Ernst & Young visuals security survey 2012
•Transferir como PPTX, PDF•
0 gostou•446 visualizações
Risk and Security not always aligned. Not enough non IT focus on security. Hardly surprising that organisational Information Security needs are not being met in enough organisations.
Denunciar
Compartilhar
Denunciar
Compartilhar
Recomendados
Mais conteúdo relacionado
Mais procurados
Mais procurados (20)
Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?

Sécurité Mobile : Votre Entreprise est-elle préparée pour 2020?
Understanding the Data & Analytics Specific Purchase Process [Infographic]![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![Understanding the Data & Analytics Specific Purchase Process [Infographic]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
Understanding the Data & Analytics Specific Purchase Process [Infographic]
The Cyber Security Readiness of Canadian Organizations

The Cyber Security Readiness of Canadian Organizations
Executive Summary of the 2016 Scalar Security Study

Executive Summary of the 2016 Scalar Security Study
SVB Cybersecurity Impact on Innovation Report - Overview

SVB Cybersecurity Impact on Innovation Report - Overview
2017 Role & Influence of the Technology Decision-Maker

2017 Role & Influence of the Technology Decision-Maker
How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs

How to Connect Your Server Room to the Board Room – Before a Data Breach Occurs
Destaque (18)
Semelhante a Ernst & Young visuals security survey 2012
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attentionRamón Gómez de Olea y Bustinza
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attentionRamón Gómez de Olea y Bustinza
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...Hewlett Packard Enterprise Business Value Exchange
2014 Executive Breach Preparedness Research Report

2014 Executive Breach Preparedness Research ReportHewlett Packard Enterprise Business Value Exchange
ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...

ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...Enterprise Strategy Group
5 Questions Executives Should Be Asking Their Security Teams 

5 Questions Executives Should Be Asking Their Security Teams Arun Chinnaraju MBA, PMP, CSM, CSPO, SA
Semelhante a Ernst & Young visuals security survey 2012 (20)
Cyber security: five leadership issues worthy of Board and executive attention

Cyber security: five leadership issues worthy of Board and executive attention
Cyber security: Five leadership issues worthy of board and executive attention

Cyber security: Five leadership issues worthy of board and executive attention
Build a Business-Driven IT Risk Management Program

Build a Business-Driven IT Risk Management Program
Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...

Breaches Are Bad for Business. How Will You Detect and Respond to Your Next C...
2014 Executive Breach Preparedness Research Report

2014 Executive Breach Preparedness Research Report
Insights from the IBM Chief Information Security Officer Assessment

Insights from the IBM Chief Information Security Officer Assessment
Government and Education Webinar: Public Sector Cybersecurity Survey - What I...

Government and Education Webinar: Public Sector Cybersecurity Survey - What I...
01-Build-an-IT-Risk-Management-Program--Phases-1-3.pptx

01-Build-an-IT-Risk-Management-Program--Phases-1-3.pptx
ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...

ESG TechTruth: Advanced Persistent Threat: The Pervasive IT Security Skills S...
Cyber Security in the Digital Age: A Survey and its Analysis

Cyber Security in the Digital Age: A Survey and its Analysis
5 Questions Executives Should Be Asking Their Security Teams 

5 Questions Executives Should Be Asking Their Security Teams
Accenture 2015 Global Risk Management Study: Insurance Report Key Findings an...

Accenture 2015 Global Risk Management Study: Insurance Report Key Findings an...
Último
Último (20)
Digital Identity is Under Attack: FIDO Paris Seminar.pptx

Digital Identity is Under Attack: FIDO Paris Seminar.pptx
Streamlining Python Development: A Guide to a Modern Project Setup

Streamlining Python Development: A Guide to a Modern Project Setup
Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024

Transcript: New from BookNet Canada for 2024: BNC CataList - Tech Forum 2024
Take control of your SAP testing with UiPath Test Suite

Take control of your SAP testing with UiPath Test Suite
The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx

The Fit for Passkeys for Employee and Consumer Sign-ins: FIDO Paris Seminar.pptx
Unraveling Multimodality with Large Language Models.pdf

Unraveling Multimodality with Large Language Models.pdf
Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)

Tampa BSides - Chef's Tour of Microsoft Security Adoption Framework (SAF)
TrustArc Webinar - How to Build Consumer Trust Through Data Privacy

TrustArc Webinar - How to Build Consumer Trust Through Data Privacy
What's New in Teams Calling, Meetings and Devices March 2024

What's New in Teams Calling, Meetings and Devices March 2024
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
Gen AI in Business - Global Trends Report 2024.pdf

Gen AI in Business - Global Trends Report 2024.pdf
Dev Dives: Streamline document processing with UiPath Studio Web

Dev Dives: Streamline document processing with UiPath Studio Web
DSPy a system for AI to Write Prompts and Do Fine Tuning

DSPy a system for AI to Write Prompts and Do Fine Tuning
Ernst & Young visuals security survey 2012
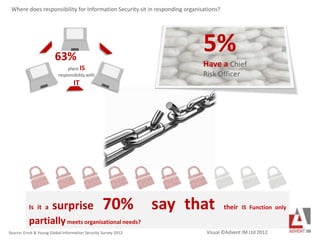
- 1. 63% place IS responsibility with IT 5% Have a Chief Risk Officer Source: Ernst & Young Global Information Security Survey 2012 Where does responsibility for Information Security sit in responding organisations? Is it a surprise 70% say that their IS Function only partiallymeets organisational needs? Visual ©Advent IM Ltd 2012
- 2. 46% neveror almost never discuss Information Security at top governing structure of their organisation 56% 42% 38% aligned to IT Strategyaligned to Business Strategyaligned to Risk Appetit how is Information Security aligned in your organisation?
- 3. planned spend increase of 5-15% planned spend increase of 25% or more With so little boardroom involvement and so little specialist security resourcing, how will any additional spending be effectively appropriately controlled?
- 4. 63% place IS responsibility with IT 5% Have a Chief Risk Officer Source: Ernst & Young Global Information Security Survey 2012 Where does responsibility for Information Security sit in responding organisations? Is it a surprise 70% say that their IS Function only partiallymeets organisational needs?
