Mobile Security: Perception vs Reality
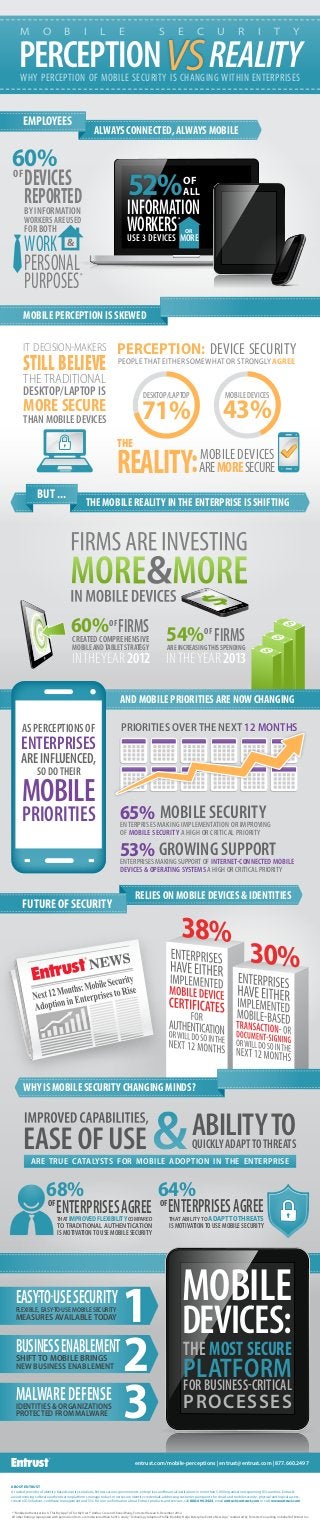
- 1. EMPLOYEES ALWAYS CONNECTED, ALWAYS MOBILE AND MOBILE PRIORITIES ARE NOW CHANGING INFORMATION WORKERS 52%OF ALL USE 3 DEVICES OR MORE * INTHEYEAR 2013 OF FIRMS54%AREINCREASINGTHISSPENDING INTHEYEAR 2012 OF FIRMS60%CREATED COMPREHENSIVE MOBILEANDTABLETSTRATEGY OF & * DEVICES REPORTED 60% BY INFORMATION WORKERS ARE USED FOR BOTH PERSONAL PURPOSES WORK DESKTOP/LAPTOP 71% MOBILE DEVICES 43% PEOPLE THAT EITHER SOMEWHAT OR STRONGLY AGREE PERCEPTION: DEVICE SECURITY THE MOBILE REALITY INTHE ENTERPRISE IS SHIFTING BUT ... MOBILE SECURITY65%ENTERPRISES MAKING IMPLEMENTATION OR IMPROVING OF MOBILE SECURITY A HIGH OR CRITICAL PRIORITY GROWING SUPPORT53%ENTERPRISES MAKING SUPPORT OF INTERNET-CONNECTED MOBILE DEVICES & OPERATING SYSTEMS A HIGH OR CRITICAL PRIORITY ASPERCEPTIONSOF ENTERPRISES AREINFLUENCED, SO DOTHEIR MOBILE PRIORITIES FUTURE OF SECURITY RELIES ON MOBILE DEVICES & IDENTITIES WHY IS MOBILE SECURITY CHANGING MINDS? ABILITYTOQUICKLYADAPTTOTHREATS ARE TRUE CATALYSTS FOR MOBILE ADOPTION IN THE ENTERPRISE OF ENTERPRISESAGREE 68% THATIMPROVEDFLEXIBILITYCOMPARED TO TRADITIONAL AUTHENTICATION IS MOTIVATIONTO USE MOBILE SECURITY OF ENTERPRISESAGREE 64% THAT ABILITYTO ADAPTTOTHREATS IS MOTIVATIONTO USE MOBILE SECURITY VSPERCEPTIONWHY PERCEPTION OF MOBILE SECURITY IS CHANGING WITHIN ENTERPRISES M O B I L E S E C U R I T Y REALITY THE REALITY:MOBILE DEVICES AREMORESECURE IT DECISION-MAKERS STILL BELIEVE THE TRADITIONAL DESKTOP/LAPTOP IS MORE SECURE THAN MOBILE DEVICES MOBILE PERCEPTION IS SKEWED PRIORITIES OVER THE NEXT 12 MONTHS ABOUT ENTRUST A trusted provider of identity-based security solutions, Entrust secures governments, enterprises and financial institutions in more than 5,000 organizations spanning 85 countries. Entrust’s award-winning software authentication platforms manage today’s most secure identity credentials, addressing customer pain points for cloud and mobile security, physical and logical access, citizen eID initiatives, certificate management and SSL. For more information about Entrust products and services, call 888-690-2424, email entrust@entrust.com or visit www.entrust.com. * “Mobile Authentication: Is This My App? Is This My User?”Andras Cser and Chenxi Wang, Forrester Research, December 2012. All other findings repurposed with permission from a commissioned March 2013 study,“Technology Adoption Profile: Mobility Helps Enterprise Enter a New Age,”conducted by Forrester Consulting on behalf of Entrust Inc. THE MOST SECURE PLATFORM FOR BUSINESS-CRITICAL PROCESSES MOBILE DEVICES: entrust.com/mobile-perceptions | entrust@entrust.com | 877.660.2497 EASY-TO-USESECURITYFLEXIBLE, EASY-TO-USE MOBILE SECURITY MEASURES AVAILABLE TODAY 1 BUSINESSENABLEMENTSHIFT TO MOBILE BRINGS NEW BUSINESS ENABLEMENT 2 MALWAREDEFENSEIDENTITIES & ORGANIZATIONS PROTECTED FROM MALWARE 3
