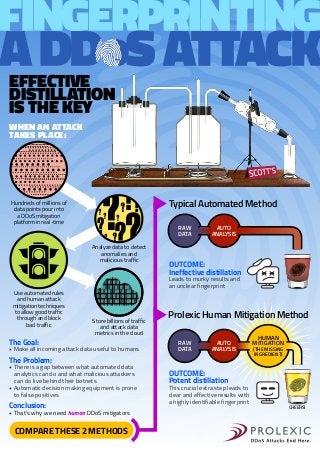
- 1. EFFECTIVE DISTILLATION IS THE KEY WHEN AN ATTACK TAKES PLACE: Hundreds of millions of data points pour into a DDoS mitigation platform in real-time ?? ??? ? ?? ? ? ? ? Analyze data to detect anomalies and malicious traffic Use automated rules and human attack mitigation techniques to allow good traffic through and block bad traffic The Goal: 101101010001010100011 010100110101001110011 101010011010101001100 101010100110010100101 101010010101010100101 010100101010011100010 101010100101001110101 Store billions of traffic and attack data metrics in the cloud • Make all incoming attack data useful to humans Typical Automated Method RAW DATA AUTO ANALYSIS OUTCOME: Ineffective distillation Leads to murky results and an unclear fingerprint Prolexic Human Mitigation Method RAW DATA AUTO ANALYSIS The Problem: • There is a gap between what automated data analytics can do and what malicious attackers can do live behind their botnets • Automatic decision making equipment is prone to false positives Conclusion: • That’s why we need human DDoS mitigators COMPARE THESE 2 METHODS HUMAN MITIGATION (THE MISSING INGREDIENT) OUTCOME: Potent distillation This crucial extra step leads to clear and effective results with a highly identifiable fingerprint CHEERS!